Hi Everyone,
I have some case that is quite weird, my customer has Security Gateway R80.10 with HF T121 running at the moment.
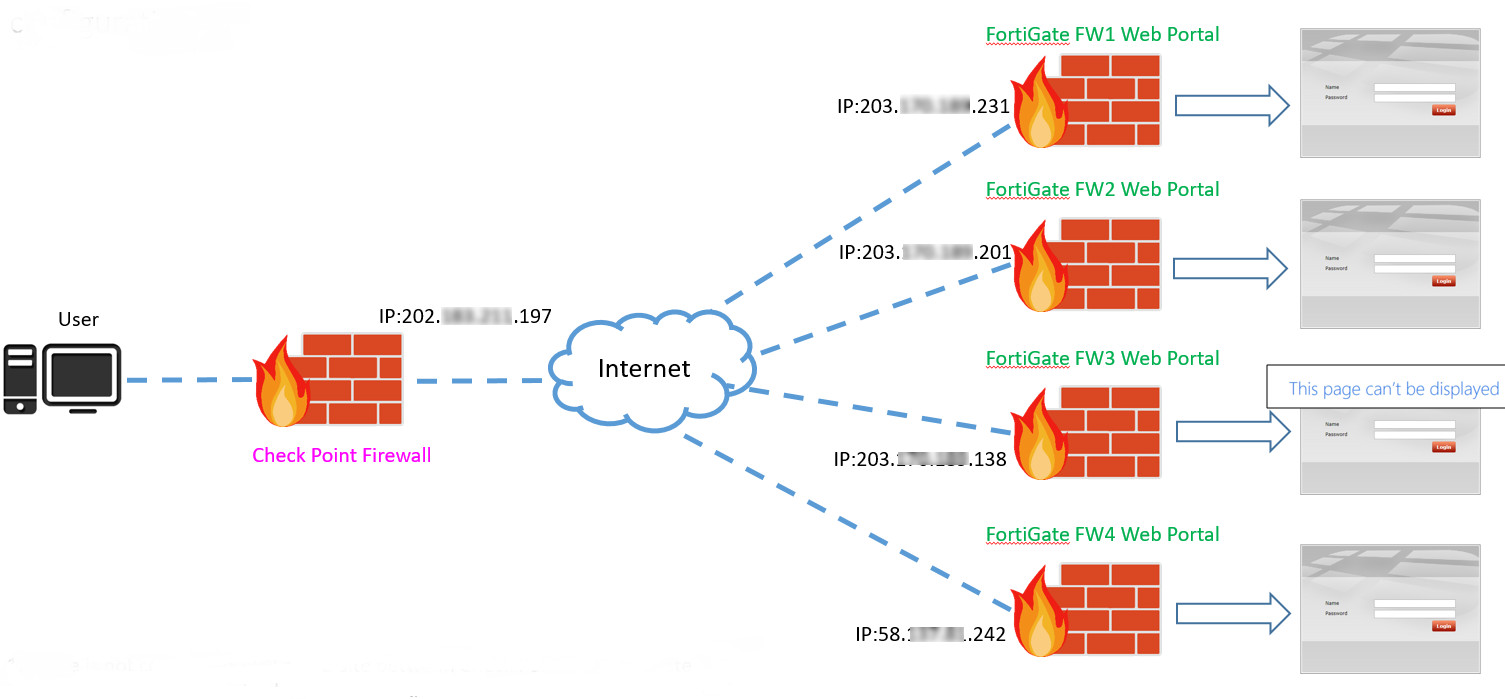
The problem is when users that's behind Check Point does not get access to Public IP Address of Fortigate sometimes.
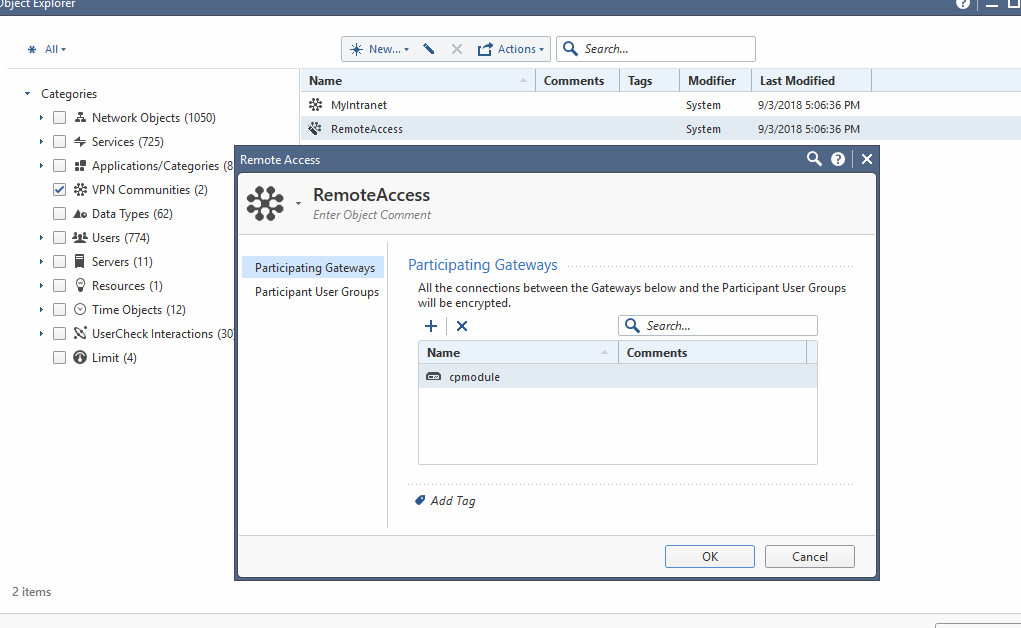
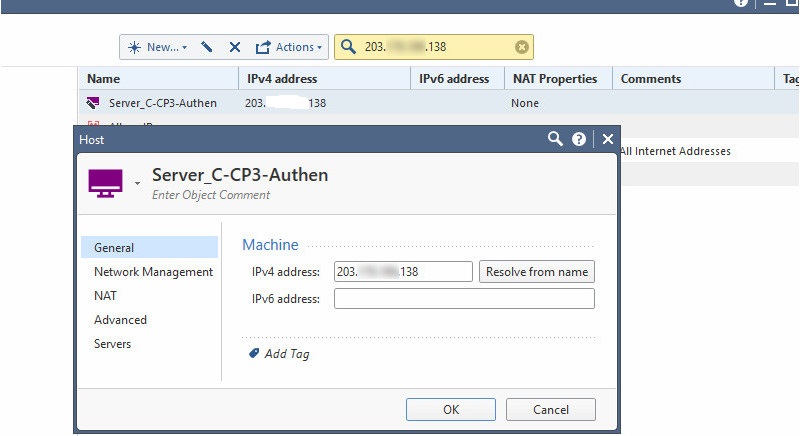
This only happens to Fortigate FW3 ( 203.xxx.xxx.138 ) refer screenshot below and there are no IPSec configuration of both sides
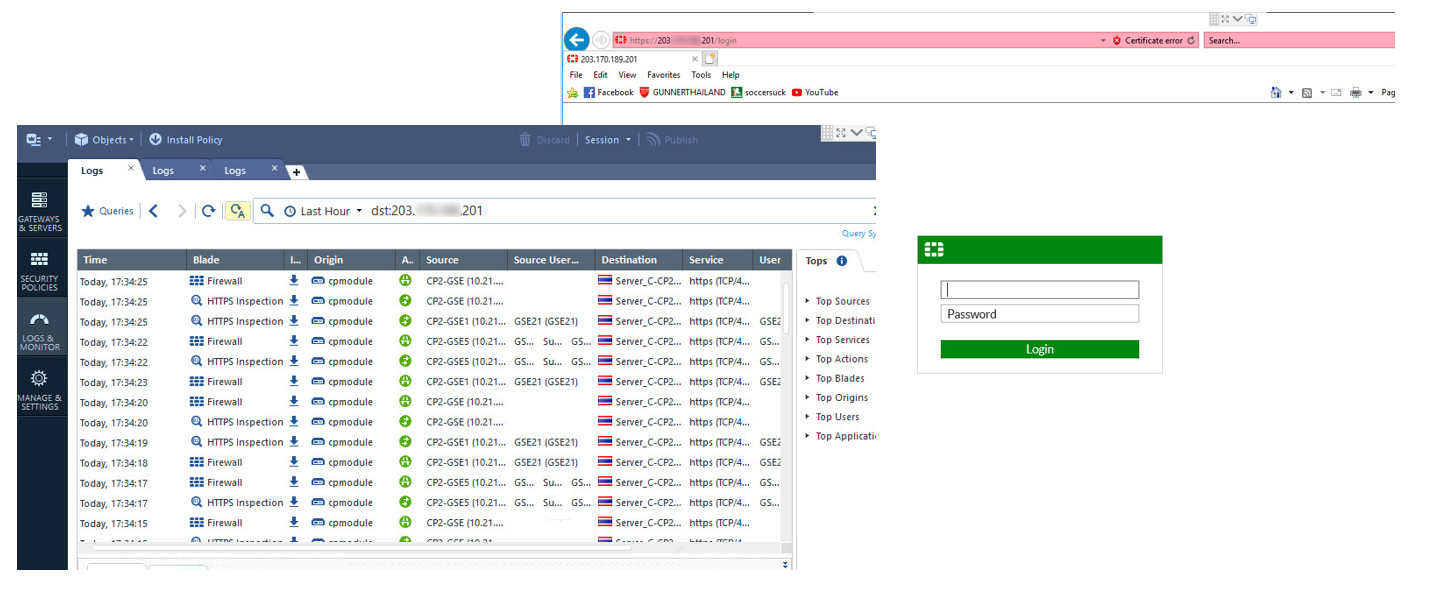
Here is the screenshot if the connectivity is being successfully to destination IP address, look at on column blade is showing firewall and https inspection. We do configure as a bypass for those IP public this is expected behavior
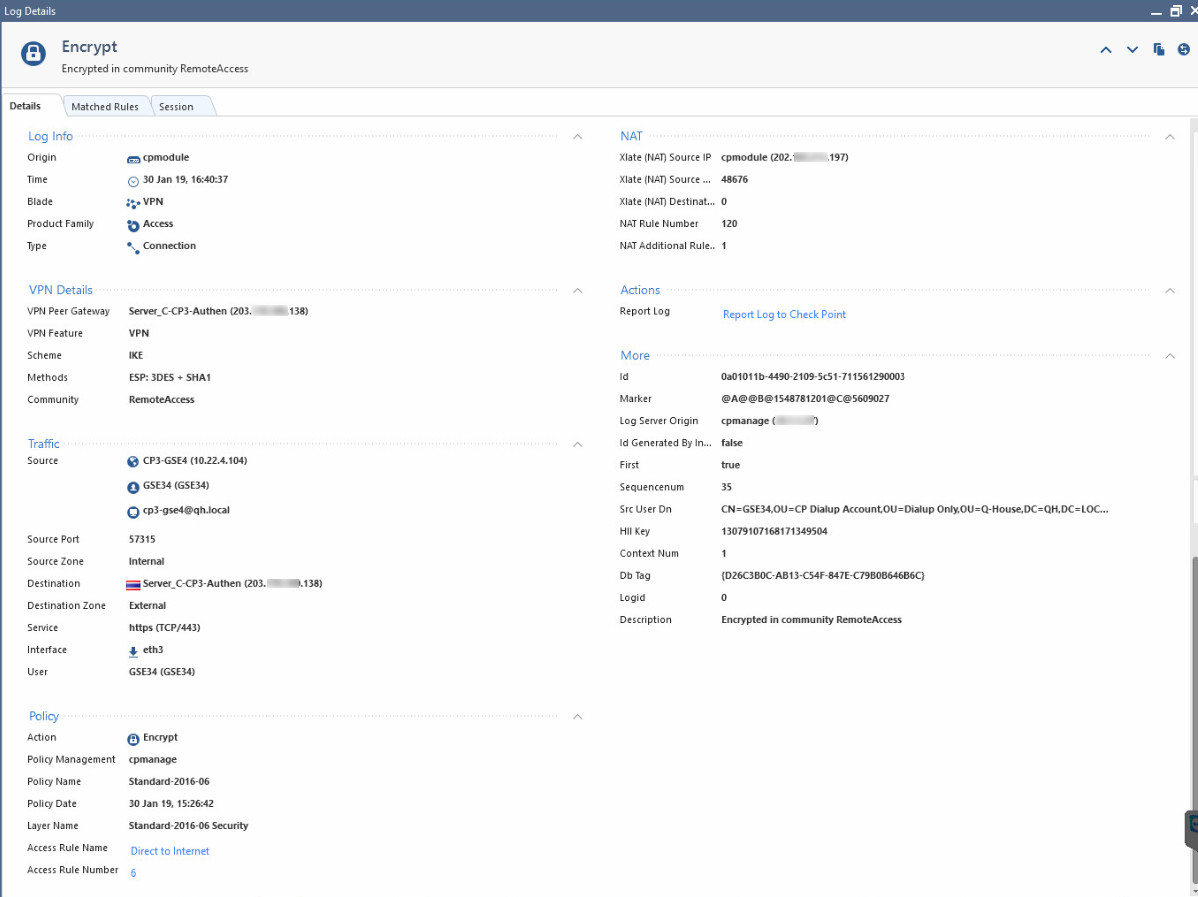
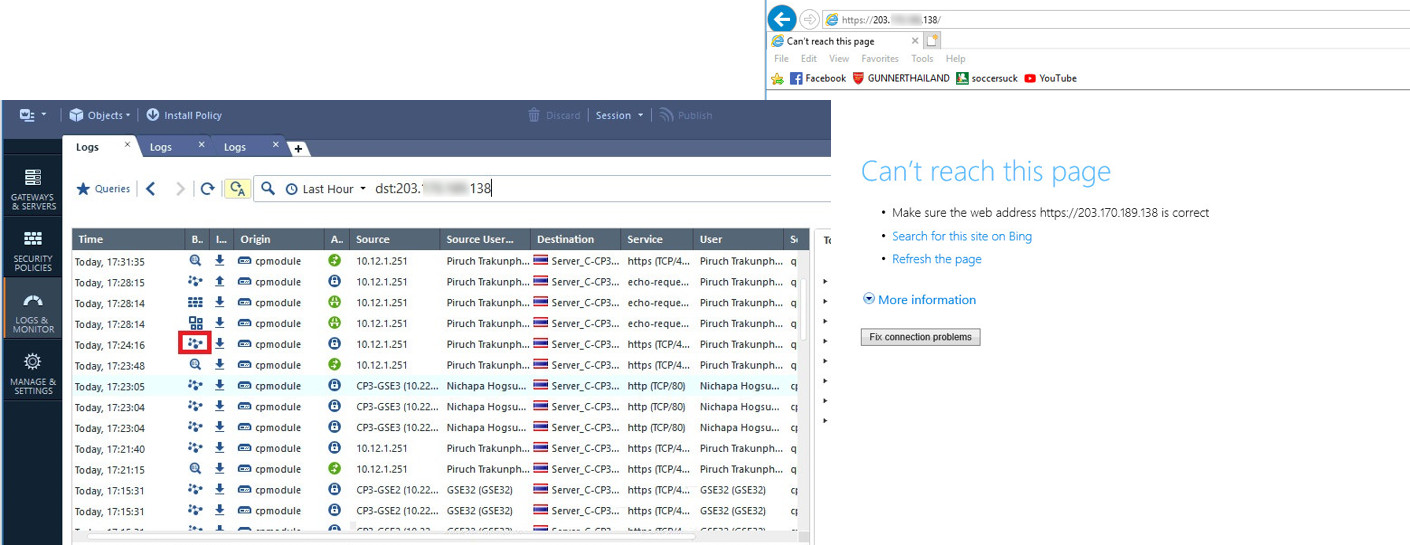
But they sometimes can not get access to that web portal page due to the traffic is redirect to VPN tunnel, look at on column blade is showing VPN blade
This problem happens intermittent without a cause, I have already opened case to TAC but they can not find out something wrong as well
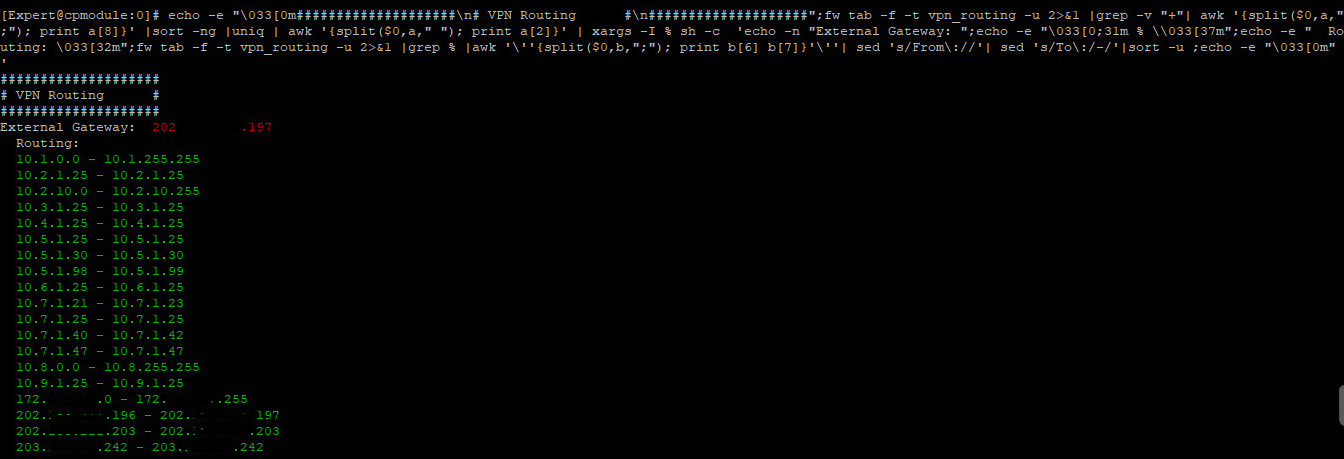
I ran zdebug drop command during the issue was occurring and below is output
[Expert@cpgateway:0]# fw ctl zdebug drop |grep 203.xxx.xxxx.138
;[cpu_1];[fw4_2];fw_log_drop_ex: Packet proto=6 202.xxx.xxx.197:53651 -> 203.xxx.xxx.138:443 dropped by vpn_encrypt_chain Reason: encrypt drop;
;[cpu_1];[fw4_2];fw_log_drop_ex: Packet proto=6 202.xxx.xxx.197:53651 -> 203.xxx.xxx.xxx:443 dropped by vpn_encrypt_chain Reason: encrypt drop;
;[cpu_1];[fw4_2];fw_log_drop_ex: Packet proto=6 202.xxx.xxx.197:53651 -> 203.xxx.xxx.xxx:443 dropped by vpn_encrypt_chain Reason: encrypt drop;
From Access Control Policy, we have configured rule with source to dest and with all any service and https inspection rule with bypass for those Fortigate Public IP
I do not know the root cause of this case, does any one can help or guide me to check more and find the root cause ?
Really appreciate and thanks in advance.
Regards,
Sarm