Host : Management Server(SMS)
OS : R80.40
Port:8211
Vulnerability_ID :ssl-weak-message-authentication-code-algorithms
Vulnerability_NAME : TLS/SSL Weak Message Authentication Code Cipher Suites
Vulnerability_Proof: Negotiated with the following insecure cipher suites: * TLS 1.2 ciphers: * TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA * TLS_RSA_WITH_AES_128_CBC_SHA
Vulnerability_Solution: Disable any weak HMAC algorithms within the TLS configurationThe following recommended configuration provides a higher level of security. This configuration is compatible with Firefox 27; Chrome 22; IE 11; Opera 17 and Safari 9. SSLv2; SSLv3; TLSv1 and TLSv1.1 protocols are not recommended in this configuration. Instead use TLSv1.2 protocol.Refer to your server vendor documentation to apply the recommended cipher configuration:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!3DES:!MD5:!PSK:!SHA1:!DSS
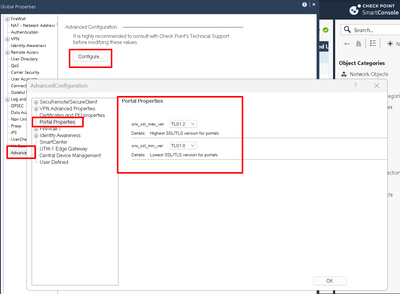
Port 8211 uses TLS 1.2 .Attached file for reference.
We have checked the sshd.config file httpd all looks fine . Can you please let us know what needs to be tweaked here?