- CheckMates
- :
- Products
- :
- CloudMates Products
- :
- CloudGuard - WAF
- :
- CloudGuard AppSec - The Full Exception and Manual ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
CloudGuard AppSec - The Full Exception and Manual Rules Guide
Although configuring Web Application security or Web API security is easily done via the configuration wizard, in most cases, assets are fully protected without additional manual changes, thanks to the CloudGuard AppSec learning mechanism.
Why do I need exceptions?
The most common use case of custom rules and exception configuration is when a log is issued and a security administrator decided that traffic matching one of the log fields (for example, the URI field) should not be detected or blocked by the AppSec engine. This is also known as a “false positive”.
Usually, for new traffic that is being blocked because he was not learned yet or because it looks like an actual attack.
How do exceptions work?
A custom rule/exception is a combination of the specific AppSec security practice that caught the original event and the Asset relevant for the same traffic. Once an exception is put in place, the AppSec engine will work according to the configuration:
- Accept - Traffic matching the exception's conditions will be accepted.
- Drop - Traffic matching the exception's conditions will be blocked.
- Skip - Relevant only for specific keys like "Parameter Name", "Parameter Value", and “Indicator”. Allows skipping the value of the matching parameter from being inspected by the AppSec engines. The rest of the traffic will be inspected for malicious behavior.
- Suppress Log - Traffic matching the exception's condition will not activate their Log Trigger object/s upon an event.
How to create an exception?
- Identify the Prevent/Detect log you want to create an exception for.
- For Accept and Skip - make sure that this traffic is indeed legitimate:
- Verify that the source is familiar.
- Verify that the request is legitimate.
- Review the Threat Prevention details and compare the details with the system admin to make sure this transaction is OK.
- For Drop and Suppress Log - make sure that this traffic is indeed malicious.
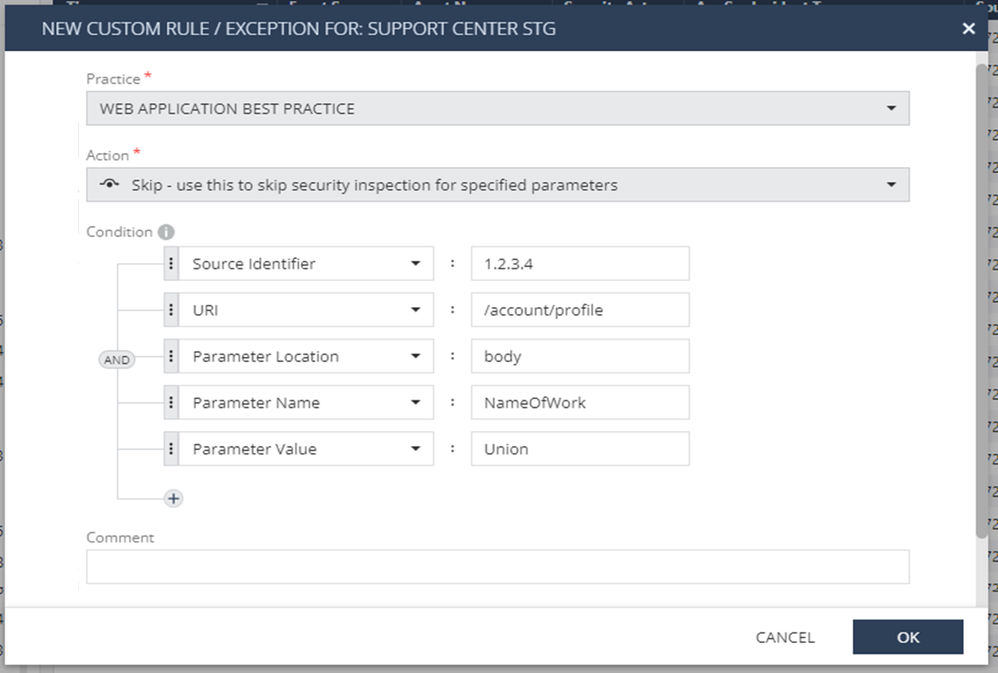
- Right-click on the log and choose “Add Exception”.
