- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Both security gateways are active in the Full HA c...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Both security gateways are active in the Full HA cluster
Hi All,
I have configured two Checkpoint Gateways using GAIA R80.20 and added both security gateways in the Full HA cluster. After configuring the sync interface when I have check the High Availability state using "cphaprob state" command both gateways are appearing as "Active". It is not displaying secondary gateway as "Stand by" gateway. Is there any settings or configuration change required to change the secondary gateway as "Stand by"?
Thanks.
37 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Make sure they are communicating on both Sync and other production interfaces. It looks like a clear split brain situation.
Another guess is that you are not using Full HA but Load Sharing physical cluster instead. In that case, it is normal.
Please post output of "cphaprob stat" command here
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Output of "cphaprob stat"
Gateway 1:
Gateway 2:
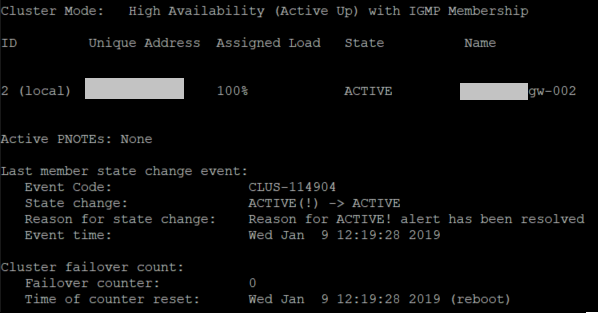
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Okay. It is a split brain. They do not see each other. Are they connected to the same network on at least 1 of the interfaces?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes they both are connected to the same network
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please also post "cphaconf cluster_id" get from both of them
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am using R80.20 and I believe from R80.10 onwards there is a new algorithm introduced which does automatic selection for the MAC magic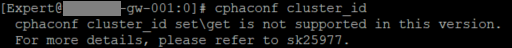
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Okay, need output from each for this:
fw ctl get int fwha_mac_magic
do it from expert shell
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I get this result on both gateways when I run fw ctl get int fwha_mac_magic
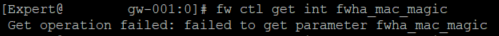
If you are after ClusterXL detail for both gateways then it is shown below:
Gateway 1
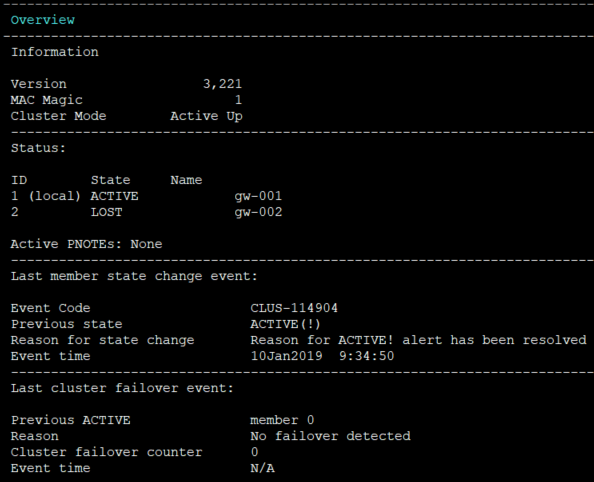
Gateway 2
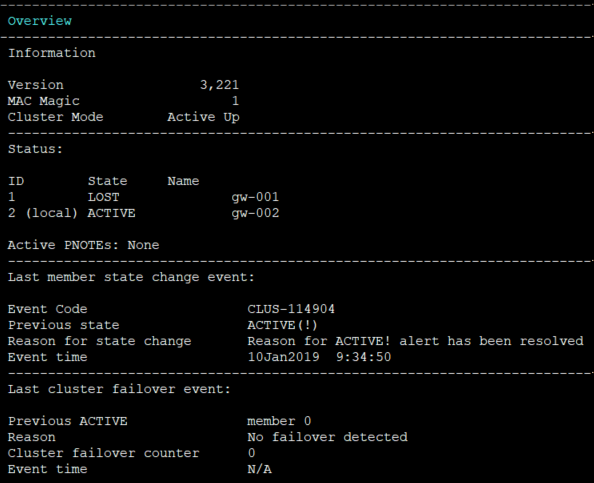
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Are these gateways production appliances? or do you have them setup in test in VM-Ware?
