- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- VRRP Issue - Interface stuck in Init State
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
VRRP Issue - Interface stuck in Init State
Hi Experts,
We upgraded RAM in one of our 4800 cluster , post-firewall reboot we noticed one of the interafce on standby member is in VRRP initialize state.
We do see the arp entry of the active member on the standby member of that interface but don't see the arp entry of the standby member on the active member for the interface in the init state.
We have done the following workaround to mitigate this:
- We noticed that the virtual IP was changed automatically to the physical IP) which was later corrected.
- Hotfix upgraded
- Manual ARP entry added on active member
- Anti Spoofing disabled/enabled on the cluster
- Firewall rebooted
- Removing/adding interface from VRRP cluster.
- Tried changing the Switch port which is connected to Stanby member interface.
- The network team confirmed they are receiving Mac address for the standby interface on the switch end.
Further Analysis.
- Stanby member interface eth1-01.xxxx is in vrrp initialize state however on active memebr interface eth1-01.xxxx is in master state.
- We unable to ping the active member interface from standby firewall and vice versa .
- Able to receive the arp entries on stanby member however we are not receiving arp entries from standby on active member
- All other sub-interfaces are working perfectly fine.
- Ideally, the route for the interface on standby firewall should be directly connected(same as on active member and other interfaces ) however the best route is default route.
- As per ASP drop logs, active member is dropping packets for stnaby member due to local anti spoofing . the main reason is active memeber has no entry in its arp table.
- As per tcpdump logs on active member when we are trying to ping the remote end IP , its is getting ICMP echo message but it is not replying.
Is there something we are missing and what can bee done to resolve the issue. ?
Regards
Sijeel
14 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Sijeel,
Just so we can get better idea, can you please send below outputs from BOTH members?
Andy
cphaprob state
cphaprob -a if
cphaprob list
cphaprob syncstat
cphaprob roles
cphaprob tablestat
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Andy,
Please find the output. I have also added output for below command
show vrrp summary
show vrrp interface eth1-01.1491 ( Problematic interface on standby)
show route destination 163.166.149.35 (on standby )
show route destination 163.166.149.36 (on active )
show route direct
Regards,
Sijeel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have a call in 10 mins, but I quickly reviewed show interface command for problematic one and vmac and IDs looks correct to me. This happened AFTER upgrade you said?
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you also please send topology config, SPECIFICALLY for problematic interface? Please blur out any sensitive data.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
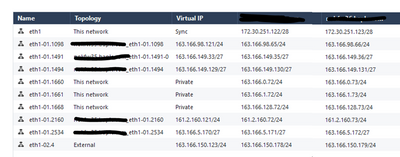
Please find the topology
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks, but I more meant topology properties ONLY for interface you have issue with, if you double click on it. I think it would also be worth to contact TAC, so they can do remote session and see whats going on.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi .
Please find the details , it been 2 months my team has raised a case with TAC but they arent able to identify the issue,
Do u have any idea what can be an issue as the connected route is not showing in the routing table? what could be a reason for such an issue,The link status is up for the interface
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Im really not sure, as looking at your screenshots, all seems correct to me. If TAC case has been ongoing for 2 months, did they at least escalate it? Sounds way too long for an issue like this...if connected route is missing, tells me something with the interface is wrong, since its not static route, cant be added manually. What steps did TAC provide you so far?
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
the rest of the sub interfaces are fine the issue is with this interafce. if this was ab issue with the physical interface then we would have faced the issue with all the sub-interfaces
.TAC has taken dumps , asked to update HF . Below steps have been done till now.
- We have noticed that virtual IP 163.166.149.33 was changed automatically to 163.166.149.36(physical IP) which was later corrected .
- Hotfix upgraded
- Manual ARP entry added on NOKFW35
- Anti Spoofing disabled/enabled on cluster
- Firewall rebooted
- Removing/adding interface eth1-01.1491 from VRRP cluster.
- Tried with changing Switch port which is connected with NOKFW36 eth1-01 interface .
- Network team confirmed they are receiving mac address for vlan 1491 on the switch end.
As per zdebug NOKFW35 is dropping packets for 163.166.149.36 due to local local spoofing (screenshot attached)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
-
Anti-Spoofing drops indicate that the source IP address of the packet received on a certain interface is not a part of the defined interface's topology.
-
Local interface address spoofing drops indicate that the Security Gateway / Cluster member received a packet with a source IP address that belongs to one of the local interfaces on the Security Gateway / Cluster member.
https://support.checkpoint.com/results/sk/sk115276
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What type of NIC card is populated in the expansion slot?
Anything odd in /var/log/messages ?
Can you please confirm the version & jumbo that this gateway/cluster is installed with?
(Note 4800 appliances are no longer supported).
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Chris,
R80.40 +take 180 is installed . I dont see any odd messages also, the rest of the logical interfaces on the physical port are working fine. the issue is with 1 logical interface.
Line card model : CPAP-4-1F Type 4 ports 1 gbe sfp
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
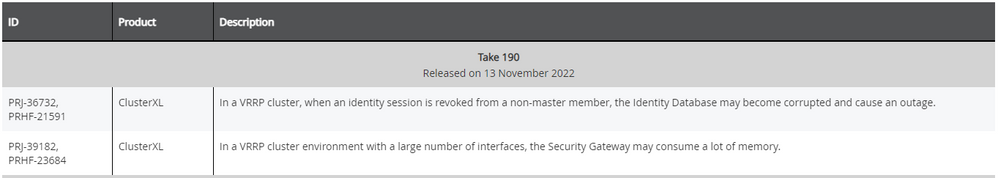
Note Take 196 is the current recommended release and includes the following VRRP fixes for awareness.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey @Malik1 ,
I think, as always, @Chris_Atkinson brings up a good point. To add to what he said, I would strongly consider also upgrade to R81.10, jumbo 94, if you can, as its super stable.
Not sure if TAC made that recommendation yet.
Andy
Best,
Andy
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 14 | |
| 9 | |
| 9 | |
| 9 | |
| 6 | |
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 2 |
Upcoming Events
Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter