- CheckMates
- :
- Products
- :
- CloudMates Products
- :
- Cloud Network Security
- :
- Discussion
- :
- Re: ESG Labs Validation Report: Advanced Security ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ESG Labs Validation Report: Advanced Security with CloudGuard IaaS
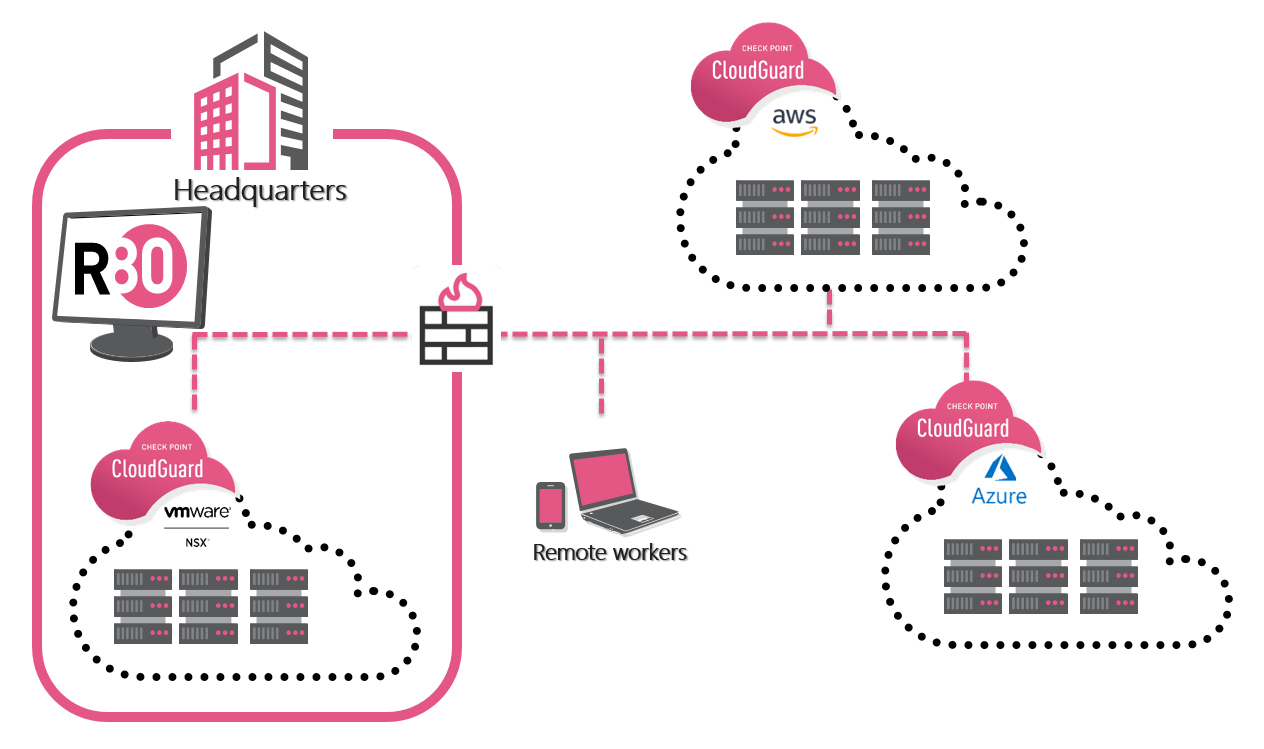
A few months back we had ESG (Enterprise Strategy Group) come to our labs in San Carlos to validate our CloudGuard IaaS core value propositions around adaptive security, agile and automated deployments as well as unified visibility and control. They leveraged our hybrid environment comprised of a VMware NSX SDDC front ended by a Check Point 5800 perimeter gateway allowing connectivity to AWS and Azure public cloud environments. We had prepared Ansible scripts to showcase the automatic deployment and configuration of CloudGuard gateways in both AWS and Azure including policies and VPN configuration.
Please download a copy of the report to learn more.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The problem with this design is the network throughput capacity. For traditional Enterprise data centres Check Point recommends appliances with 30 Gbps Firewall Production Throughput . However, in cloud deployments Check Point suggests firewall VMs with 1-2 Gbps of throughput. It's clear the design will work only for businesses who migrated 5-10% of their workload to cloud. If you migrate more than that the design won't work I'm afraid.
Check Point Security Appliances Comparison | Check Point Software
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Constantine,
When thinking and talking about public cloud, we need to think differently. We need to think automation and scale (i.e. having more smaller gateways as opposed to a single large gateway). We have auto scale templates in Azure and AWS that do just that and noted in the report: "the template enabled this CloudGuard instance to automatically scale, leveraging AWS’s native Auto Scaling features,without the need for the user to add more gateways" manually.
Have a look at the Cloud Security Blueprint as well.
Cloud Security Architecture Blueprint
Regards,
Glenn


