- CheckMates
- :
- Products
- :
- CloudMates Products
- :
- Cloud Network Security
- :
- Discussion
- :
- Cluster HA (Azure) with Multiple VIP - NAT for int...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Cluster HA (Azure) with Multiple VIP - NAT for internet egress
Hello everyone!
I am developing a lab (that if everything goes well will become a customer project), in this lab I am deploying an Azure HA Cluster with the Multiple VIP option.
In my cluster, I have chosen to deploy the firewalls with 3 VIP, that is, my "default" VIP + 2 additional VIP.
I can do the exposure of some test servers that I have in Azure, this through Azure FrontEnd LB rules that deploy the cluster template + firewall rules + "inbound" NAT rules.
However, if I try to make NAT rules of type "Outbound" so that my test servers can go out to the internet through any of the VIP (either the default VIP or any of the 2 additional VIP), I can only go out to the internet with my servers if I make an automatic Hide NAT from the Check Point object that represents the server with the private IP (backend subnet in Azure).
When I do this, my test server can browse the internet using the "default" VIP of the HA cluster.
But, if I try to make this Hide NAT rule "Outbound" manually and setting the default VIP or any of the other 2 VIP as "Translated Source", my server cannot browse the internet.
- HA cluster and test servers are on separate VNETs/subnets.
- HA cluster VNET and test server VNET are interconnected through peerings.
- The routing tables (UDR) of my servers have only two routes, a "local" route for the servers to reach any other server on the same subnet and a "default" route for everything it does not know (0.0.0.0.0/0) to send to the Backend LB (and for the Backend LB to send the traffic to inspection with the firewalls).
- Cluster HA and SMS for this tests are in R81.20
Would I have to do any additional configuration in Check Point to achieve this desired configuration with the OutBound Hide NAT where I decide which VIP the server needs to browse the internet?
Any additional configuration in Azure?
I hope I have explained myself, if any additional data is needed, I will gladly share it with you.
Greetings to all! I hope you can help me.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @yairra ,
I am very grateful, the comments you shared with me were the solution to my problem, thanks a lot!
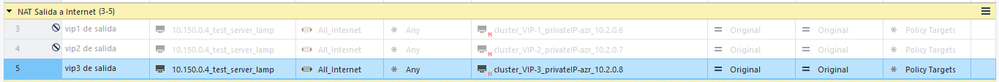
I tried creating a couple of manual Hide NAT rules, using the VIP of the cluster; using the private IPs of the active cluster member in Azure, i.e. (for example):
IP 10.2.0.6 (private IP for VIP) - Public IP 172.212.126.209
IP 10.2.0.7 (private IP for my second extra VIP) - 172.212.126.218
IP 10.2.0.8 (private IP for my third extra VIP) - 172.212.127.24
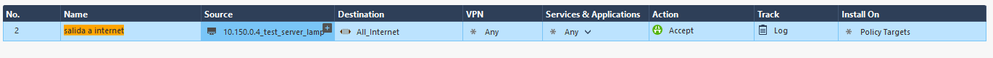
I attach some images of the configuration for firewalls rules and Hide NAT
After these configurations, I was able to go out to the internet with the test server using the Hide NAT of my choice, for example:
-If I used Hide NAT 1, I was able to exit to the internet with the public IP 172.212.126.209.
-If I used the Hide NAT 2, I had access to the internet with the public IP 172.212.126.218.
-If I used Hide NAT 3, I had access to the Internet with the public IP 172.212.127.24.
This was the definitive solution, thank you very much!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @israelsc ,
You can set the automatic Hide NAT of the relevant subnet to hide behind IP address instead of behind the gateway,
In the IPv4 address field use the Private IP Address of your preferred VIP,
You can find the Private IP Address of a VIP under the IP configuration section of the active member's external NIC (in Azure portal).
Feel free to contact if you need any assistance 🙂
Thanks,
Yair.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @yairra ,
I am very grateful, the comments you shared with me were the solution to my problem, thanks a lot!
I tried creating a couple of manual Hide NAT rules, using the VIP of the cluster; using the private IPs of the active cluster member in Azure, i.e. (for example):
IP 10.2.0.6 (private IP for VIP) - Public IP 172.212.126.209
IP 10.2.0.7 (private IP for my second extra VIP) - 172.212.126.218
IP 10.2.0.8 (private IP for my third extra VIP) - 172.212.127.24
I attach some images of the configuration for firewalls rules and Hide NAT
After these configurations, I was able to go out to the internet with the test server using the Hide NAT of my choice, for example:
-If I used Hide NAT 1, I was able to exit to the internet with the public IP 172.212.126.209.
-If I used the Hide NAT 2, I had access to the internet with the public IP 172.212.126.218.
-If I used Hide NAT 3, I had access to the Internet with the public IP 172.212.127.24.
This was the definitive solution, thank you very much!