If the latter, please disable all port security features of the switch ports leading to the FW's.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Gateways are not production appliances yet but they will be deployed soon once HA starts working.
Yes they are running in virtual environment and I have disable all port security features but no luck.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I'm having this exact same issue with R80.40 JHF 118 running on a 15000 appliance. This started after an upgrade from r80.20 to r80.40. Any idea how to solve this. Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You have a R80.40 Full Management HA Cluster ? This is a deployment i would not suggest to anybody ! Better contact TAC to resolve this...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Issue solved after rebooting both gateways and installing policy. No we do not have a Full Management HA Cluster.
Thank you for your reply 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Reboot is good 8) ! The original issue was with Full Management HA cluster and you wrote: I'm having this exact same issue with R80.40 JHF 118 running on a 15000 appliance.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The LOST state says - The peer cluster member lost connectivity to this local cluster member (for example, while the peer cluster member is rebooted).
check policy install - fw stat, check the license and cluster membership enabled in cpconfig but it looks like a connectivity issue.
POST: cphaprob -a if, cphaprob -l list
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Currently there are no policies installed as it is new setup. Cleanup rule has been set to allow all traffic. And cluster membership is enabled in cpconfig. It can be connectivity issue but couldn't figure out where the problem will be.

The output of "cphaprob -a if" and "cphaprob -l list":
Gateway 1:
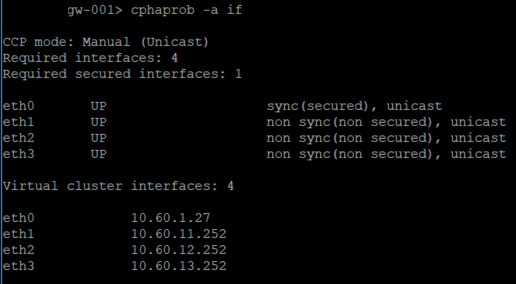
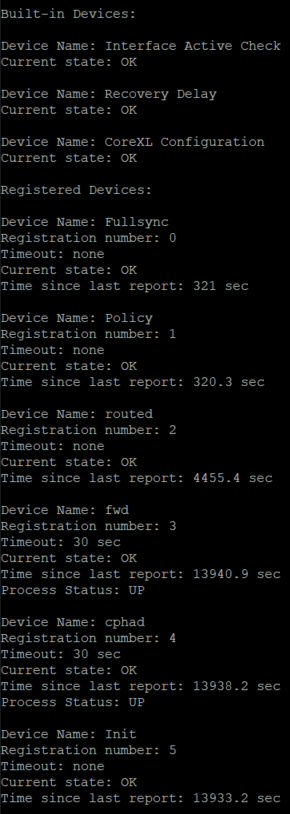
Gateway 2:
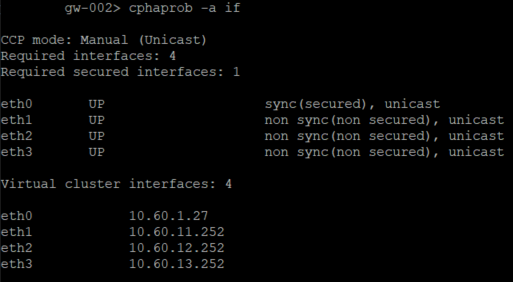
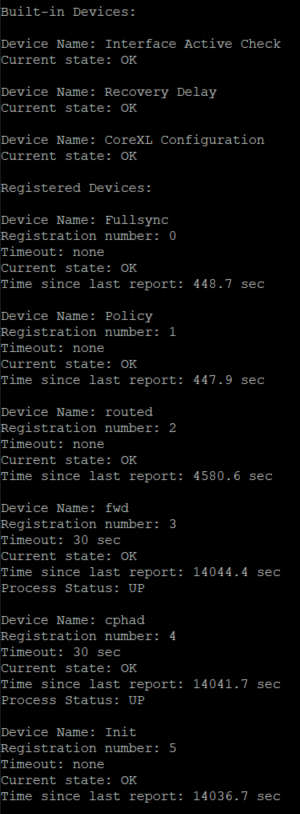
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Okay, that explains it... You need to push policy for cluster to work properly. Before that, any checks are pointless.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have also tested to push the policy for cluster but it didn't help either.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Reboot both members and also check on the Switches if they allow Multicast.
Last but not least check with cpconfig if cluster membership is enabled.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I see policy installed with time and date, and pnote also shows Policy = OK, but try to install one more time, if it helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Have tried to install policies number of times by making different changes but no joy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try to switch to a different mode than unicast, cphaconf set_ccp broadcast, both nodes and reboot.
Send section Sync from fw ctl pstat
And also:
cphaprob syncstat
cphaprob mmagic
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Gateway 1
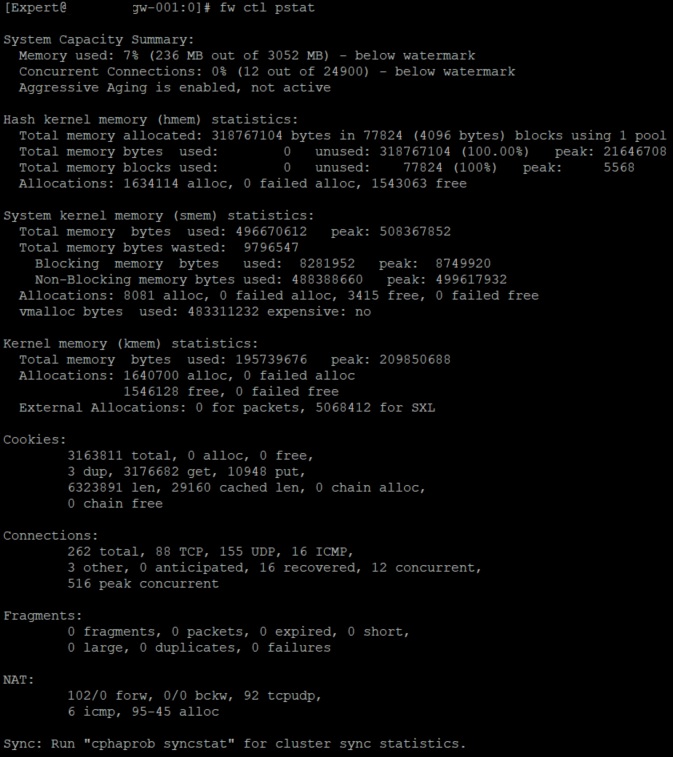
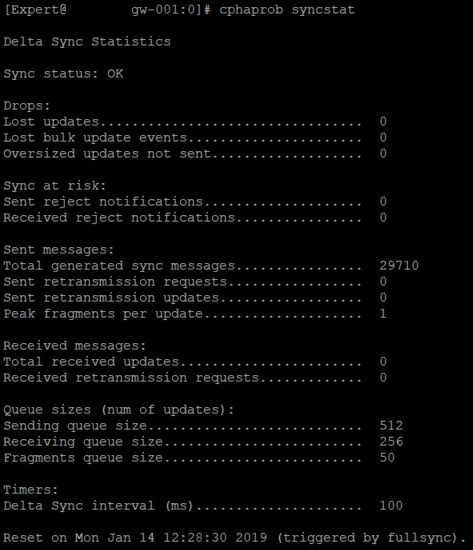
[Expert@gw-001:0]# cphaprob mmagic
Configuration mode: Automatic
Configuration phase: Stable
MAC magic: 1
MAC forward magic: 254
Used MAC magic values: None
Gateway 2
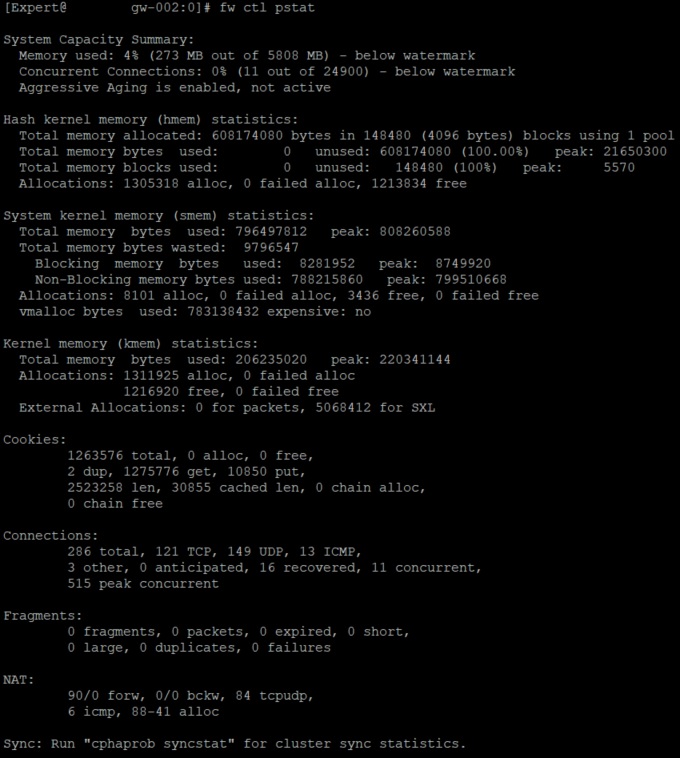
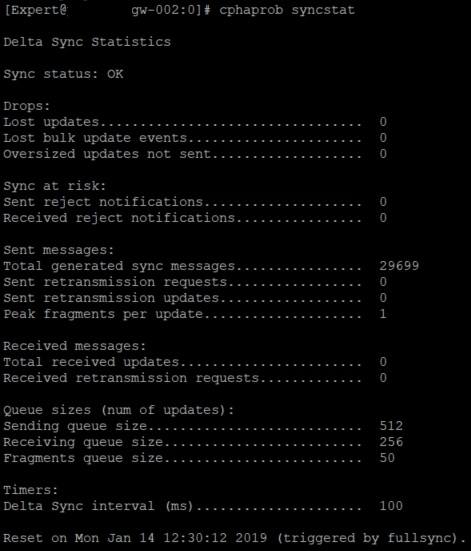
[Expert@gw-002:0]# cphaprob mmagic
Configuration mode: Automatic
Configuration phase: Stable
MAC magic: 1
MAC forward magic: 254
Used MAC magic values: None.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I can not see any issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Pay special attention whether the cluster members are configured identically:
- security policy (
cpstat -f policy fw) - status of SecureXL (
fwaccel stat) - FireWall-1 Chain Modules (
fw ctl chain) - FireWall-1 Connections Modules (
fw ctl conn) - enabled_blades
Else create TAC ticket, because debug is needed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why don't you try to use a dedicated interface for sync? It appears that you are using Cluster + Sync on eth0 and may be that is somehow confusing it?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I did try to use dedicated interface for sync but that didn't help either, I was getting same result.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Muhammad,
Your members don't hear each other. Please check your Sync (eth0) connectivity between members, try to perform ping and tcpdump investigation. Make sure, that you are using L2 connection between your members. Check, that your environment doesn't have duplicate of the IP on the physical interfaces of the members. Check, that the "Get Topology" has been done and policy was installed after it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
the SYNC isn't on L2/L3 at all - those HA members does not "elect" each other respectively hence that wired indeed situation. as other already explained - they do not hear/see each other. that's all.
SYNC must be done on/via VMWare vSwitch/vMotion groups btw. ![]() otherwise as if on Appliances on dedicated int.
otherwise as if on Appliances on dedicated int.
Jerry
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 10 | |
| 10 | |
| 9 | |
| 6 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


