- CheckMates
- :
- Products
- :
- CloudMates Products
- :
- CNAPP
- :
- Re: New CloudGuard Dome9 integration support: Tena...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
New CloudGuard Dome9 integration support: Tenable.io
The option to integrate Tenable.io has now been added to the CloudGuard Dome9 Posture Management module. With this integration, you can correlate information from Tenable.io and Dome9, to identify the most critical vulnerabilities in your cloud environment.
It can also hel you remediate the risks for your cloud services, using the CloudBots technology, based on severity and reduction of attack surface.
You can include Tenable.io details in enhanced GSL queries, to identify conditions such as the following:
-
what are the public facing instances with High/Mid or Low Severity CVE’s?
-
which web server workload has known CVEs?
-
which vulnerable workloads have we detected in our cloud environment in the last XX days?
Example GSL
Instance where isPublic=true should not have externalFindings.findings contain [ ( findingSource='Tenable.io ') ]
For more details, see here
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
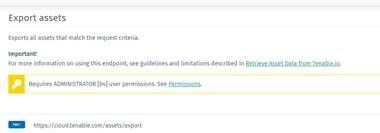
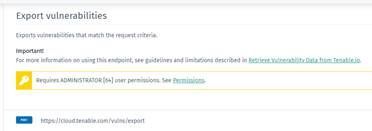
We utilize the export API as required by Tenable according to the following guidelines.
- Tenable documentation states that for integrations with third-party you should use the Tenable Export Apis (https://developer.tenable.com/docs/retrieve-vulnerability-data-from-tenableio)
- They also made sure that we use them before approving the integration
Tenable Export Apis require Admin permissions
Thanks,
Guy Shteinberg
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We are testing the Tenable integration however it states that the admin role is required on the Tenable side. Is this necessary? Dome9 is only pulling CVE results from Tenable's cloud assets inventory so read-only should be sufficient. It doesn't need to initiate a scan, etc. We like to know why Dome9 needs Tenable's admin role before we proceed with the testing. Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
We utilize the export API as required by Tenable according to the following guidelines.
- Tenable documentation states that for integrations with third-party you should use the Tenable Export Apis (https://developer.tenable.com/docs/retrieve-vulnerability-data-from-tenableio)
- They also made sure that we use them before approving the integration
Tenable Export Apis require Admin permissions
Thanks,
Guy Shteinberg
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We have yet to get our Tenable integration working in Dome9. I've been testing with a Windows 2016 AWS EC2 instance with 3rd party and OS vulnerabilities. However still nothing shows up in the alerts as "tenable" source.
What are the requirements on the Tenable side that vulnerabilities are captured and matched with a cloud asset on Dome9?