Hi Team
I have been working on automating site2site vpn with a Check Point Gateway and an Interoperable device, and setting up a vpn community.
https://community.checkpoint.com/message/18635-how-to-add-interoperative-device-via-api
The next step my search to complete my use of API is Add my site2site firewall rule to gateway cluster Security policy.
When I use the active example from the API doc it us being published to the standard security profile. I’ve multiple profile to each of my rule set per secure gateway.
I have been able find my security profiles by using commands to extract uid.
https://community.checkpoint.com/message/18729-how-to-find-generic-object-that-is-not-defined-in-the...
And I also had to find out how to extract and set values I dont find any documentation of.
https://community.checkpoint.com/message/18727-missing-api-possibility-to-set-vpn-community-star-obj...
For example how to set ipsec and ike rekey values because Cisco device ASA5506 or Cisco router 1921/1941 have been configured differnetly than default vpn community values as 1440 min, and 86400 sec.
I can publish a firewall rule
#############################
# Add FW rule
#############################
# Name of rule WP-<Parkname>
# source "Hobro_Scada_Internal" & "WP_Gettrup_Internal_Network"
# destination "WP_Gettrup_Internal_Network" & "Hobro_Scada_Internal"
# services "Vestas Park Services"
# vpn-community "WP-Gettrup"
# action "Accept"
# track "Log"
# install-on "gwcluster"
mgmt_cli -u admin add access-rule layer "Network" position 1 name "Windpark Getrrup" source.1 "Hobro_Scada_Internal" source.2 "WP_Gettrup_Internal_Network" destination.1 "WP_Gettrup_Internal_Network" destination.2 "Hobro_Scada_Internal" service.1 "Vestas Park Services" vpn "WP-Gettrup" action "Accept" track.type "Log" install-on "gwcluster"
As you can see it add itself to the security policy [Standard]
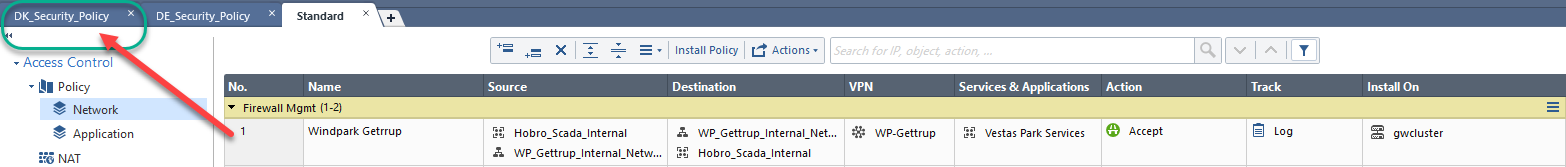
How do I select a security profile by either using the name or uid to publish my new firewall rule?
Thanks
Kim
Best Regards
Kim



