- CheckMates
- :
- Products
- :
- CloudMates Products
- :
- Cloud Network Security
- :
- Discussion
- :
- The Workshop - AWS Gateway LoadBalancer & CloudGua...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
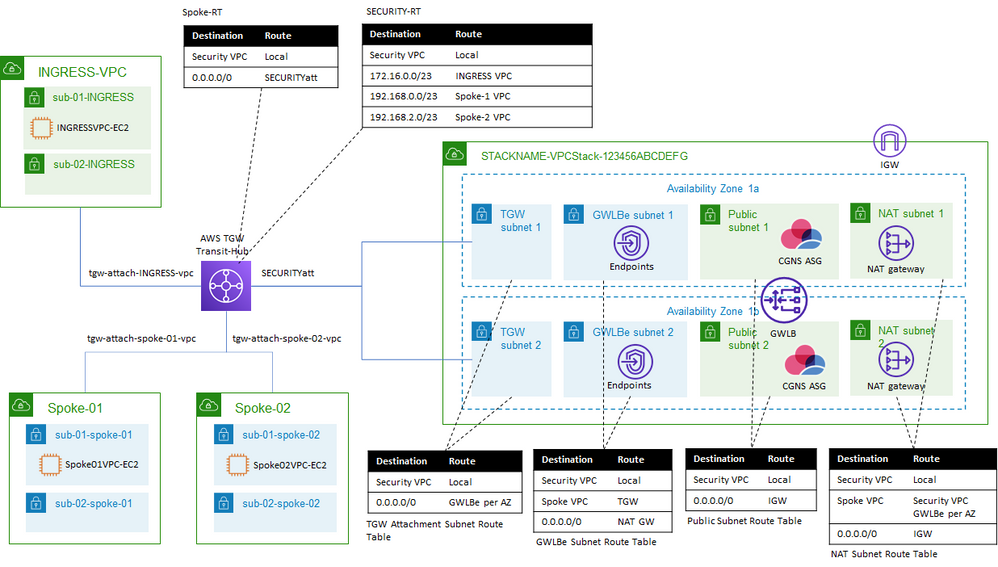
The Workshop - AWS Gateway LoadBalancer & CloudGuard Network
Do you want to learn how to build a state-of-the-art enterprise scalable network architecture on AWS?
Join me for a 2.5 hands-on workshop.
I will provide you with an AWS account and will walk you through a step-by-step process of building the below architecture from scratch.
*** Each Workshop will be closed for registration after 20 users ***
APAC - Apr 12, 2022 12:00 PM Singapore - Register Here
AMERICA - Apr 13, 2022 09:00 AM Pacific Time (US and Canada) - Register Here
EUROPE - Apr 14, 2022 10:00 AM London - Register Here
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Shay_Levin,
Great!! i have some questions about integration with AWS Transit Gateway VPN from On premise..I've been working with a customer in GWLB CHKP and i have some issues about East-West Inspection with AWS VPN traffic the Check Point in AutoScaling GWLB cannot see that traffic because in the TGW will have the decision for that inspection when associate and propagate Routes and VPC to BGP for On Premise VPN.
I have two TGW Route table first one is for Inbound and the second one is for Outbound. Well we will see in production environment.
I'll be in that workshop.
Best regards,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Shay_Levin,
will this workshop open in this year again?
how can the CGNS work with the incoming traffic ? what if the CGNS behind the EIP, NLB and ALB? what will be the architecture ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
for this scenarios, there is some architectural designs that could work.
- Inspection or the real source happens in the GW
- for this you should use Ingress Routing, deploying the Public Facing resource in it's own subnet and within a VPC with IGW, then associate an IGW route table (Edge association) that will send the Public Facing Subnet CIDR block to the relevant GWLB Endpoint per AZ, this is useful when you want to apply security to control de source or in directly attached PIP on EC2 Instances, the subnet where the public facing resources are deployed needs to point reply to GWLB Endpoint.
- Inspection happen after the ELB and could be in clear packet
- When you deploy ELB (NLB or ALB) and the targets are in other VPC (like deploying the ELB in a Subnet where the Check Point are and the Targets are in a VPC attached by the TGW) the default behavior is to SNAT the packet by the ELB private IP, so you can apply a Route Table that will send all RFC1918 or the VPC CIDR into the GWLB (like the one that you're using for the NATGW already), this will show to the Check Point just the IP address of the ELB as source, but allows you to add TLS termination in the NLB or ALB, making the GW able to Deep Packet Inspect the flow, you can apply the Firewall policy directly in the SG associated to the ELB.
hope is clear, if not, please let me know to clarify any doubt.,