- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
10 December @ 5pm CET / 11am ET
Announcing Quantum R82.10!
Learn MoreOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: Trusted CA List is missing a lot
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Trusted CA List is missing a lot
Hello Mates!
I am currently working to enable HTTPS Inspection for a customer. After configuring the basics (CA cert import, basic ruleset, Manual Update of Trusted CA List), we enabled the Inspection for a testing Host and noticed that a lot of URLs were still causing Warnings in the browser about the connection not beeing secure.
After checking the logs, I noticed that there were a lot of logs for the Inspection Blade showing "action: Detect" and "HTTPS Validation: Untrusted Certificate"
I did a manual update of the Trusted CA List before, so I was a bit surprised to see that things were still missing there. After checking all the URLs used for testing and what certs they use, I started importing the missing certs one by one. That is a lot of manual work and when I look at what certs were missing there, I get the impression that I did somethign wrong, or missed something, as I would have thought that the List provided from Check Point would contain popular and often used CA certs like "Amazon Root CAx" , the main Microsoft Azure root CAs, DigiCert root CAs or Let's Encrypt CAs for example.
I imported around 12 certs manually now but still see a lot of "Untrusted Certificate" warnings in the Logs. This is only for one Host so far that I used for testing. I can only imagine what would have happened if we would have activated this for a bigger number of users right away.
So my questions abnout this:
1. Did I miss something here or is it really expected behaviour? Is it really required for using HTTPS Inspection to check a lot of URLs for certs and import a lot of certs manually??
2. I suspect the manually imported certificates will also not be updated automatically, so is it required to regular check this list for outdated manually imported certs?
Any Tips that help with this are welcome!
Best Regards,
Alex
12 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What version is this Alex? I can send you updated R81.20 list if you like.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Its R81.10 in this case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
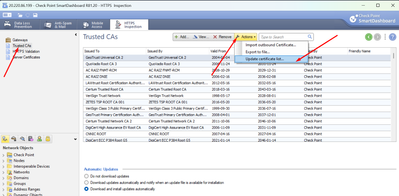
K, great. I attached most updated CA list from R81.20 and all you would need to do is upload the file as per below. Now, I gave it to folks on here before and it never caused any issues, but just a small disclaimer, keep in mind there is always a small chance it could, just saying : - )
Best,
Andy
From legacy dashboard (where you would import the file)
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you, that could be really helpful and a big time saver.
I still wonder though how this is supposed to be done when there is no one around to provide a better list 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
All you would need to do is upload it, save, push policy, thats it. I cant say for sure it would solve the issue, but I would be shocked if it made it worse.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Kryten,
Importoning CA list will not fix it, i had same problem on other customers.
Try this: select all CA in list (select the first one and shift+click mouse until the latest on list) and delete all. Don't be scared (save button is needed), the list will be populated with ALL CA this time.
I did onto two customers
Let us know
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Never really heard of that method. I gave updated CA zip file to 5 clients and worked every single time.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In R81.20 and above, this list should get updated by default.
In R81.10, follow the steps here to ensure this is updated automatically: https://support.checkpoint.com/results/sk/sk173629
For other releases, see: https://support.checkpoint.com/results/sk/sk64521
If something is missing in our CA list that should be there, please consult with TAC: https://help.checkpoint.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, Reading the documentation, it shows the trusted CA list is used, but by default, at least on version R81.20 it is downloaded automatically but not installed automatically. My question is: is it always reccomanded to choose the option to download and install automatically? If more decision can be taken based on trusted CA, why the download and install is not performed automatically by default?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It should be default in R81.20 for new installations (may not be the case for ones upgraded from previous releases).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Check this as well. May need to open a case with TAC - https://support.checkpoint.com/results/sk/sk180507
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Funny story about that sk lol. So couple of months ago I was on the phone with customer who had exact same issue and TAC guy gave them the same sk and since Im not a big fan of installing these custom fixes (been there, done that), TAC guy said, well if you have fresh R81.20 mgmt server, you can simply give customer updated zip file from mgmt database folder to upload to their R81.10 server. I spun one up on eve-ng in 10 mins, installed latest jumbo, in 30 mins issue was fixed 🙂
Best,
Andy
Best,
Andy
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 16 | |
| 13 | |
| 8 | |
| 7 | |
| 6 | |
| 4 | |
| 3 | |
| 3 | |
| 2 | |
| 2 |
Upcoming Events
Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter