- CheckMates
- :
- Products
- :
- CloudMates Products
- :
- Cloud Network Security
- :
- Discussion
- :
- Re: UDP through Azure Load Balancer as part of Clo...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
UDP through Azure Load Balancer as part of CloudGuard VMSS
Hi,
I have deployed a standard Scale Set, CloudGuard R81.20
TCP traffic works fine, for example outbound https to internet is NAT-ed correctly and connects ok.
However, I can't send UDP traffic to the internet. For example, ntpdate 0.pool.ntp.org
I logged a case with TAC. They confirmed UDP traffic is leaving the Check Point gateway correctly and suggested I open a case with Microsoft. I'm not in a position to do this.
The load balancer is the standard backend-lb deployed by the Azure Marketplace solution. The loadbalancer rule is the standard "HA" one (all ports, all protocols) deployed in the same way.
I tried separating into a TCP LB rule and a UDP lb rule. This did not help.
I have reproduced the issue in a freshly built test environment.
Any help/suggestions appreciated.
Cheers
Andrew
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
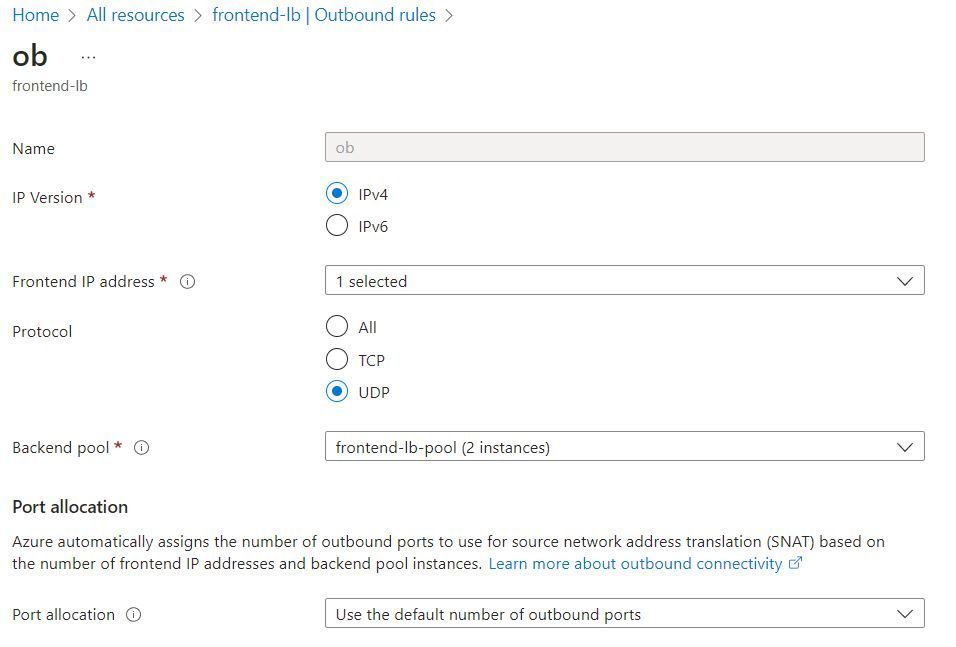
On the "frontend-lb" created by the Check Point CloudGuard deployment scripts, adding an "Outbound rule" of protocol UDP got outbound UDP working correctly.
I think the logic here is that outbound SNAT for TCP is automagically created because the deployment script creates an example inbound NAT rule, however as there is no example UDP inbound rule, there is no corresponding automagic UDP outbound SNAT rule created. Creating an outbound rule for UDP corrects this. I also tried creating an inbound UDP rule (similar to the example TCP one) instead of an outbound UDP rule, however this did not work in my case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is likely caused by a networking issue in Azure if the traffic is leaving the gateway correctly.
In which case, you will have to troubleshoot the issue there (possibly with Microsoft's help).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
On the "frontend-lb" created by the Check Point CloudGuard deployment scripts, adding an "Outbound rule" of protocol UDP got outbound UDP working correctly.
I think the logic here is that outbound SNAT for TCP is automagically created because the deployment script creates an example inbound NAT rule, however as there is no example UDP inbound rule, there is no corresponding automagic UDP outbound SNAT rule created. Creating an outbound rule for UDP corrects this. I also tried creating an inbound UDP rule (similar to the example TCP one) instead of an outbound UDP rule, however this did not work in my case.