- CheckMates
- :
- Products
- :
- CloudMates Products
- :
- Cloud Network Security
- :
- Discussion
- :
- CloudGuard Cross AZ Cluster AWS - duplicate second...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
CloudGuard Cross AZ Cluster AWS - duplicate secondary private IP of external interface
Hi, I am building R81.20 CloudGuard Cross AZ Cluster.
Used template in sk111013 (new VPC, R81.20, cross availability zone cluster for transit gateway) stack deployed ok.
At steps to create cluster in Smart Console and push policy to it
Step 11, add an alias interface, in AWS console the secondary private IP address of both cluster members is the same
Although the cluster configuration was able to be published with the same IP address on both cluster members I was not able to install policy, with error "check point duplicate keys "<0a030a1d>" in table 'cluster_members_ids_by_ips'"
If someone could confirm that the 2 cluster members are meant to have the same secondary private IP of external interface, that would help provide a starting point for troubleshooting the policy install error.
Cheers
Andrew
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@AK2
The issue was resolved
Templates with the fix published and are available in:
- https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
- https://github.com/CheckPointSW/CloudGuardIaaS/tree/master/aws/templates
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Update. I reset SIC on gateways and manager, deleted the Cluster Object in Smart Console, went through the config one more time. I reproduced the policy push error, however this time was able to work past it by deliberately setting the second cluster member's secondary private IP of external interface so that it did not conflict with the first cluster member (ie something different to what the AWS stack says it is). Doing this allowed me to push policy and the cluster is now in a healthy state...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @AK2
Thanks for reporting the issue . We are checking it
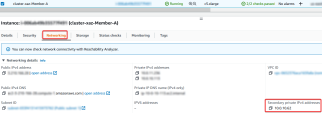
Meanwhile the you may refer to instructions in admin guide on how to find secondary external private IP address
Configure Member IPs: Enter secondary private IPv4 address of external interface for each cluster member and click OK.
To get the IP address in AWS console:
In AWS Console chose Cluster member > Navigate to the Networking tab.
Thanks,
Roman
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@AK2
The issue was resolved
Templates with the fix published and are available in:
- https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
- https://github.com/CheckPointSW/CloudGuardIaaS/tree/master/aws/templates
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
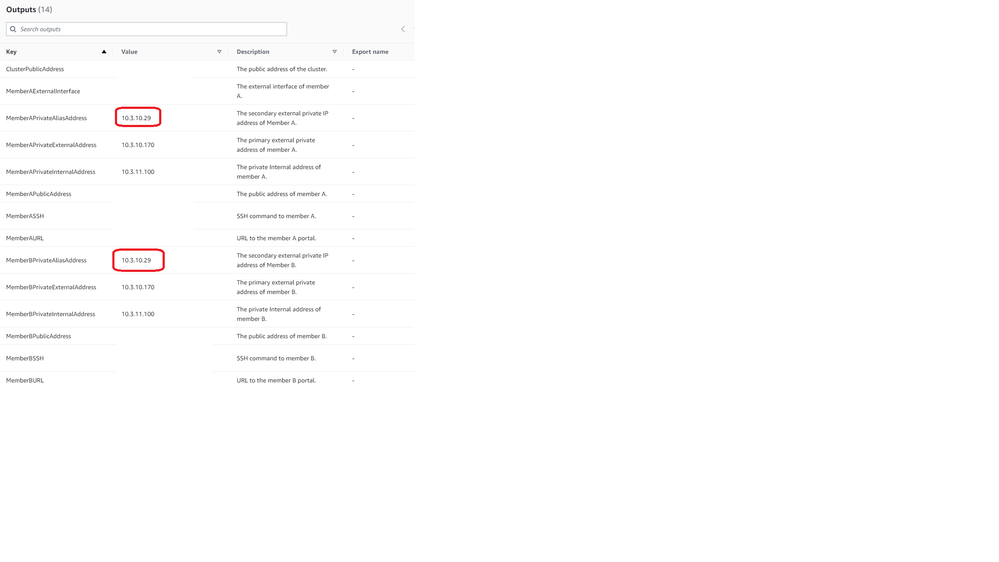
Hi Roman, thank you so much for resolving this issue so quickly during the holiday season, it means a lot for me and my customer! I redeployed today and the new secondary IPs are different for each member. I was able to create the cluster in Smart Console and push policy to it. For the benefit of others here are the private IPs assigned during stack creation:
ClusterPublicAddress |
| The public address of the cluster. |
MemberAExternalInterface | The external interface of member A. | |
MemberAPrivateAliasAddress | 10.4.10.75 | The secondary external private IP address of Member A. |
MemberAPrivateExternalAddress | 10.4.10.137 | The primary external private address of member A. |
MemberAPrivateInternalAddress | 10.4.11.145 | The private Internal address of member A. |
MemberAPublicAddress | The public address of member A. | |
MemberASSH | SSH command to member A. | |
MemberAURL | URL to the member A portal. | |
MemberBPrivateAliasAddress | 10.4.20.34 | The secondary external private IP address of Member B. |
MemberBPrivateExternalAddress | 10.4.20.208 | The primary external private address of member B. |
MemberBPrivateInternalAddress | 10.4.21.45 | The private Internal address of member B. |
MemberBPublicAddress | The public address of member B. | |
MemberBSSH |
| SSH command to member B. |
MemberBURL |
| URL to the member B portal. |
Cheers, Andrew