- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- I can ping but I can't browse - vpn and proxy chec...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I can ping but I can't browse - vpn and proxy check point
Hello everyone
I'm having some issues using the Check Point Gateway as a proxy when I'm using the check point client VPN.
Scenario is as follows: my gateway is configured as a proxy. Recently I activated VPN functionality. The vpn works normally, however, I can not navigate if I use the proxy check point but I can ping any site.
I made a test connected in another VPN that gives access to the same networks, I used the Check Point proxy again and the access was allowed or denied according to my ACLs and I can see it in my logs.
is there any limitation on using the gateway as vpn and proxy or should I make some configuration?
Thanks!
5 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Plea specify the version of the Check Point Management and gateways, if you have proxy configured in transparent or explicit mode, if you have defined the interface for the proxy and if you are using .pac files on your VPN clients.
Additionally, please clarify what kind of VPN are we talking about: SSL or the IPSec and if second, what VPN software client and version is in use.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for your answer, Vladimir!
I'm using R80.10 in both: Mangament and gateway. Proxy is configured in Non Transparent mode. I did not define an interface for the proxy and in this firt moment I'm not using .pac file on VPN client.
I'm using IPSec with Check Point Endpoint Security E80.70
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Kadu,
Please check if the VPN tunneling is enabled on your EndPoint Security clients, else you are looking at the split tunnel scenario, where not all traffic is being sent to the gateways.
Since you have mentioned that you can ping all the sites, (I presume from the client), try traceroute from the client to determine if your ICMP traffic is going over the VPN, or if it is going directly via local gateway of the remote client.
Additionally, it is a good idea to determine, using nslookup, where does the DNS resolution happening, locally or via VPN.
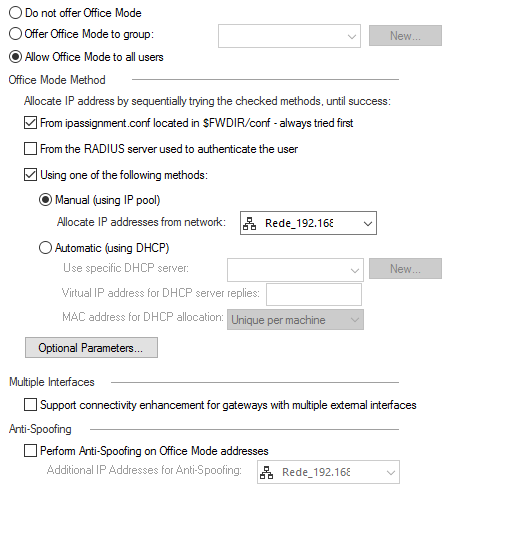
Next, confirm that you are offering "Office Mode" to remote users.
If yes, check the IP Pool that is being used for address allocation.
Make sure that you have a rule allowing the IP pool to access Internet and that it is being NATed on its way out.
You may also check "Optional Parameters" in the "Office Mode" to see what DNS servers are defined for remote clients.
Cheers,
Vladimir
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Vladimir, is this option you referred to (VPN tunneling)? How can I change it?
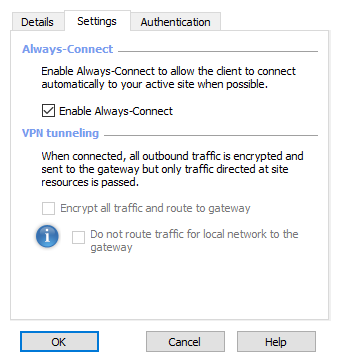
My ICMP traffic is going directly via local gateway of my remote client.
DNS resolution is happening via VPN normally.
I'm offering "Office Mode" to remote users.
Any idea?
Thanks for your time!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you are using a simple SecuRemote, you will not be able to change this:
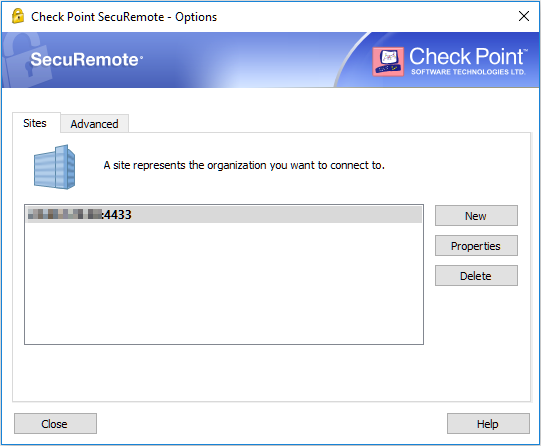
If you are using a full EndPoint security, this should work:
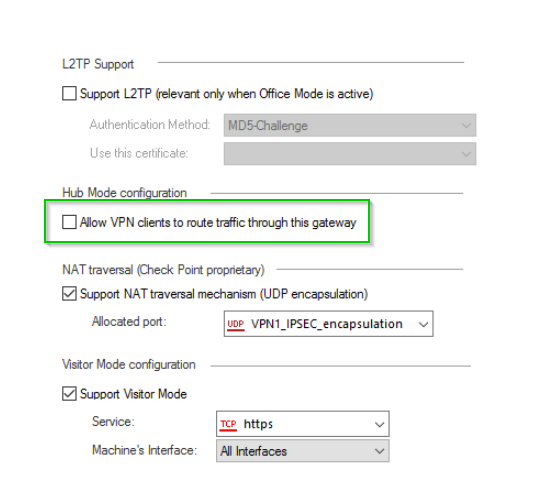
Provided the rules are in place to allow it.
Cheers,
Vladimir
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 18 | |
| 10 | |
| 10 | |
| 10 | |
| 6 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


