Step 1: Fill out a VPN setup sheet with your FortiGate VPN partner and agree on the VPN settings.
See here: VPN setup sheet template
Step 2: Start configuring your Check Point.
In Check Point SmartConsole you have to create an Interoperable Device (your FortiGate).
New > Network Object > More > Interoperable Device
There you have to fill in information like the WAN-IP of your FortiGate.
And the local subnet you want to tunnel from the FortiGate to the Check Point under “Topology”.
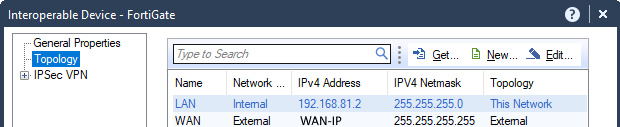
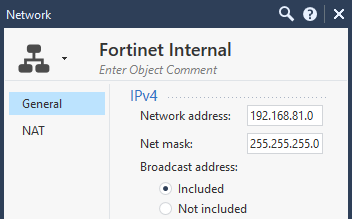
I would generally advise you to create Network Objects for both, your Check Point local subnet and your FortiGate local subnet to be reachable by VPN.
Best practice: Use Object Names that are self-explanatory.
New > Network

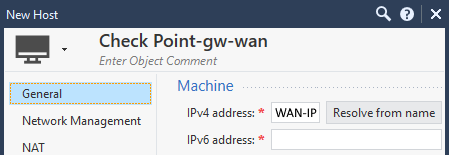
Best practice: Create a host Object with the IP of the WAN interface of your Check Point, in case the main IP of your Check Point Object is the internal IP address. This object can be used in the rulebase when configuring access rules.
New > Host
Step 3: Create a VPN community object within Check Point's SmartConsole and then head over to the FortiGate and configure the VPN there as well.
Securely configure the VPN Community, install the Security Policy to your Check Point VPN Gateway and you should then see the VPN tunnel Status: Down. After completing the VPN configuration on your FortiGate, the VPN Tunnel should go up.
Before you create a VPN-Community, make sure that your IPsec VPN blade is enabled on your Check Point:
General Properties > Network Security IPsec > VPN

Next step is to create a new VPN Community. (This can be either Star or Mesh VPN)
New > More > VPN Community > Star Community
Best practice: Use a name that is self-explanatory.
Define your Check Point VPN gateway as the Center Gateway and the FortiGate as the Satellite Gateway:

Select the correct encryption parameters that you've exchanged with your VPN partner.

Set the shared secret.
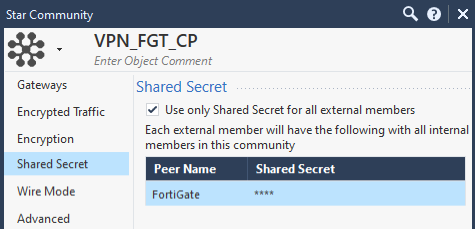
Set the correct IKE/IPsec renegotiation times and toggle "Disable NAT inside the VPN" according to your requirements.

After you saved the configuration you’ll be able to check the state of your VPN tunnel with this SmartConsole Extension.
This should show the VPN tunnel as "Down" because you haven’t configured your FortiGate yet.

Step 4: Configure a custom VPN tunnel on your FortiGate.
Custom selector(s) are required because Check Point will not accept 0.0.0.0/0 as encryption domain from the FortiGate in its usual domain-based VPN set up.
On your FortiGate WebUI, enter a name for your VPN:
VPN > IPsec Wizard

Enter the Remote Gateways IP Address and the outgoing interface.

Enter the Pre-shared Key you agreed upon as well as IKE-version.

For Phase 1 select the Encryption and Authentication you agreed upon as well as the Diffie-Hellman Group and the Key Lifetime.

For Phase 2 enter the Local and Remote Address space.

Under Advanced options you can select the Encryption and Authentication method you agreed upon as well as the Diffie-Hellman Group and the Key Lifetime.
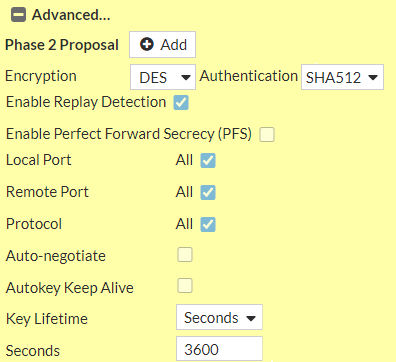
In the next step you add new Address objects under
Policy & Objects > Addresses > Create New > Address

For your local subnet:

and for the remote subnet:

for the remote wan:

for your local wan:
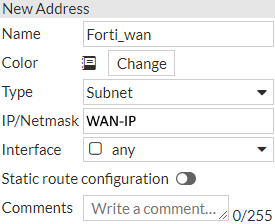
You can also add Address Groups if you want to add them to the Firewall Policies instead of the direct Subnets.
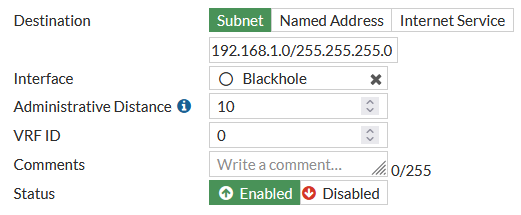
Add a static route for your remote subnet pointing to the VPN-Tunnel Interface.
Network > Static Routes > Create New

Add another static Route this time pointing to the Blackhole interface.
Last step is to add Firewall Policies to allow the VPN traffic to pass trough.
Add a New Policies Policy & Objects > Firewall Policy > Create New

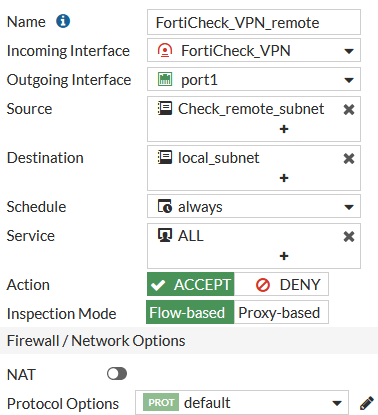
First for the traffic going to the VPN-Tunnel from the Port of your Subnet. In this case, NAT is not required.
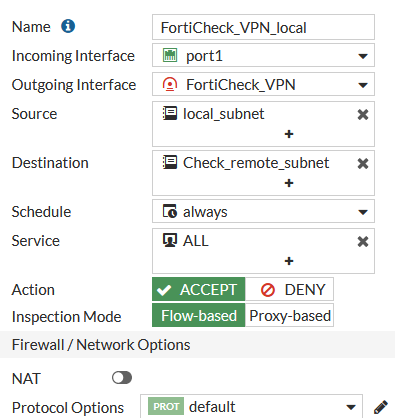
Then for the traffic coming from the VPN-Tunnel going to the Port of your destination Subnet. In this case NAT not required.
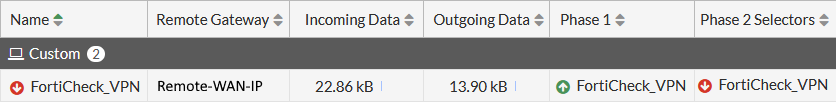
After that, monitor your VPN-tunnel. To check your VPN tunnel health you have to add a new Dashboard-Widget called IPsec
Dashboard > Status > Add Widget

Check the VPN Phase 1 and Phase 2 status:
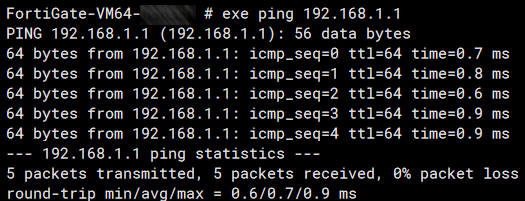
You can then test the connection by sending a ping through it.
Phase 2 should be brought up automatically, provided Phase 1 has been brought up properly.
Let's verify on your FortiGate and Check Point if the tunnel has been established successfully.

In your Check Point SmartConsole, you can easily check your VPN tunnel state with this SmartConsole Extension.

Enjoy!


































