Hello everyone,
I wanted to share with you a tool that we developed to help us automate a big part of a project.
Long story short, we needed to migrate many virtual context from ASA to VSX. As you may know adding static routes and interfaces to a VS can be cumbersome. Especially if you have firewalls with +100 interfaces and +300 routes 😀
The tool was developed in Golang and is open source.
Keep in mind that this tool was developed for our use case, maybe you need to tinker around a bit regarding interfaces names. For example, you may need to replace "bond" with "eth"
Feel free to fork it if you need.
Download: ASAtoVSX Parser - Molten Minds Github
Current features (Tested with ASA Version 9.4(4)5 and Check Point R80.30)
- Translates interfaces to vsx_provisioning_tool language
- Translates static routes to vsx_provisioning_tool language
- Marks with # when an interface is down
- Generates a vsx_provisioning_tool output with interfaces and static routes
- Generates a JSON file containing all the interfaces
- Generates a JSON file containing all the routes
Translation examples
| | ASA | Check Point (vsx_provisioning_tool) |
| Interface | interface Port-channelY.XX
description ***
nameif IFNAME
security-level 30
ip address 172.**.**.** 255.255.128.0
! | add interface name bondY.XX ip 172.**.**.** netmask 255.255.128.0 |
| Interface (Shutdown) | Caso interfaz down
interface Port-channelY.XX
description IFNAME
shutdown
nameif IFNAME
security-level 30
ip address 10.**.**.** 255.255.255.248
! | #add interface name bondY.XX ip 10.**.**.** netmask 255.255.255.248 |
| Static route | route IFNAME 10.**.**.** 255.255.255.255 10.**.**.** 1 | add route destination 10.**.**.** netmask 255.255.255.255 next_hop 10.**.**.** |
| Default route | route OUTSIDE 0.0.0.0 0.0.0.0 181.**.**.** 1 | add route destination default next_hop 186.**.**.** |
Usage
Usage is really simple.
1) Download the executable file from Github or compile the code yourself
2) Extract running config and save it as a text file with UTF-8 format . At the moment the tool only allow inputs in this format.
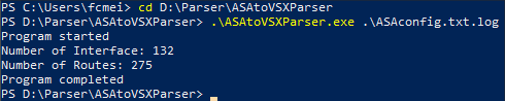
3) Using PowerShell execute the program command with the desired input file.
4) Check the output files
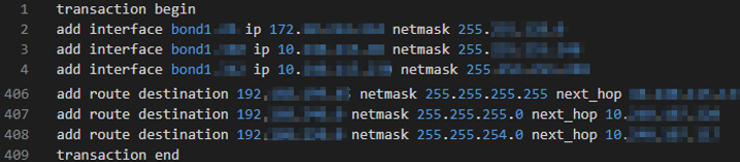
vsx_provisioning_tool sample output
Interfaces JSON output
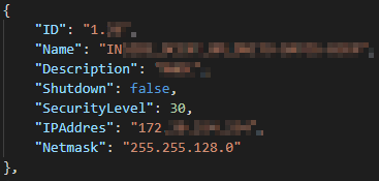
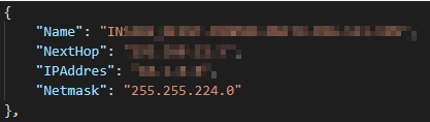
Routes JSON output
5) Add the desired header on the VSX output for vsx_provisioning_tool to create de VS. Example: add vd name VS-Name vsx VSX-FW instances 1 main_ip 172.1.2.3
6) Put the script in the management server that manages the involved VSX and use vsx_provisioning_tool to execute it
7) Verify the new VS and push policy.
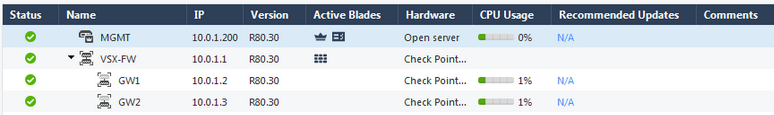
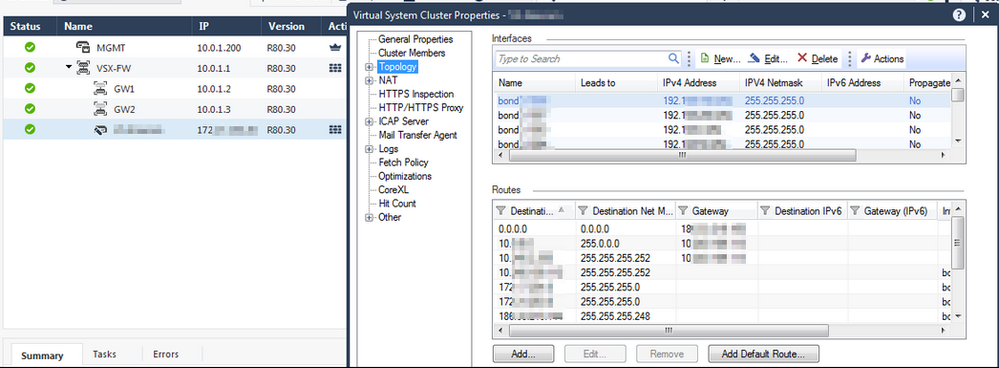
Lab
Sample VSX Lab prior script
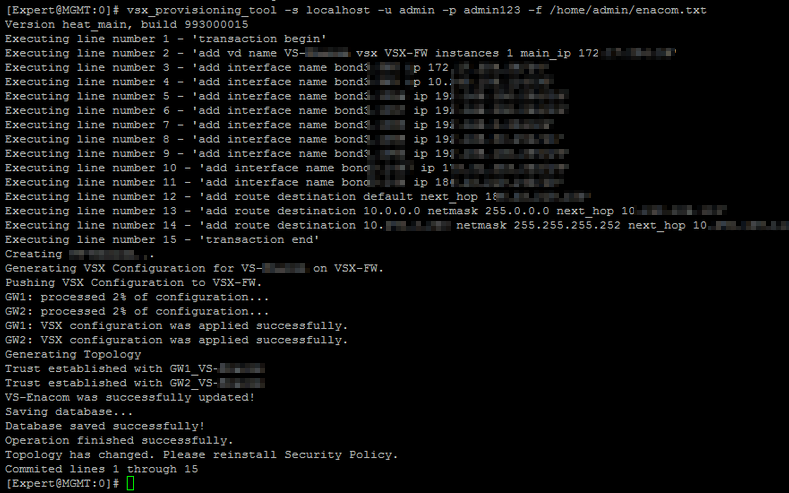
After we move the generated script to the management server we execute it.
If any of the commands fail then the transaction will be canceled and reversed.
User and passwords are for demonstration purposes only 😀
Now check your VS and push policy
____________
https://www.linkedin.com/in/federicomeiners/











