- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast Weekly Reports - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
The Future of Browser Security:
AI, Data Leaks & How to Stay Protected!
CheckMates Fest 2025!
Join the Biggest Event of the Year!
Simplifying Zero Trust Security
with Infinity Identity!
CheckMates Go:
Recently on CheckMates
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- IMPORTANT: Client VPN/Endpoint versions E81.10 or ...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
IMPORTANT: Client VPN/Endpoint versions E81.10 or earlier – MUST UPDATE before January 1st 2021
On August 2019 we released version E81.20 addressing usage limitation of older versions of Check Point’s Endpoint, VPN and SandBlast agent (sk158912). These older, out of support versions – Endpoint/VPN E80.81 to E81.10 (Windows only) and SandBlast agent E80.61 to E81.10 (Windows only) – WILL CEASE TO OPERATE on January 1st 2021.
Unfortunately, we see that some customers haven’t updated these old versions. Their update will become more difficult to facilitate after January 1st.
Therefore, we urge to all customers reminding them that users of versions E81.10 and before are required to update their versions by January 1st 2021 in order to make sure their systems remain operational.
We offer our customers two options to address this request. Upgrade to a newer version (Recommended) or apply a simple fix to the old version. Look into sk171213 for the details.
Either way, customers should make sure to carry upgrades to supported versions (E83 or later versions) at a later time to ensure they receive the best security.
Our TAC services are available to support any customer needs regarding this request. More information can be found on this web page.
Please find some FAQ below:
FAQs
- Q: Why are we approaching all customers now?
On August 2019 we released version E81.20 addressing usage limitation of older versions of Check Point’s Endpoint, VPN and SandBlast agent (sk158912). These older, out of support versions will cease to operate on January 1st 2021. We are approaching all customers as we saw that many of them haven’t updated these old versions, and their update will become more difficult to facilitate after January 1st. So, we need to make sure they do so this week – before January 1st – to ensure a smooth and easy to facilitate transition to newer versions. - Q: What is the technical problem?
The issue happens due to the internal certificate used by VPN/Endpoint services. One of the certificates expires on January 1st 2021, therefore all services that use this certificate will stop working on January 1st 2021. The fix is within the driver library: epklib. The library fixes an issue with regards to the certificate’s expiration validation (current date and not the signing date). - Q: Which versions are affected, and which are not?
A: For the full list of affected clients, please refer to sk171213. - Q: Is this a security update? Is there a vulnerability in the software?
A: No. This is a functional update to ensure VPN and blade connectivity and functionality. There are no known security vulnerabilities. - Q: Is this a pressing matter?
A: Yes! Customers need to act before Jan-1st 2021. After this date they may experience client malfunctions For Stand Alone VPN with Firewall – the Firewall and the VPN may stop working. For Endpoint client - Firewall, Forensics, Threat Emulation, Anti-Bot and in some cases also the VPN may stop working.
- Q: Are customers notified?
Impacted versions are already out-of-support. See Check Point Support Life Cycle Policy. - Q: What is the suggested course of action?
Please follow sk171213 for the full details on all the actions.- A. Upgrade to a newer version (E81.20 or later versions). We recommend using version E84.0 Download link, or
- B. Apply a quick and temporary fix that takes a minute to install (Download from sk171213).
Either way, you should make sure to carry upgrades to supported versions (E83 or later versions) at a later time to ensure you receive the best security.
- Q: Who should I approach for additional information?
The Check Point TAC should be consulted. - Q: What indications customers will encounter facing this problem?
- Inability to connect using remote access VPN. Error message while connecting "Connectivity with the Check Point Endpoint Security service is lost".
- “Blade not running” indicated in Endpoint/VPN client Display Overview.
2 Solutions
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We now have a simple UI application for end users without admin rights that runs on Endpoint Security versions that will apply the necessary patch.
This is in addition to the previous simple UI application for users with admin rights.
This tool is published under https://www.checkpoint.com/fix/ and referenced from sk171213.
For users without admin rights, we also have updated the tool that leverages the admin password cached on the end-user machine.
This version of the tool will work for standalone VPN and Endpoint Security.
See sk171341 for all details, and it's referenced from sk171213.
We also now have a VPN recovery tool that uses the Capsule VPN plugin for Windows 10 to initiate a VPN connection to the relevant Security Gateway, using the existing Endpoint Security configuration.
This will allow the client to be patched using existing mass deployment tools.
See sk171341 for all details, and it's referenced from sk171213.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
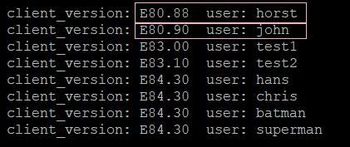
Show all current Endpoint Security VPN versions and users that can be found in the current firewall log. Executes this command on the management server:
fw log -n -p |grep "Endpoint Security VPN" | awk -F";" '{print $7 ,$9}' | grep client_version |sort | uniq
Output:
This writes the output to the epc.txt file:
fw log -n -p |grep "Endpoint Security VPN" | awk -F";" '{print $7 ,$9}' | grep client_version |sort | uniq &> epc.txt
More read here: Endpoint Versions - ONELINER
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
60 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello..
First time poster but regular viewer. Thanks for post. Got the email from Check Point earlier today and I am currently working through this now as this is going to be a major headache for us as we have massive deployments of Endpoint VPN across many customers and versioning is a mix on Win7, 8 & 10 unfortunately.
What I am trying to figure out currently is how we can run a report to see what versions that users are on? I cannot find an easy way to do it - the "All Users" view in Smartview Monitor has a "Version" column but no information populated. Are there custom reports I can generate in Smart Event or Logs etc (R80.40)
One other question I have not been able to confirm or test yet is whether the small patch requires Admin rights to install - we would have customers with varying policies on desktops/laptops so cannot be sure but if it can be installed without Admin rights it would be a big help.
Any help would be really appreciated.
Thanks again, Hugh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is there any workaround? We have hundreds of Clients affected with that issue - now in vacation and if they try to connect in january they keep offline so that package distribution with the hotfix or a newer vpn client is not possible. Users also do not have the rights to install anything (patch or vpn client) on their own.
As tested vpn service goes down - so upgrade from gateway is also no option.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As mentioned in https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut... the upgrade is the recommended solution. In the article, it also mentions options for a workaround.
For example, you can use a workaround mentioned here: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
in this Case we have absolutely no workarounds - actually it is unintelligible why such an information comes 1 week before day-x ! With one or two month before an update would have been no problem - by the end of december with 4 days time abolutely no chance.
The SKs were created 2020-12-27 - so actually I think that also checkpoint was not aware of that issue!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello.. is there a simple way to run back thru SmartLog data or to run off a report to see what version is in use for Endpoint clients? I can see the version info in the Log In data but want to know is there a way to get it in a report along with the username. This is just for 1 x customer on R80.40 with Smart Event & Reporter etc - lots of other customers on differing versions and no reporter licenses.
Overall this is a major disaster and can see it affecting hundreds of customers and thousands of users.. quite simply massive amounts of users are going to be on affected versions as organisations have not risked updating VPN clients this year due to the pandemic and risk of totally isolating users without ability to get them back into the office to fix them.
Any help or guidance would be really appreciated. I don't think the Compliance check fix is going to be really feasible - it seems convoluted and also I think extra licensing is required etc and the time to test and rollout is too short, and if it goes wrong we have a bigger issue to fix!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Hugh,
I'm right now using this way:
1. Select Column Profile: Endpoint Compliance
You should get Product Version.
2. Filter for the following expression, so you don't get all the capsule, mobile access clients:
action:"Log In" and blade:"Mobile Access" and "Endpoint Security VPN"
3. Export CSV to excel
4. Import to Excel (Data -> Text/CSV)
5. Select affected versions in column Product Version
Sort/Unique users
Hope this helps somewhat.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Christoph Thanks.. that's a big help! Much appreciated. It now makes me realise even more how big an issue we have...☹️
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In addition I have tested in a small lab using the following filter in SmartLog to look for the affected versions in the logs. Then export to CSV as you described with the Column Profile.
action:"Log In" AND ("Endpoint Security") AND (E80.81 or E80.82 or E80.83 or E80.84 or E80.85 or E80.86 or R80.87 or E80.88 or E80.89 or E80.90 or E80.92 or E80.94 or E80.95 or E80.96 or E80.97 or E81.00 or E81.10)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, - you can do that with smartview. Filter on Action: Log In, then edit profile to show also the column "Client Version". You can export that as xlsx and go on filterinh in Excel.
