- CheckMates
- :
- Products
- :
- CloudMates Products
- :
- Cloud Network Security
- :
- Discussion
- :
- after a cluster failover (Cloudguard) the VPN tunn...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
after a cluster failover (Cloudguard) the VPN tunnel gets disconnected
We have a vpn tunnel between two cluster, one is a pair of OpenServers and the other Cloudguard in Azure.
For the one on OpenServers the gateways are running R80.40. The gateways in Azure we just updated to R81.10.
Since the upgrade when there is a failover in the Cloudguard cluster, the VPN doesn’t work anymore. A quick fix to get it back seems to be re-installing the policy.
Last time we noticed in SmartView monitor the status of the VPN was Up-Phase1. Anyone seen something like this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How long does the outage last when you failover? I remember we had similar issues with our CloudGuard cluster on failover, where it would cause up to a 5 minute outage to our on-prem cluster. The failover would eventually complete and the tunnel would re-establish.
Did you get this issue when your CloudGuard cluster was running another OS version?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Depending on the Azure API the failover time should be ~ 2 minutes for VPN scenarios.
- Are both clusters under the same management i.e. is either defined as an Interoperable device object?
In R81 and above we changed the tunnel keep alive to DPD by default for 3rd party devices... refer sk108600 scenario 5.
- Also is keep_IKE_SAs configured?
This property is available under Global Properties -> SmartDashboard Customization -> Advanced Configuration -> VPN advanced properties -> VPN IKE properties.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So here are some additional details.
We experienced the issue only after upgrading to R81.10.
The participating gateways are two clusters. One is Checkpoint R80.40 running on OpenServers. The other is Checkpoint R81.10 on Cloudguard (Azure).
They are managed by the same management server running R81.10.
The cluster failover happens fairly quickly but as far as I know the VPN tunnel stays down indefinitely. Until we install the Policy which seems to kick in something and make it works.
Keep_IKE_SAs is configured.
I looked at SK108600 scenario 5, should we use DPD over Tunnel_Test even with all members being CheckPoint?
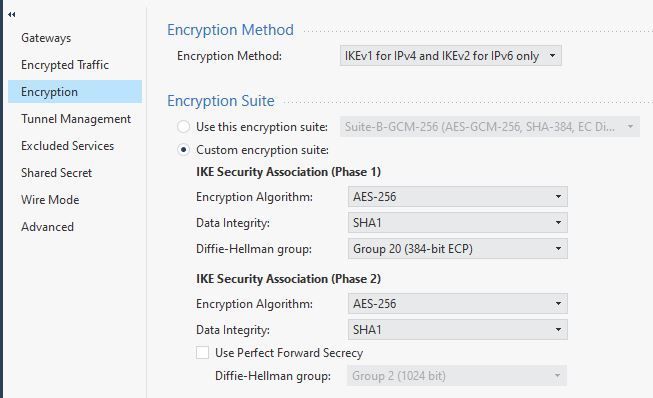
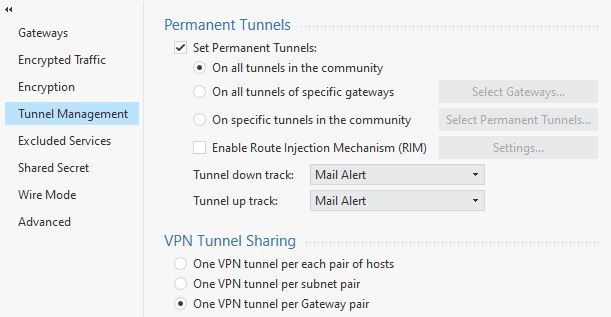
It’s a Meshed VPN tunnel. With the following properties