- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
Policy Insights and Policy Auditor in Action
19 November @ 5pm CET / 11am ET
Access Control and Threat Prevention Best Practices
Watch HereOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: Packet doesn't leave the FW. It ate my packets...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Packet doesn't leave the FW. It ate my packets!
Need your expertise!
Packet from R80.10 firewall doesn't leave the box?
The FW (its external interface at 10.0.0.111) can ping its default gateway (10.0.0.1) which is behind a NAT going out to the internet. However, the FW can't reach google or ComCast DNS (75.75.75.75 or 8.8.8.8). These IPs are reachable by other host in 10.0.0.0/24 subnet). Traceroute at the FW indicates the packet doesn't leave the box! Did the FW eat the packets? Internal network is ok, I could ssh into the FW.
----
See attached picture for the trouble firewall.....am I missing something?
hoangsa@ubun2svr:~$ ping 8.8.8.8 -c 2
PING 8.8.8.8 (8.8.8.8) 56(84) bytes of data.
64 bytes from 8.8.8.8: icmp_seq=1 ttl=121 time=11.8 ms
64 bytes from 8.8.8.8: icmp_seq=2 ttl=121 time=10.4 ms
--- 8.8.8.8 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1001ms
rtt min/avg/max/mdev = 10.407/11.127/11.848/0.728 ms
hoangsa@ubun2svr:~$ ping 75.75.75.75 -c 2
PING 75.75.75.75 (75.75.75.75) 56(84) bytes of data.
64 bytes from 75.75.75.75: icmp_seq=1 ttl=58 time=10.5 ms
64 bytes from 75.75.75.75: icmp_seq=2 ttl=58 time=9.48 ms
--- 75.75.75.75 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1001ms
rtt min/avg/max/mdev = 9.486/10.041/10.597/0.564 ms
hoangsa@ubun2svr:~$
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did you install the policy after publishing the changes?
15 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
very strange.... able to access the internet only after all rules are removed.
HQ-FW1> fw unloadlocal
Uninstalling Security Policy from all.all@HQ-FW1
Done.
HQ-FW1> fw stat
HOST POLICY DATE
localhost - - - : >eth0 <eth0 >eth1 <eth1 >eth2
HQ-FW1> ping 8.8.8.8 -c 1
PING 8.8.8.8 (8.8.8.8) 56(84) bytes of data.
64 bytes from 8.8.8.8: icmp_seq=1 ttl=121 time=10.5 ms
:::::::.......
HQ-FW1> traceroute 8.8.8.8
traceroute to 8.8.8.8 (8.8.8.8), 30 hops max, 40 byte packets
1 10.0.0.1 (10.0.0.1) 16.733 ms 16.681 ms 16.705 ms
2 96.120.25.229 (96.120.25.229) 26.779 ms 26.769 ms 26.719 ms
3 162.151.173.129 (162.151.173.129) 26.713 ms 26.661 ms 26.685 ms
4 68.86.184.146 (68.86.184.146) 26.540 ms 26.640 ms 26.618 ms
5 be-121-ar01.area4.il.chicago.comcast.net (69.139.203.169) 27.454 ms 27.412 ms 28.348 ms
6 be-33491-cr02.350ecermak.il.ibone.comcast.net (68.86.91.165) 28.307 ms 13.031 ms 39.374 ms
7 be-10563-pe01.350ecermak.il.ibone.comcast.net (68.86.82.158) 30.555 ms 39.274 ms 30.509 ms
8 as15169.350ecermak.il.ibone.comcast.net (75.149.230.110) 39.178 ms 30.349 ms 75.149.230.26 (75.149.230.26) 39.173 ms
9 * * *
10 108.170.233.86 (108.170.233.86) 39.120 ms 216.239.51.144 (216.239.51.144) 30.267 ms 216.239.42.108 (216.239.42.108) 39.041 ms
11 209.85.250.7 (209.85.250.7) 30.730 ms 72.14.235.245 (72.14.235.245) 39.036 ms 108.170.236.101 (108.170.236.101) 39.009 ms
12 google-public-dns-a.google.com (8.8.8.8) 20.045 ms 20.026 ms 19.953 ms
HQ-FW1>
...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
and this is what happened when the policy is re-applied ......... (FW got drunk?)
HQ-FW1> fw fetch 172.16.0.25
Fetching FW1 Security Policy From: 172.16.0.25
Local Policy is Up-To-Date.
Reinstalling Local Policy.
Installing Security Policy Basic-Rules on all.all@HQ-FW1
Using username "admin". <<<< I had to restart ssh session. Rules are re-applied, the prompt is back but not the GUI
This is HQ-FW1. Authorized personnel only.
admin@172.16.0.111's password:
Last login: Sat Sep 22 23:12:16 2018 from 172.16.0.9
HQ-FW1> fw stat
HOST POLICY DATE
localhost Basic-Rules 22Sep2018 23:25:37 : [>eth0] [<eth0] [>eth1] [<eth1] [>eth2]
HQ-FW1>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Matthew Do, there is nothing strange. FW GW is a security device. Policy is important.
Please make sure you apply appropriate policy allowing you require. Also, if this is a newly installed device, check the topology is properly defined, and you have both internal and at least one external interfaces probably defined on FW object.
To see why packets are not forwarded, you ca use "fw ctl zdebug drop | grep <IP in question>" command on cli to understand why packets are dropped.
BTW, I have moved your post into more appropriate area and removed unnecessary tag
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Traffic originating from the firewall itself is a bit of a special case, and must still be allowed in the Firewall/Network Policy Layer by an explicit rule or the implied rule "Accept outgoing packets originating from gateway" since that traffic still passes through inspection points o and O. As Val mentioned topology and antispoofing are enforced as well and must be properly defined. Because traffic originated from the firewall itself does not pass through iI where destination NAT operations occur, it is impossible to NAT the destination address of this type of traffic but the source IP address can most definitely still be NATted. When you unload policy NAT is disabled too, so I suspect you are source NATting traffic originated from the firewall to something the Comcast modem is not expecting. Probably not relevant here, but also keep in mind that traffic originated from the firewall or bound for the firewall itself is never accelerated by SecureXL and will always go F2F.
Please see the slides from my CPX Barcelona/Vegas presentation where I talk about how to troubleshoot what I call the "Roach Motel" situation where packets enter the firewall, but mysteriously disappear (get "eaten") with no logging indication of what happened to them:
--
Second Edition of my "Max Power" Firewall Book
Now Available at http://www.maxpowerfirewalls.com
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
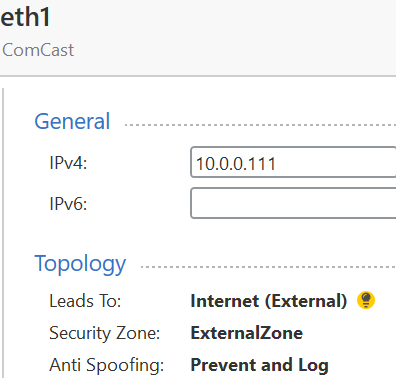
Thank you gentlemen... below is the reason but I don't know how to fix yet. The reason I tried the ping from FW is internal host (172.16.1.22) couldn't ping any thing from the internet although the packet is routed to the FW (172.16.1.111)
The FW ext interface is 10.0.0.111.
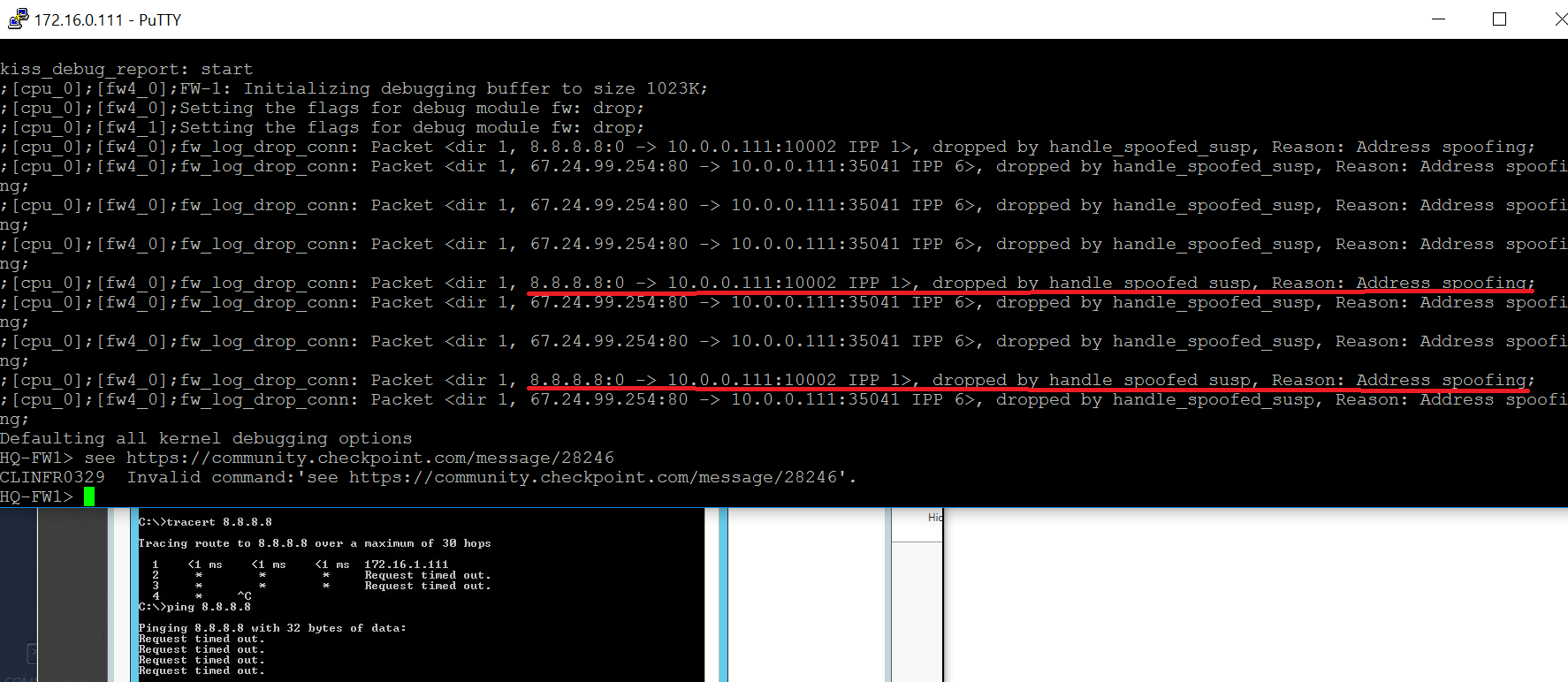
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please see my post above.
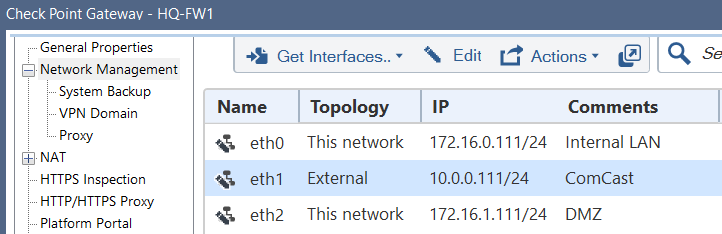
You did not configure your Forewall's topology properly: your External Interface is not defined.
It should look something like this:
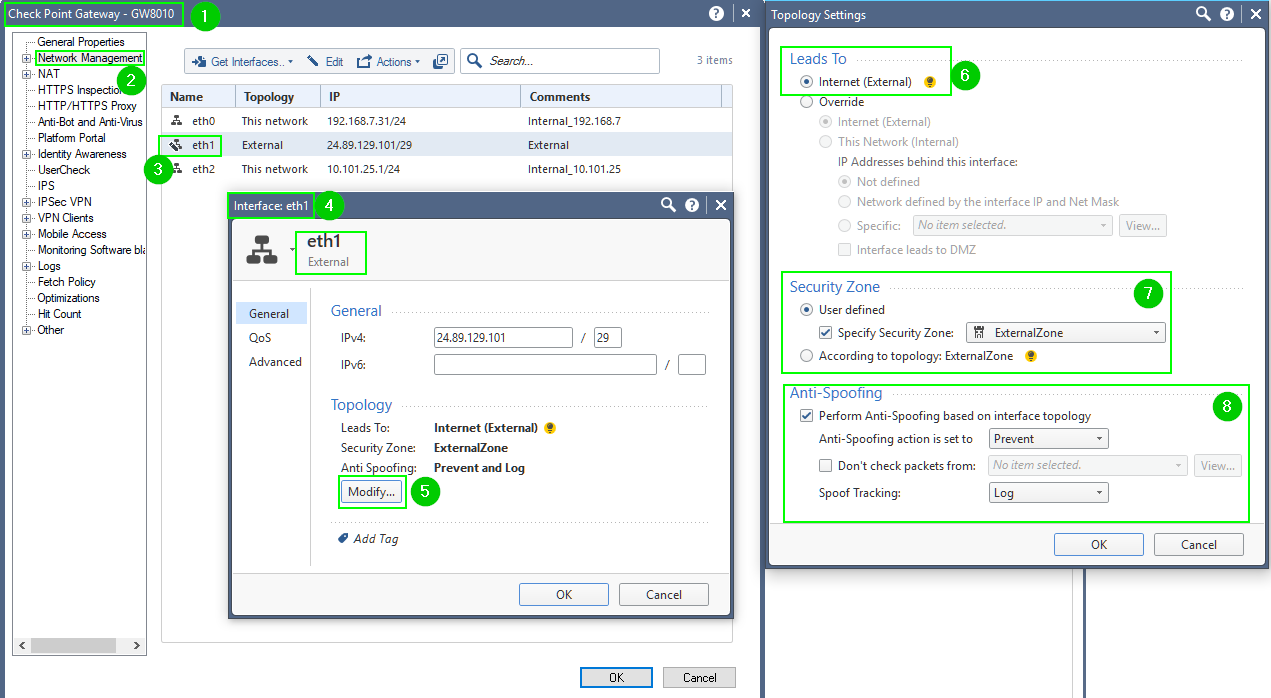
In step 3, chose the interface connected to your ISP's router.
In step 7, you can chose "According to topology: ExternalZone"
Settings in Step 8, "Anti-Spoofing" are likely the reason you are seeing the messages shown in your screenshot above.
You still should keep it on "Prevent", but for experiment, you may disable "Perform Anti-Spoofing based on interface topology" load the policy ignoring the warning and see if you are getting replies.
Then revert to normal Anti-Spoofing settings.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
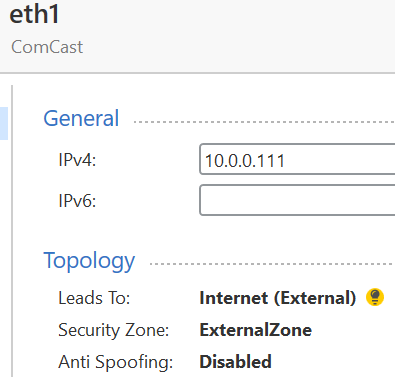
Hi Vladimir, this is helpful but still doesn't resolve my issue. The FW was reconfigured as your pictures suggested & published but still get the same output when a ping was attempted at internal host (172.16.0.7):
The same result for both cases: (enable or disable perform Anti-Spoofing....)
;[cpu_0];[fw4_0];fw_log_drop_conn: Packet <dir 1, 8.249.107.254:80 -> 10.0.0.111:35062 IPP 6>, dropped by handle_spoofed_susp, Reason: Address spoofing;
;[cpu_0];[fw4_0];fw_log_drop_conn: Packet <dir 1, 205.185.216.10:80 -> 10.0.0.111:10062 IPP 6>, dropped by handle_spoofed_susp, Reason: Address spoofing;
;[cpu_0];[fw4_0];fw_log_drop_conn: Packet <dir 1, 8.249.107.254:80 -> 10.0.0.111:35062 IPP 6>, dropped by handle_spoofed_susp, Reason: Address spoofing;
;[cpu_0];[fw4_0];fw_log_drop_conn: Packet <dir 1, 8.8.8.8:0 -> 10.0.0.111:10005 IPP 1>, dropped by handle_spoofed_susp, Reason: Address spoofing;
;[cpu_0];[fw4_0];fw_log_drop_conn: Packet <dir 1, 8.249.107.254:80 -> 10.0.0.111:35062 IPP 6>, dropped by handle_spoofed_susp, Reason: Address spoofing;
;[cpu_0];[fw4_0];fw_log_drop_conn: Packet <dir 1, 8.249.107.254:80 -> 10.0.0.111:35062 IPP 6>, dropped by handle_spoofed_susp, Reason: Address spoofing;
;[cpu_0];[fw4_0];fw_log_drop_conn: Packet <dir 1, 8.249.107.254:80 -> 10.0.0.111:35062 IPP 6>, dropped by handle_spoofed_susp, Reason: Address spoofing;
;[cpu_0];[fw4_0];fw_log_drop_conn: Packet <dir 1, 8.249.107.254:80 -> 10.0.0.111:35062 IPP 6>, dropped by handle_spoofed_susp, Reason: Address spoofing;
;[cpu_0];[fw4_0];fw_log_drop_conn: Packet <dir 1, 205.185.216.10:80 -> 10.0.0.111:10062 IPP 6>, dropped by do_inbound, Reason: Address spoofing;
;[cpu_0];[fw4_0];fw_log_drop_conn: Packet <dir 1, 8.8.8.8:0 -> 10.0.0.111:10005 IPP 1>, dropped by handle_spoofed_susp, Reason: Address spoofing;
;[cpu_0];[fw4_0];fw_log_drop_conn: Packet <dir 1, 69.89.207.99:123 -> 10.0.0.111:123 IPP 17>, dropped by handle_spoofed_susp, Reason: Address spoofing;
;[cpu_0];[fw4_0];fw_log_drop_conn: Packet <dir 1, 8.248.45.254:80 -> 10.0.0.111:35063 IPP 6>, dropped by handle_spoofed_susp, Reason: Address spoofing;
;[cpu_0];[fw4_0];fw_log_drop_conn: Packet <dir 1, 8.248.45.254:80 -> 10.0.0.111:35063 IPP 6>, dropped by handle_spoofed_susp, Reason: Address spoofing;
;[cpu_0];[fw4_0];fw_log_drop_conn: Packet <dir 1, 8.248.45.254:80 -> 10.0.0.111:35063 IPP 6>, dropped by handle_spoofed_susp, Reason: Address spoofing;
;[cpu_0];[fw4_0];fw_log_drop_conn: Packet <dir 1, 8.8.8.8:0 -> 10.0.0.111:10005 IPP 1>, dropped by handle_spoofed_susp, Reason: Address spoofing;
;[cpu_0];[fw4_0];fw_log_drop_conn: Packet <dir 1, 8.248.45.254:80 -> 10.0.0.111:35063 IPP 6>, dropped by handle_spoofed_susp, Reason: Address spoofing;
;[cpu_0];[fw4_0];fw_log_drop_conn: Packet <dir 1, 8.8.8.8:0 -> 10.0.0.111:10005 IPP 1>, dropped by handle_spoofed_susp, Reason: Address spoofing;
;[cpu_0];[fw4_0];fw_log_drop_conn: Packet <dir 1, 8.248.45.254:80 -> 10.0.0.111:35063 IPP 6>, dropped by handle_spoofed_susp, Reason: Address spoofing;
;[cpu_0];[fw4_0];fw_log_drop_conn: Packet <dir 1, 8.252.10.254:80 -> 10.0.0.111:10074 IPP 6>, dropped by handle_spoofed_susp, Reason: Address spoofing;
;[cpu_0];[fw4_0];fw_log_drop_conn: Packet <dir 1, 8.8.8.8:0 -> 10.0.0.111:35006 IPP 1>, dropped by handle_spoofed_susp, Reason: Address spoofing;
;[cpu_0];[fw4_0];fw_log_drop_conn: Packet <dir 1, 8.249.107.254:80 -> 10.0.0.111:10075 IPP 6>, dropped by handle_spoofed_susp, Reason: Address spoofing;
;[cpu_0];[fw4_0];fw_log_drop_conn: Packet <dir 1, 8.8.8.8:0 -> 10.0.0.111:35006 IPP 1>, dropped by handle_spoofed_susp, Reason: Address spoofing;
;[cpu_0];[fw4_0];fw_log_drop_conn: Packet <dir 1, 8.249.107.254:80 -> 10.0.0.111:10075 IPP 6>, dropped by handle_spoofed_susp, Reason: Address spoofing;
;[cpu_0];[fw4_0];fw_log_drop_conn: Packet <dir 1, 8.249.107.254:80 -> 10.0.0.111:10075 IPP 6>, dropped by handle_spoofed_susp, Reason: Address spoofing;
;[cpu_0];[fw4_0];fw_log_drop_conn: Packet <dir 1, 8.249.107.254:80 -> 10.0.0.111:10075 IPP 6>, dropped by handle_spoofed_susp, Reason: Address spoofing;
;[cpu_0];[fw4_0];fw_log_drop_conn: Packet <dir 1, 8.8.8.8:0 -> 10.0.0.111:35006 IPP 1>, dropped by handle_spoofed_susp, Reason: Address spoofing;
;[cpu_0];[fw4_0];fw_log_drop_conn: Packet <dir 1, 8.249.107.254:80 -> 10.0.0.111:10075 IPP 6>, dropped by handle_spoofed_susp, Reason: Address spoofing;
;[cpu_0];[fw4_0];fw_log_drop_conn: Packet <dir 1, 8.249.107.254:80 -> 10.0.0.111:10075 IPP 6>, dropped by handle_spoofed_susp, Reason: Address spoofing;
;[cpu_0];[fw4_0];fw_log_drop_conn: Packet <dir 1, 8.8.8.8:0 -> 10.0.0.111:35006 IPP 1>, dropped by handle_spoofed_susp, Reason: Address spoofing;
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did you install the policy after publishing the changes?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Show us the topology info for your external interface. It is still incorrect.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
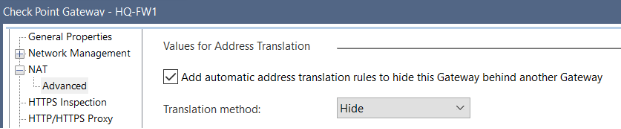
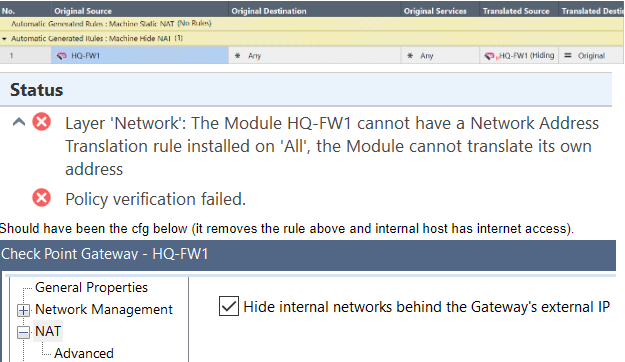
One of the root causes was...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Antispoofing drops mean your topology is not properly defined. Look into interface topologies to fix the issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can some expert please explain or share link to the answer?
I'm still unclear about the difference and when it would be appropriate to use one of the following options:
1) CP GWY: NAT > Advanced > Add automatic address translation rules > to hide this gateway behind another gateway
2) CP GWY: NAT > Hide internal networks behind the gateway's external IP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
1. If you have two gateways, i.e. Internal and External, the setting "CP GWY: NAT > Advanced > Add automatic address translation rules > to hide this gateway behind another gateway" allows you to specify that either:
a). you'll be hiding your Internal Gateway behind IP address of the External interface of your External Gateway
In this case, you have to specify the actual External Gateway, behind who's IP you are hiding and the NAT rule will be installed on that unit:

b). you'll be hiding your Internal Gateway behind IP address of another NAT capable device, such as your ISPs router.
So if you have a single gateway with internal network 10.0.0.0/24 and external network 192.168.1.0/24 connected to the ISP router's internal port and the external port having a single public IP (for example 20.20.20.1/30) assigned to the router, you can specify that in this setting:
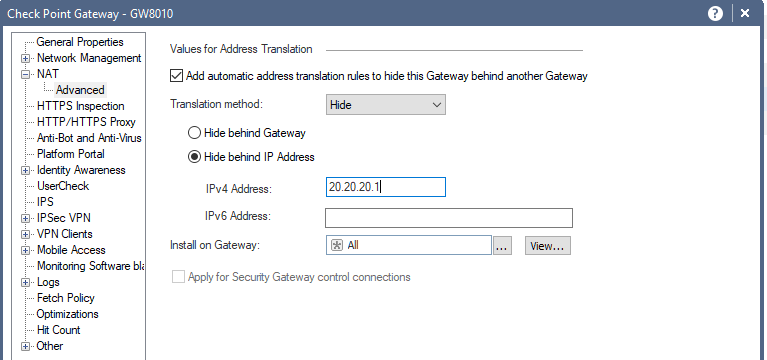
What you cannot do is hide your gateway behind it's own external IP, as this will look like dog chasing it's own tail.
2. The "CP GWY: NAT > Hide internal networks behind the gateway's external IP" simply allows you to hide all of your internal networks behind external IP of your single gateway.
I.e. it is the same thing any home router is doing by overloading single public IP with the internal network range on its way out to the Internet.
It is seldom used in business environments that have multiple public IPs or entire network ranges from ISPs, as a more prudent approach is to "Hide" or "Statically NAT" individual hosts or networks behind either external interface of the gateway (for general access to the Internet), or particular IPs (for inbound traffic, such as mail, FTP, etc..).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content


and that your policy does not drop the ICMP replies.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks. Is your CP FW behind another FW?
These are the cfg on my FW. However, this CP FW is behind another FW (NAT) and SNAT is being used at 2 places (CP and ComCast FW). In your case, probably public IP is assigned to eth1 (ext interface) and there is no NAT after that.
In addition, not only ICMP can't get out but also http, udp etc.
Probably, I need to study Timothy Hall's suggestion above..
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 42 | |
| 21 | |
| 10 | |
| 7 | |
| 7 | |
| 6 | |
| 5 | |
| 5 | |
| 5 | |
| 4 |
Upcoming Events
Thu 20 Nov 2025 @ 05:00 PM (CET)
Hacking LLM Applications: latest research and insights from our LLM pen testing projects - AMERThu 20 Nov 2025 @ 10:00 AM (CST)
Hacking LLM Applications: latest research and insights from our LLM pen testing projects - EMEAWed 26 Nov 2025 @ 12:00 PM (COT)
Panama City: Risk Management a la Parrilla: ERM, TEM & Meat LunchThu 20 Nov 2025 @ 05:00 PM (CET)
Hacking LLM Applications: latest research and insights from our LLM pen testing projects - AMERThu 20 Nov 2025 @ 10:00 AM (CST)
Hacking LLM Applications: latest research and insights from our LLM pen testing projects - EMEAThu 04 Dec 2025 @ 12:30 PM (SGT)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - APACThu 04 Dec 2025 @ 03:00 PM (CET)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - EMEAThu 04 Dec 2025 @ 02:00 PM (EST)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - AmericasWed 26 Nov 2025 @ 12:00 PM (COT)
Panama City: Risk Management a la Parrilla: ERM, TEM & Meat LunchAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