- Choose the Action you want to add: Accept / Drop / Skip / Suppress Log.
- Review the automated built-in configuration and adjust the values.
- It’s important to understand the log you are working on in order to create an exception as specific as possible, to act only on the specific parameters shown on the transaction.
- It is possible to create multiple rules containing AND or OR.
- In case the specific parameter is in a unique place in the transaction, you can specify where using “Parameter Location” and then “Parameter Name” and “Parameter Value”.
- Mandatory: Add a comment for this exception.
- Click OK.
List of Keys Possible to Use:
|
Exception Key |
Value String Search Location |
Remarks |
|
Host |
Regular expression of the HTTP Hostname |
|
|
URI |
HTTP full URI in request |
|
|
Source Identifier |
Regular Expression of the identifier, according to the definition of Source Identifier in the Asset's configuration |
|
|
Source IP |
The IP address of the request's source in the IP address or CIDR format (e.g. "<IP address>/<number of bits for network>") |
|
|
Parameter Name |
Regular Expression of a parameter name is key in the HTTP request body's XML or JSON file |
Can be used with the “Skip” action |
|
Parameter Value |
Regular Expression of a parameter value is the value to a key in the HTTP request body's XML or JSON file |
Can be used with the “Skip” action |
|
Protection Name |
The protection name used by the security sub-practice |
For IPS and Snort Rules only |
|
Country Code |
For Geolocation-based exceptions. The country is resolved according to the source IP address. Code is the recommended use for country-based exceptions and can be searched here according to the Alpha-2 code of ISO-3166. |
|
|
Country Name |
For Geolocation-based exceptions. The country is resolved according to the source IP address. The name is less recommended for country-based exceptions but is more readable. Exact names can be searched here according to ISO-3166. |
|
|
File Hash |
SHA-256 string of the file the exception should apply to. |
For File Security only |
|
File Name |
The file name matches the configured exception. |
For File Security only |
|
Response Body Note - Scanning response traffic adds a performance impact. |
Regular expression of a pattern within the HTTP Response Body |
This key allows adding manually Data Loss Prevention (DLP) rules |
|
Indicator |
A regular expression for indicators to be ignored during the inspection. When an exception is set to skip and includes the "Indicator" field, the parameter will not be skipped, and instead, only the matching indicators will be ignored, allowing for other indicators to be detected in the matching parameter. |
Can be used with the “Skip” action |
Examples:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Yuval,
thank you very much for the documentation.
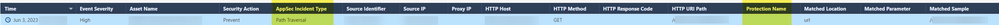
I have one question. I want to exclude a "protection", but if I check the log I only see this...
In this case there is no protection, just an AppSec Incident Type.
I have other logs, with a large list of these cases, no protection name but an AppSec Incident Type, i.e. Cross Site Scripting/SQL injection or both.
So, the question is, how do or can I conditionally or without an condition, i.e. exclude an AppSec Incident Type.
Christoph
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Christoph,
Protection Name shows only for IPS and Snort Rules detections and shows the protection name used by the security sub-practice.
It is also mentioned in the table above 🙂
In general, the best option is to right-click the log, and choose "Add Exception". It will automatically build the exception rule according to the existed parameters.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok, but it's really hard to see the difference between an "IPS pattern" and a AppSec Incident Type. My understanding is, an IPS pattern may include a regex to detect a path traversal or SQL injection.
The auto rule build, in other examples I have will not build working exceptions.
To cut it short. Am I, or will I be able to exclude an AppSec Incident type, like SQL Injection, completely?
I know I will lessen the security by a large amount, but I have a "broken" webapp, I'm aware of the risks and I'm fine with only running the other protections, that do not produce false positives.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
There is no way to create an exception based on the "AppSec Incident Type" field.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Yuval for sharing this content. Its a great insight!!
Blason R
CCSA,CCSE,CCCS