- CheckMates
- :
- Products
- :
- CloudMates Products
- :
- CNAPP
- :
- A new Ruleset for anomalous outbound network activ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
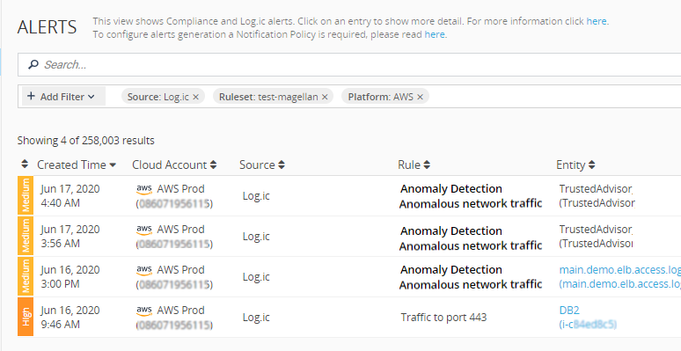
A new Ruleset for anomalous outbound network activity is now included in CloudGuard Log.ic
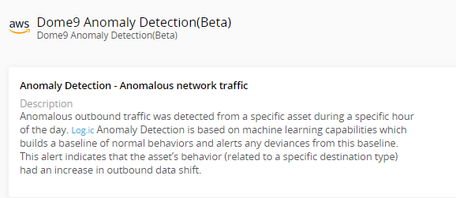
CloudGuard Log.ic has a new Ruleset to check for anomalous outbound network activity, which may indicate an attempt at data theft. The Dome9 Anomaly Detection ruleset can be applied to your AWS cloud accounts, and can identify attempts at data exfiltration or other unauthorized data transfers from your cloud assets, which may expose sensitive enterprise information to outside sources.
To use this ruleset in Log.ic, you apply it to a cloud account in a policy (together with a notification policy, which channels alerts to your preferred target, whether email, or the Alerts page, or a third-party system).
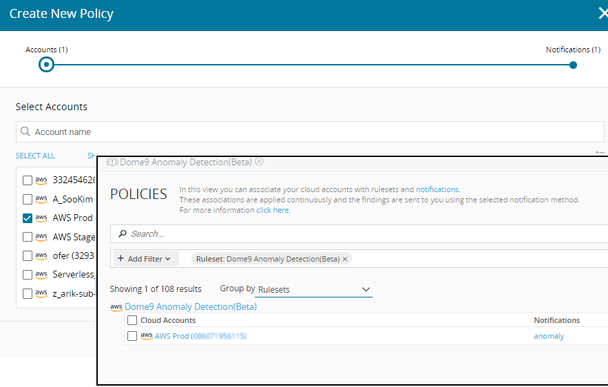
Once applied, Log.ic builds a baseline of normal activity, using ML algorithms to process flow logs and other information. It then applies these algorithms to the flow logs to detect anomalous activities, and generates Alerts when they are detected. These alerts can be in near real-time (as emails), or periodic reports, and contain details of the asset involved, the destination, and the time it occurred.