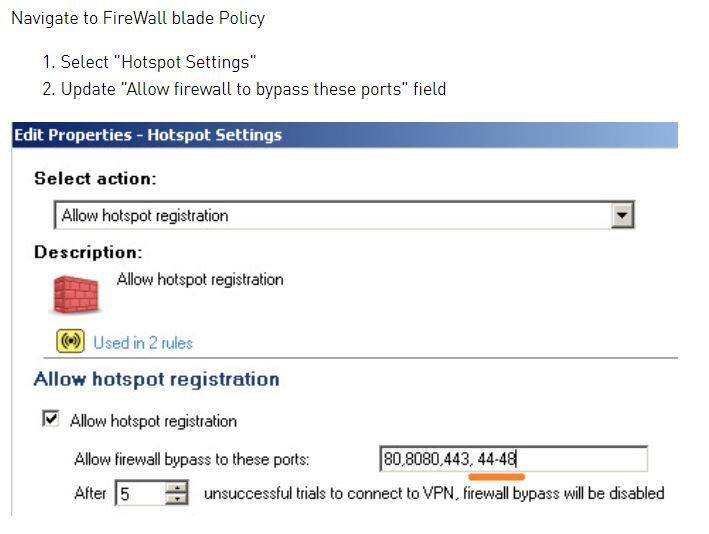
1.) The port-range doesn't work, as PhoneBoy mentioned it should be fixed in R80.40.
For us the solution was to use any port. To get it working you need to add any in the SmartEndpoint policy on the Hotspot Settings (Policy -> Allow hotspot registration). I have tested this solution and it is working fine.

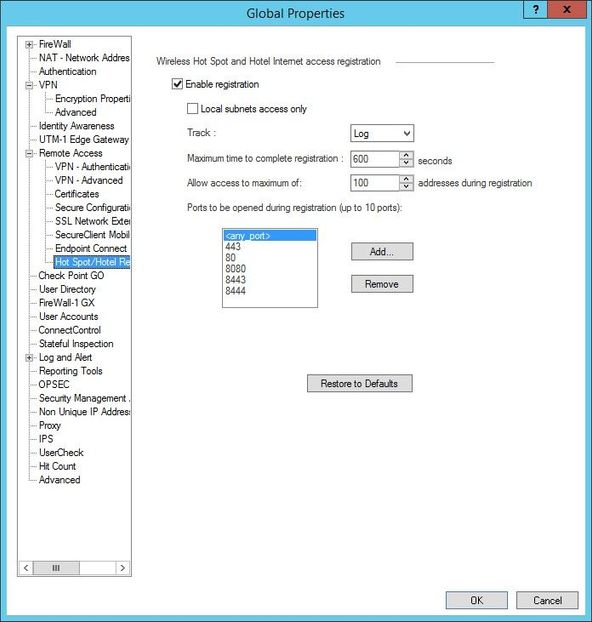
Although, if you check the trac.config file on the client side, the ports that are configured for the hotspot are the ones that are defined in the Global Properties on the gateway (not the ones from SmartEndpoint). But, apparently they are not applied, the configuration from the SmartEndpoint is the one that is applied (in our case any port).
trac.config:
<PARAM fw_hotspot_ports="22"></PARAM>
<PARAM fw_hotspot_ports="443"></PARAM>
<PARAM fw_hotspot_ports="80"></PARAM>
<PARAM fw_hotspot_ports="8080"></PARAM>
2.) Also, to answer the second question. It is enough to define the hotspot policy in the SmartEndpoint console. You can have the option on the Global Properties checked or unchecked, it won't make any difference as long as you are using SmartEndpoint. I tested it both ways, and SmartEndpoint configuration overrides the Global Properties.
In fact, we got the response from TAC regarding this second question and they said it depends if you enforce the Endpoint Firewall policy or the Desktop Policy from SmartConsole (as per sk105644). But, I have tried both options and they don't affect the hotspot registration settings. For us it always remained the one configured in the SmartEndpoint (testing was conducted with re-creating the VPN sites).