I opened an SR today - to check the workarounds - so for my environments no way - and not in that small...tiny timeslot!
Actually I am working for 16 years with checkpoint gateways in deep and never had such an bad announcement before......5 days before the bug bang.
Also for me and my customers a real disaster - especially in corona times when users are forced to work from home.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Has anyone run the "EPPatch.msi" on machines that are not affected by this problem?
The reason for asking this is, if one can run this EPPatch on any client version, one could software deploy this patch to all connecting clients before Jan-1, without having to implement a complex software update policy, taking into account every version (no idea how to do that). Though this would only help for some clients (not the people that come back on the 4th from holidays), this might lessen the problem.
Unfortunately I do not have such an old client at hand for testing.
In addition, I'm not sure what happens when a uninstall password is set. Trying to install the patch on a new sandblast enabled machine I get the following error. Maybe it's related to the unsupported sandblast agent or the uninstall password. Where is the logfile for the patch? (sorry for the poor image quality, was a screengrab of a video)
Edit: Updated SK clarified this question.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Christoph I've an E75.30 if that's any use? Works on Windows 7. As far as I can see any patching requires Admin privileges so not an option to be able to send users off to update themselves as most won't have the permissions. So only real way I can see is via GPO, or whatever 3rd party software tools a customer uses - and the window to cover all these is getting smaller by the hour! Don't know if its against forum rules to attached a Check Point software item.. maybe someone can confirm?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@PaddyCPIt's ok, no need to and only E80.81-81.10 are affected anyway. The updated SK offers a few more answers. Worst case, but may prove to help in some scenarios "...ask the users to change the windows clock to 21-Dec-2020 and reboot...", if NTP does not interfere.
Just one last remark. CP recommends upgrading to 84.00 and in the SK article 84.00 is referenced. If users are able to update by themselves, the might reach the client via a search engine and the CP portal for the VPN client (Remote Secure Access VPN | Check Point Software) There 84.20 is referenced, which is broken at this time and disconnects users, when the lock screen activates. They should probably not update to this version. 84.30 fixes this bug.
Since today, E84.30 is released on the official download site.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Assuming what they have is the Endpoint VPN client and not, say, the full Endpoint suite.
If you installed the client as Check Point Mobile or SecuRemote (neither of which include the Desktop Firewall), then you will not be impacted by this issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I posted a - far from perfect - help using the logs API of R80.40 to see the VPN Client version used over the last 30 days here
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have created a very basic Report that shows the users, client versions and OS name/version based on the logs. Also far from perfect but it is a start.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Wolfgang If you post this in a separate post, I will be able to move it to Toolbox. Please consider and let me know 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This would be outdated in less than 48 hours.
What we really need is a SmartEvent report that easily shows all supported and unsupported Endpoint client versions in use. I posted this here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So - finally nobody has an idea for an workaround? I also no chance to get the hotfix installed remotely with admin rights......only one by one user with enabled hotspot detection - really worst case scenario.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Since we're replacing a driver as part of the patch, admin rights are a necessity.
We are investigating other solutions.
Since the bug is date-triggered, backdating the system is always an option.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The patch we created is the simplest resolution we could for remote install. It can be activated from endpoint security server (with compliance) or from GPO or from any other form of pc software distribution system. The patch takes less than 10 seconds to install and require no interaction from the end user and no boot.
The alternative approach will be to use the GW to force VPN upgrade.
If neither of these is used before the date of expiry then the VPN fails and depending on your policy, the above actions may become more difficult
Dorit
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
can you provide further details on the driver name and version before and post patch please?
I am looking at deploying via SCCM and the detection is being a pain based on the eppatch.msi product code not registering correctly and not being detected.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We're replacing a specific driver.
You can see the details here: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Actually - since it is not possible to distribute a hotfix (within 5 days) when 99% of the users are offline all my affected customers must prepare on one-by-one install in january.
So.....just one question to checkpoint.....since the problem was fixed in E81.20 I it was known since Aug 2019......so why now this "IMPORTANT Notice" 1 week before 1.1.21 and not earlier?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
All affected versions are out of support since August 2020 or earlier, as mentioned above. It is also properly listed in our Lifecycle Management page.
The issue is only relevant to customers who do not adhere to our software support guidance. However, we do see signs of those unsupported versions still running out there.
The purpose of this communication to raise awareness to those who are affected and provide them with actions to do before their business is affected.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I don't quite understand one thing, for simple Endpoint Security clients without any blades:
<= 80.80 - not affected
=> 81.20 - not affected
80.80 < Are these versions Endpoint Security affected? < 81.20
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Quoting: SandBlast Agent:
E81.10, E81, E80.97, E80.95, E80.96, E80.94, E80.92, E80.90, E80.89, E80.88, E80.87, E80.86, E80.85, E80.84, E80.83, E80.82, E80.81, E80.80, E80.72, E80.71, E80.70, E80.65, E80.64, E80.62, E80.61
Endpoint Security VPN and Endpoint Security VPN for ATM:
E81.10, E81, E80.97, E80.95, E80.96, E80.94, E80.92, E80.90, E80.89, E80.88, E80.87, E80.86, E80.85, E80.84, E80.83, E80.82, E80.81
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Long time ago we increased self protection of security but the check we added was too restrictive and in E81.20 we corrected the check ... So the effected versions are between very old version to slightly less old versions ....
The exact version depends on the type of client you use: In VPN stand alone the effect is from E80.81 and in EP+SBA the effect is from E80.61. If you have VPN without FW then the problem will not effect you
The exact detailed versions per product are in the SK
- What products and versions are affected?
a. Standalone VPN: I. Endpoint Security VPN from versions E80.81 to E81.10 (no longer supported) II. Endpoint Security VPN for ATM from versions E80.81 to E81.10 (no longer supported) NOTE: It does not matter if the desktop policy (policy server) is used or not; The above two clients will be affected b. Check Point Endpoint Security Suite / SandBlast Agent: I. Check Point Endpoint / SandBlast Agent from versions E80.61 to E81.10 (no longer supported) if one of the following blades is being used: Forensics, Threat Emulation and Anti-Bot blades - What products and versions are NOT affected?
a. Standalone VPN: I. Endpoint Security VPN from versions E81.20 and above II. Endpoint Security VPN for ATM from versions E81.20 and above III. Check Point Mobile / SecuRemote - all versions IIII. Endpoint Security VPN from versions E80.80 and below (no longer supported) b. Check Point Endpoint / SandBlast Agent: I. Check Point Endpoint and SandBlast Agent from versions E81.20 and above II. Check Point Endpoint, not using Forensics, Threat Emulation and Anti-Bot blades from versions E80.80 and below (no longer supported) c. Win XP - all products and versions d. Mac OS - all products and versions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Your comment “If you have a VPN without FW, then it won’t effect you”.
Does that mean only the firewall blade is effected, but the VPN will still connect?
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 12 | |
| 12 | |
| 12 | |
| 9 | |
| 9 | |
| 8 | |
| 6 | |
| 3 | |
| 3 | |
| 2 |
Upcoming Events
Tue 04 Mar 2025 @ 04:00 PM (CET)
Check Point | WIZ : Powering the Next Era of Cloud Security - EMEA & AMERICASTue 04 Mar 2025 @ 05:00 PM (PST)
Check Point | WIZ : Powering the Next Era of Cloud Security - AMERICAS & APACTue 11 Mar 2025 @ 05:00 PM (CDT)
Under the Hood: Configuring Site to Site VPN with Azure Virtual WAN and CloudGuard Network SecurityTue 04 Mar 2025 @ 04:00 PM (CET)
Check Point | WIZ : Powering the Next Era of Cloud Security - EMEA & AMERICASTue 11 Mar 2025 @ 05:00 PM (CDT)
Under the Hood: Configuring Site to Site VPN with Azure Virtual WAN and CloudGuard Network SecurityWed 12 Mar 2025 @ 06:00 PM (IST)
TechTalk: The Future of Browser Security: AI, Data Leaks & How to Stay ProtectedAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter