- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Printernightmare CVE-2021-1675
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Printernightmare CVE-2021-1675
Any IPS protection available for CVE-2021-1675 https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-1675 ?
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The PrintNightmare vulnerabilities (CVE-2021-1675 and CVE-2021-34527) are covered by TE and SBA with the following signatures:
- TE:
- Exploit.Wins.PrintNightmare.A
- SBA:
- HEUR:Trojan-Dropper.Win32.Pegazus.gen
- HEUR:Exploit.Win32.CVE-2021-1675.a
- PDM:Exploit.Win32.Generic
- PDM:Trojan.Win32.Generic
In regards to IPS, at present there is insufficient information to create an IPS protection. We re looking into this and will update once new info is available.
23 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The attack vector is local, according to MS.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That's correct. But this is a problematic vulnerability on most of the Microsoft servers and if they are located in a separated protected LAN there should be a protection.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Let me elaborate. To exploit it, you need to locally execute a file on that server. It is in the endpoint scope, not network.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I think the Print Nightmare nickname is for another bug than cve-2021-1675 and that has not an cve record yet and that is an RCE bug and the only workaround is to disable the print spooler.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
looks like there are exploits out there https://www.youtube.com/watch?v=qU3vQ-B-FPY
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Wolfgang,
I always use SNORT signatures/rules in these cases when there are no manufacturer signatures.
Most of the time you can extract some good ASCII signatures from the exploit code. Then you can create a SNORT signature and import it via the SmartConsole. This is not so easy most of the time but works quite well.
I always try to extract signatures from metasploit,... or other tools.
More information on how to import SNORT signatures can be found here:
https://sc1.checkpoint.com/documents/R81/WebAdminGuides/EN/CP_R81_ThreatPrevention_AdminGuide/Topics...
But as @_Val_ said, in this case the attack vector is local so a Snort signature is useless.
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is there actually a snort signature released for this?
I checked the current IPS database and Checkpoint have not added an signature for this yet, which is not good.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have seen that. POC exploit there is deployed locally on the machine. IPS is not in play
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @_Val_, if this CVE is in endpoint scope, Check Point Harmony Endpoint should be able to detect and protect it, right?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
According to @Pasha_Pal, we're currently evaluating our protection capabilities for this exploit on the Endpoint (and also related CVE-2021-34527).
We'll share more details when available.
In the meantime, it is best to apply the Microsoft patches and disable the print spooler on Domain Controllers and any server not using printing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is there any update to this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The PrintNightmare vulnerabilities (CVE-2021-1675 and CVE-2021-34527) are covered by TE and SBA with the following signatures:
- TE:
- Exploit.Wins.PrintNightmare.A
- SBA:
- HEUR:Trojan-Dropper.Win32.Pegazus.gen
- HEUR:Exploit.Win32.CVE-2021-1675.a
- PDM:Exploit.Win32.Generic
- PDM:Trojan.Win32.Generic
In regards to IPS, at present there is insufficient information to create an IPS protection. We re looking into this and will update once new info is available.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
is there any IPS signature update on 1500 series regarding CVE-2021-34527? I can see this IPS protection on 910 but not in any 1500 fw.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Same signatures should be available on both.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I see, @PhoneBoy beat me to that. In short, theoretically yes, but there is a question of detection, under investigation.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not releasing an IPS signature is not an option - competitors already did so https://www.fortiguard.com/encyclopedia/ips/50553 🙂
I got asked by 2 large clients today already, and it is just Sunday 9+ in the morning.
https://www.linkedin.com/in/yurislobodyanyuk/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Indeed! Trend Micro already released mitigation measures on its network and endpoint IPS solutions as well...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I just got the newsletter: The IPS Pattern has been released
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
From what I can see a signature for CVE-2021-34527 was released today, however I could not see anything for CVE-2021-1675, can you confirm if the news letter indicates anything about 1675? or is this only referencing 34527?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you please share here?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
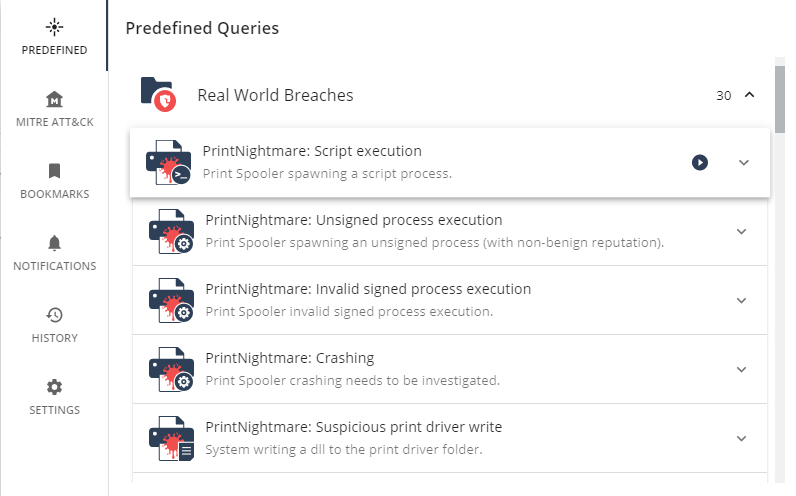
A predefined Threat Hunting query would be cool, something thats checks all servers if the spooler service is running and the system is unpatched.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just check, TH predefined queries were updated with 6 new "Real Word" queries regarding Printnightmare
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 15 | |
| 11 | |
| 6 | |
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 2 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter