- CheckMates
- :
- Products
- :
- CloudMates Products
- :
- Cloud Network Security
- :
- Discussion
- :
- HTTPS Certificate usage in Azure ApplicationGW & C...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HTTPS Certificate usage in Azure ApplicationGW & CheckPoint VMSS
Dear CheckMates,
Requesting for suggestions on below:
I have CheckPoint VMSS in Azure and below the topology setup:
Internet == AzureApplication GW (as Layer-7 LB) === Checkpoint VMSS === Internalserver
I hosted my company website "www.abc.mycompany.com" in Internal server and need to access from Outside via AzAppGW IP
I have Wildcard certificate (*.mycompany.com) issued by GeoTrustRSA and using in Internalserver.
1) In CheckPoint Object HTTPS tab - Which Certificate can I use?
(a) (Shall I import Company Wildcard certificate or Self-signed created by CheckPoint VMSS)
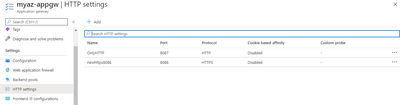
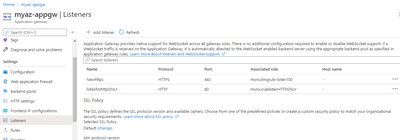
2) In Azure Portal of AzureApplicationGateway - in 2 places HTTPS certificate needs to be used.
b) HTTP Settings Tab = in .cer format
c) Listeners Tab = in .pfx format
3) I also want CheckPoint VMSS to do Outbound Inspection with this Wildcard Certificate
(as per sk113125 Wildcard should not be used for Outbound Inspection by CheckPoint)
(I cannot use this CheckPoint self-signed certificate onto Internal server due to some limitation)
Please correct me if I'm wrong on below:
a) Create & use Self Signed certificate on CheckPoint VMSS Object HTTPS Tab
b) In Azure AppGW - HTTP Settings Tab = in .cer format = Create Self-signed Certificate of CheckPoint VMSS and use here. (Because For AzureApplicationGW - The backend pool is VMSS and it needs VMSS self-signed certificate to identify)
c) In Azure AppGW - Listeners Tab = in .pfx format (Use Company Wildcard certificate)
(Since AppGW will be listening on HTTPS port it needs Wildcard or Server Certificate)
Regards, Prabu
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Outbound HTTPS Inspection cannot be done with a wildcard certificate.
As we are generating certificates on the fly, the key you import for this purpose must be a Certificate Authority key.
No getting around that.
For the inbound portion it depends on two things: what the gateway itself will offer on connection (that’s really depends on what VMSS “expects”), and what the server ultimately being connected to will offer (the CA of that certificate must be trusted by the gateway).
I’ve never configured this in Azure before, so I don’t know the precise steps, but that’s logically how it would work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello PhoneBoy,
Thanks for your inputs. Let me try again configuring.
Regards, Prabu
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Team,
Anyone had accomplished the below or any suggestion:
Internet == AzureApplication GW (as Layer-7 LB) === Checkpoint VMSS === Internalserver
1) AzureAPPGW has Backend Pools which is Checkpoint VMSS
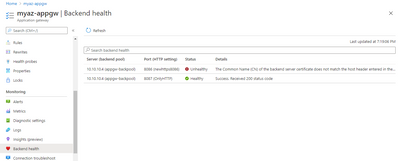
2) Able to get Success for HealthProbe in HTTP, but not for HTTPS
Regards, Prabu
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Team,
I had made success setup and working with HTTPS..
In HTTP Setting for 443 - i used Known CA and did few changes in success codes.
Now VMSS is giving Backend Health as SUCCESS and works good.
Regads, Prabu