Hello all,
I am working on the script that collects a policy package for the specific gateway (virtual system).
It works very well in the lab but in production environment I noticed the following
behavior.
API call "show-gateways-and-servers" with "details-level full" should return
list of objects. If the object type is equal to "CpmiVsxClusterNetobj" and it is
virtual system there should be "policy" object that contains the key "access-policy-name".
See the example below (the output is shortened):
{
"uid" : "f47b987d-f3d8-4ae2-b5ca-a562c7fd43ef",
"name" : "VS01",
"type" : "CpmiVsClusterNetobj",
"domain" : {
"uid" : "886fb185-487f-4ccf-94f4-ddc8443f6760",
"name" : "DOM02",
"domain-type" : "domain"
},
"policy" : {
"access-policy-installed" : true,
"access-policy-name" : "VS01_POL01",
"access-policy-installation-date" : {
"posix" : 1726439380347,
"iso-8601" : "2024-09-16T00:29+0200"
},
"threat-policy-installed" : false
But in production there are several virtual systems which has the "policy" object empty like in the following example:
{
"uid" : "f47b987d-f3d8-4ae2-b5ca-a562c7fd43ef",
"name" : "VS05",
"type" : "CpmiVsClusterNetobj",
"domain" : {
"uid" : "886fb185-487f-4ccf-94f4-ddc8443f6761",
"name" : "DOM05",
"domain-type" : "domain"
},
"policy" : {
},
"threat-policy-installed" : false
My understanding is that in case a policy package was successfully installed on a virtual system, the "policy" object should not stay empty. Is my understanding correct? Or are there any corner cases when this is not true? Like after MDS server upgrade or after purging all revisions from a domain. To be honest, I have already tested all mentioned corner cases in a lab, but I was not able to simulate the situation with empty "policy" object.
We are using 2x MDS server with version R81.20 Take 76 + 2x MLM. Firewalls are using VSX R81.10 or R81.20. I have noticed that if the "policy" object is empty also "Installation History" shows empty "Access Control Policy" and "Access Installation Date" in SmartConsole application. Like this:
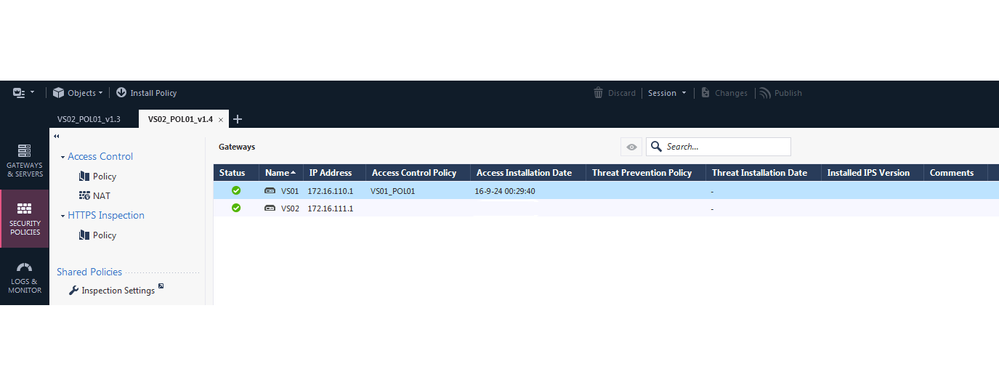
Do you have any idea about this behavior? Is this a bug?
Any suggestions would be greatly appreciated.
Regards,
ZdenekR



