- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
Quantum SD-WAN Monitoring
Watch NowCheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: IA sharing at scale
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
IA sharing at scale
Hello
We manage 50+ gw with full meshed IA sharing.
We face lot of isues with IA.
Some random IA not propagated accross gw, some random IA agents not able to connect to their local gw...
Something that improve the behavior a little bit is a cronjob to kill pep and pdp every night...
We think about centralising IA on a dedicated gw, so IA agents connect to this specific gw and it redistribute IA to all gw.
It's a big change that cannot be fully tested outside production and we are a little bit afraid things get worse than now.
How do you folks manage IA at scale?
Do you have to kill pep and pdp every night too?
Do you centralise IA to a single sharing gw?
Thanks for your advises.
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We are slowly migrating to this setup and it looks like our issues disappear.
Checkpoint should really highlight the usage of very centric PDP to avoid IA sharing issues as soon as 2 firewalls are involved.
10 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
sk88520: Best Practices - Identity Awareness Large Scale Deployment
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, I read that.
I want to know administator feedback about IA sharing in general, this solution or others they may have deployed to fix IA.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R81.20 has some relevant IA enhancements...
Are you using any of the following today and what version are the current Gateways?
- Identity Collector
- Identity Broker
- Dedicated PDPs
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We are currently running R81.10 HFA110 on every gw.
We'll upgrade to R81.20 as soon as we get a maintenance windows.
- Identity Collector: No. We don't use ADQuery. Only IA agents. Plus, each remote gateway fetch from its local DC
- Identity Broker: No. We didn't invest in it as the configuration involve files modifications with complex syntax on every firewalls. Now, if you tell us it enhance the UX, we'll consider it. But how is it different from "classical" PDP? Why is it not the default PDP mecanism?
- Dedicated PDPs: No. That's what this post is all about... Is it a good move? Is the user community doing it? what is their feeddback?...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
Please check not resolved issues in IA for R81.20:
BR,
Daniel.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
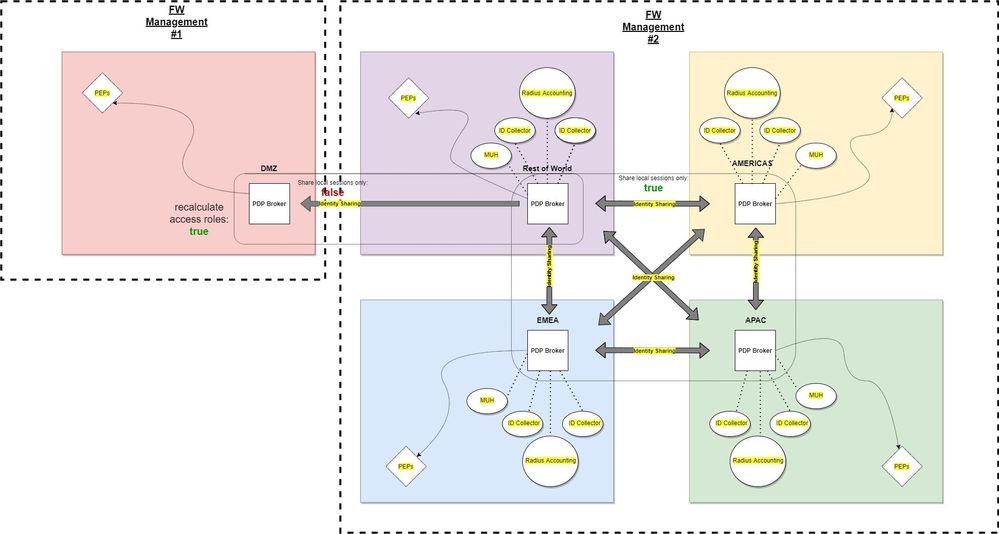
we use dedicated PDP Brokers. The firewall itselfs only do the pep enforcement. We completly seperated these two services from each other. These PDP Brokers are full meshed to share all identies with each other. The peps only consume the identies from their local PDP Broker.
We don't need to kill pep / pdp every night.
We setup a centralised IA PDP Broker for every region.
We switched from our full meshed design to PDP Brokers in 2021. I draw our design and uploaded it here:
If you want more informations, feel free to contact me via private message.
Best regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
Thanks for sharing.
Your setup make sense to us. We will think about making something similar.
Thanks mate!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We are slowly migrating to this setup and it looks like our issues disappear.
Checkpoint should really highlight the usage of very centric PDP to avoid IA sharing issues as soon as 2 firewalls are involved.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @ProxyOps
Very interesting design!
Just wondering if your PDP Broker are working with Cluster_XL or not ? Does Cluster_XL synchronize the IA tables ?
Today we have a central design with IA Sharing accross multiples site which is just working fine. Problem is to find window maintenance to upgrade this central IA gateway.
This central Gateway is doing PDP for all users and then share identity with PEP to all remote GW.
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @CP-NDA
we are running our PDP Broker as Clusters (Cluster_XL) active-standby on VMs.
Our PDP Brokers are running R81 currently are cluster_xl is not snycing the relevant tables for a interruption free failover.
When we do a failover the PDP Broker has to sync from scratch again with all over PDP Brokers.
I checked the R81.20 release noted and maybe something was improved here?
"Improved resiliency, scalability, and stability for PDPs and Identity Broker. Additional threads handle authentication and authorization flows."
I know cluster_xl is syncing some IA tables for PEP but I am not able to find a sk for that.
I have to admit, that we update the PDP Broker Gateways only if required as we need them to be as stable as possible.
Best regards
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 18 | |
| 14 | |
| 10 | |
| 8 | |
| 8 | |
| 6 | |
| 6 | |
| 6 | |
| 6 |
Trending Discussions
Upcoming Events
Tue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Tue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Thu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter