- CheckMates
- :
- Products
- :
- CloudMates Products
- :
- CNAPP
- :
- Re: Regarding GCP's disabled firewall rules
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Regarding GCP's disabled firewall rules
Hello.
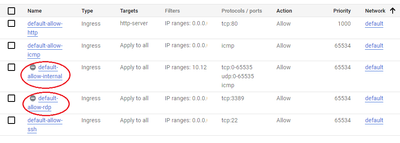
My customer claims that even if he disables the Firewall rules in GCP, they are still detected by CGPM. Indeed, CGPM does not seem to change from the enabled state even if the rule is disabled.
Is this behavior correct?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
The Security Group page UI wasn't modified with all GCP properties, it was done to keep the same concept as AWS and Azure.
To see the actual states you can always use the Compliance engine and the entity viewer that always have the updated information.
I will file a UI ticket to handle it or to add the entity viewer to the Security group so it will be easier to see the data.
Thanks,
Guy Shteinberg
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
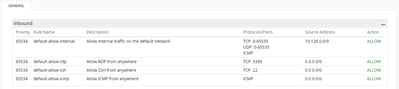
Hi,
I used the entity viewer to verify that the inbound rules for the nics array have an enabled flag. However, the GCP rules do not seem to check for this flag. I think I need to add the condition "enabled = 'ture'" to the GSL, is this unnecessary?
Like this:
VMInstance where nics contain-any [inboundRules contain [ destinationPort<=3389 and destinationPortTo >=3389 and protocol in ('TCP','ALL') and enabled = 'true']] should not have nics contain-any [inboundRules contain [ destinationPort<=3389 and destinationPortTo >=3389 and protocol in ('TCP','ALL')] and inboundRules allowedHostsForPort(3389) > 32]
Thanks,