Hi guys.
I am facing again strange issue when upgrading the gateway to 81.10
I upgraded the management server to 81.10 and also the small appliances and all seems ok on this side.
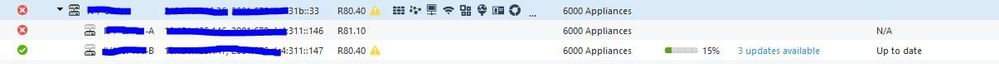
Now I am trying to upgrade 2 x 6600 Gateways that are in a Cluster XL configuration.
I do an in place upgrade via CPUSE and the upgrade process itself of the passive member goes OK, but after the upgrade I loose access to the gateway via SSH or Gaia.
[2023-06-14 - 10:33:51][26105 32165]:BLINK::skipping Major_PostInstallScript
[2023-06-14 - 10:33:51][26105 32165]:BLINK::skipping Major_LVMRenameAndSnapshotDetails
[2023-06-14 - 10:33:51][26105 32165]:Running Command || Description: Success DA Post install : Writing response
[2023-06-14 - 10:33:51][26105 32165]:Running Command || Command: echo -n "0" > /var/log/blink/processOutput
[2023-06-14 - 10:33:51][26105 32165]:Finished executing Blink post actions sequence
[2023-06-14 - 10:33:51][26105 32165]:------ Post-Install Script: ------
[2023-06-14 - 10:33:51][26105 32165]:Lock release successes
[2023-06-14 - 10:33:52][26105 32165]:Blink Install Info || Completed : false || State : run_post_script || Status Description : Run post.sh script
[2023-06-14 - 10:34:06][26105 29768]:Return code: 1
[2023-06-14 - 10:34:06][26105 32165]:Blink Install Info || Completed : true || State : finish_message || Status Description : The installation has finished successfully, reboot is suspended, perform it manually in order to finish the installation.
[2023-06-14 - 10:34:06][26105 32165]:------ Finishing: ------
[2023-06-14 - 10:34:07][26105 32165]:Found previous installed build for MGMT//6.0//HOTFIX_R80_40_JUMBO_HF_MAIN//PreviousInstalled
[2023-06-14 - 10:34:07][26105 32165]:Found previous installed build for FW1//6.0//HOTFIX_R80_40_JUMBO_HF_MAIN//PreviousInstalled
[2023-06-14 - 10:34:07][26105 32165]:Found previous installed build for PPACK//6.0//HOTFIX_R80_40_JUMBO_HF_MAIN//PreviousInstalled
[2023-06-14 - 10:34:07][26105 32165]:Found previous installed build for CVPN//6.0//HOTFIX_R80_40_JUMBO_HF_MAIN//PreviousInstalled
[2023-06-14 - 10:34:07][26105 32165]:Found previous installed build for CPUpdates//6.0//BUNDLE_R80_40_JUMBO_HF_MAIN//PreviousInstalled
[2023-06-14 - 10:34:07][26105 32165]:Found previous installed build for CPUpdates//6.0//BUNDLE_R80_40_MAAS_TUNNEL_AUTOUPDATE//PreviousInstalled
[2023-06-14 - 10:34:07][26105 32165]:Found previous installed build for CPUpdates//6.0//BUNDLE_DEP_INSTALLER_AUTOUPDATE//PreviousInstalled
[2023-06-14 - 10:34:07][26105 32165]:Found previous installed build for CPUpdates//6.0//BUNDLE_INFRA_AUTOUPDATE//PreviousInstalled
[2023-06-14 - 10:34:07][26105 32165]:Found previous installed build for CPUpdates//6.0//BUNDLE_ESOD_SCANNER_AUTOUPDATE//PreviousInstalled
[2023-06-14 - 10:34:07][26105 32165]:Found previous installed build for CPUpdates//6.0//BUNDLE_ESOD_CSHELL_AUTOUPDATE//PreviousInstalled
[2023-06-14 - 10:34:07][26105 32165]:Found previous installed build for CPUpdates//6.0//BUNDLE_HCP_AUTOUPDATE//PreviousInstalled
[2023-06-14 - 10:34:07][26105 32165]:Found previous installed build for CPUpdates//6.0//BUNDLE_GOT_TPCONF_AUTOUPDATE//PreviousInstalled
[2023-06-14 - 10:34:07][26105 32165]:Found previous installed build for CPUpdates//6.0//BUNDLE_CORE_FILE_UPLOADER_AUTOUPDATE//PreviousInstalled
[2023-06-14 - 10:34:07][26105 32165]:Found previous installed build for CPUpdates//6.0//BUNDLE_CPSDC_AUTOUPDATE//PreviousInstalled
[2023-06-14 - 10:34:07][26105 32165]:Found previous installed build for CPUpdates//6.0//BUNDLE_GENERAL_AUTOUPDATE//PreviousInstalled
[2023-06-14 - 10:34:07][26105 32165]:Found previous installed build for CPUpdates//6.0//BUNDLE_CPOTELCOL_AUTOUPDATE//PreviousInstalled
[2023-06-14 - 10:34:07][26105 32165]:Found previous installed build for CPUpdates//6.0//BUNDLE_CPVIEWEXPORTER_AUTOUPDATE//PreviousInstalled
[2023-06-14 - 10:34:07][26105 32165]:Found previous installed build for CPUpdates//6.0//BUNDLE_ENDER_V17_AUTOUPDATE//PreviousInstalled
[2023-06-14 - 10:34:13][26105 32165]:crsXml file: /opt/CPda/repository/CheckPoint#Major#All#6.0#5#3#BLINK_R81_10_T335_JHF_T95_GW/crs.xml doesn't exist.
[2023-06-14 - 10:34:13][26105 32165]:------ Going to reboot: ------
[2023-06-14 - 10:34:28][26105 32165]:------ ------
I only have access to this gateway via Lights Out Management.
If I log in via LOM and try to ssh to localhost I can fine ssh , telnet to localhost on https port also ok.
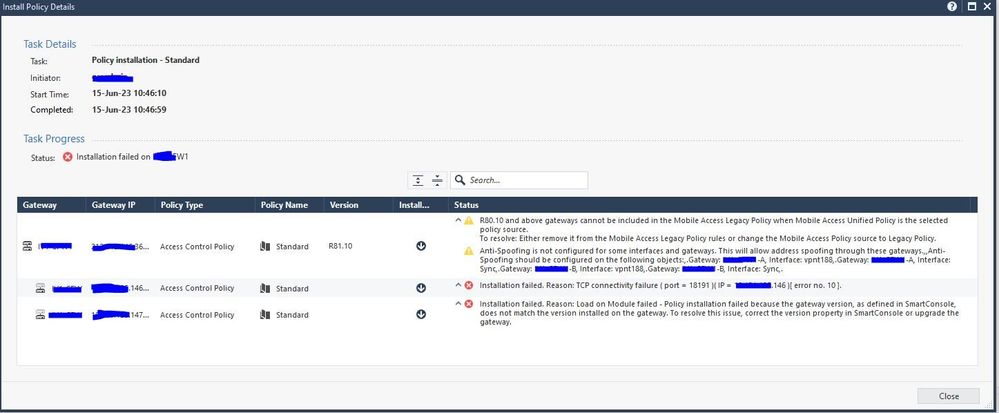
If i try to fetch the policy I get an error (even if I modified the cluster version in the management console ) :
Fetching FW1 Security Policy From: xx.xx.xxx.xx
Management rejected fetch for this module - version matching problem.
Policy Fetch Failed
Failed to fetch policy from masters in masters file
Fetching Threat Prevention Security Policy From: xx.xx.xxx.xx
Connectivity out of the upgraded gateway is no problem , I can ping , ssh , ftp etc from the upgraded gateway but nothing towards it.
So I end up reverting to the snapshot as I have been struggling with this for the past 2 days.
Any ideas ?
Thank you in advance.