- CheckMates
- :
- Products
- :
- CloudMates Products
- :
- Cloud Network Security
- :
- Discussion
- :
- AWS CloudGuard Monitoring - CloudWatch
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
AWS CloudGuard Monitoring - CloudWatch
Hello Guys
These is one idea for monitoring your "VPC Security" deployed with CloudGuard devices, use "AWS CloudWatch". Its very simply.
cloudguard vsec aws
- Tags:
- cloudguard
- vsec aws
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Luciano,
Would you mind showing the configuration steps that you've had to go through in order to implement this?
There was another discussion earlier regarding logging to CloudWatch: https://community.checkpoint.com/message/16943-re-log-exporter-guide?commentID=16943#comment-16943
I am interested to know what other metrics it is possible to collect and process without parsing the logs from the CloudGuard.
Thank you,
Vladimir
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Vladimir sure , I used the vpn metrics available in cloud watch , and CPU of ec2 CloudGuard instances .
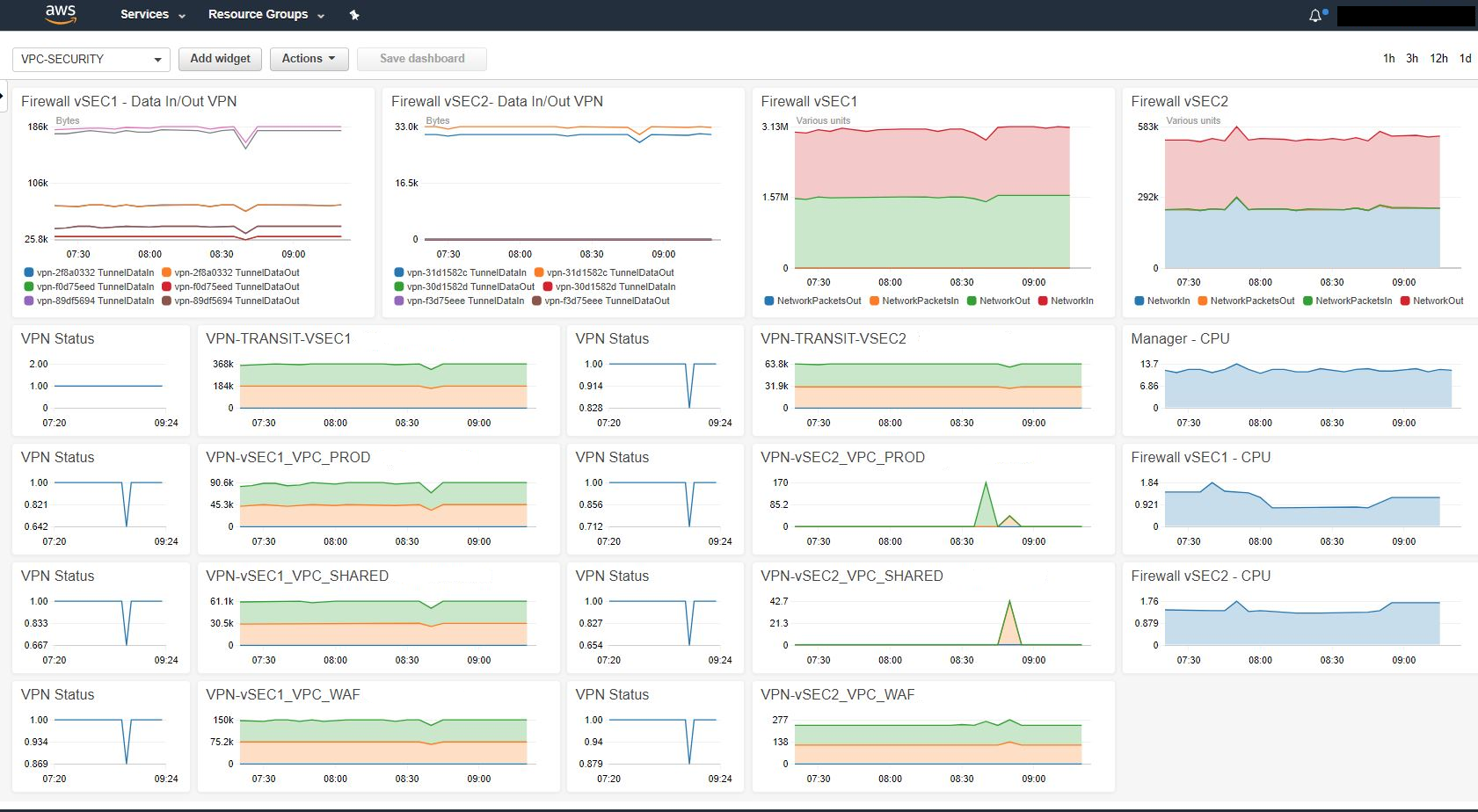
These environment have two vpcs Transit and Security with Vpn connection on both sides , see picture . And another vpcs behind the security vpc.
From these dashboard we can see vpn status, CloudGuard health and tunnels traffic .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Luciano,
Thank you for replying.
When you are saying "see picture", are you you referring to the original metrics screen or were you planning to include a sketch of a diagram?
Also, please let me know if the "vpn metric available in cloudwatch" requires VPC flow configured to recognize the VPN traffic, or is it capable of doing it naively.
I suspect that the cloudwatch can recognize the VPN traffic, but it should not be able to differentiate between multiple VPN tunnels terminating on the same vSEC gateway without tighter integration with CP APIs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Vladimir,
Let me explain better, I was talk about the first diagram, and my environment is distributed with below:
OnPremises AWS Cloud
MyDatacenter <> Direct Connection Links <> AWS Transit VPC <> AWS Security VPC <> Spoke VPCs
The Dashboard showing the connections VPNs between VPCs:
AWS Transit VPC <> AWS Security VPC
AWS Security VPC <> Spoke VPCs
For this reason we can see the VPNs metrics
We do not have external VPNs with CloudGuard ex: site to site vpns. But I believe that is possible include to CloudWatch Dashboard, but required the metrics customization or Flow export.


