- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Threat Prevention
- :
- Multiple Threat prevention profile in R80.10
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Multiple Threat prevention profile in R80.10
Team,
Can we create Multiple threat prevention profile in R80.10 , One profile with AV & AB blade enabled with prevent action and the other profile is having only IPS enabled .
10 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Libin, yes that should be fine provided you're installing to R80.10 gateways (Pre R80 gateways need to have a dedicated IPS layer).
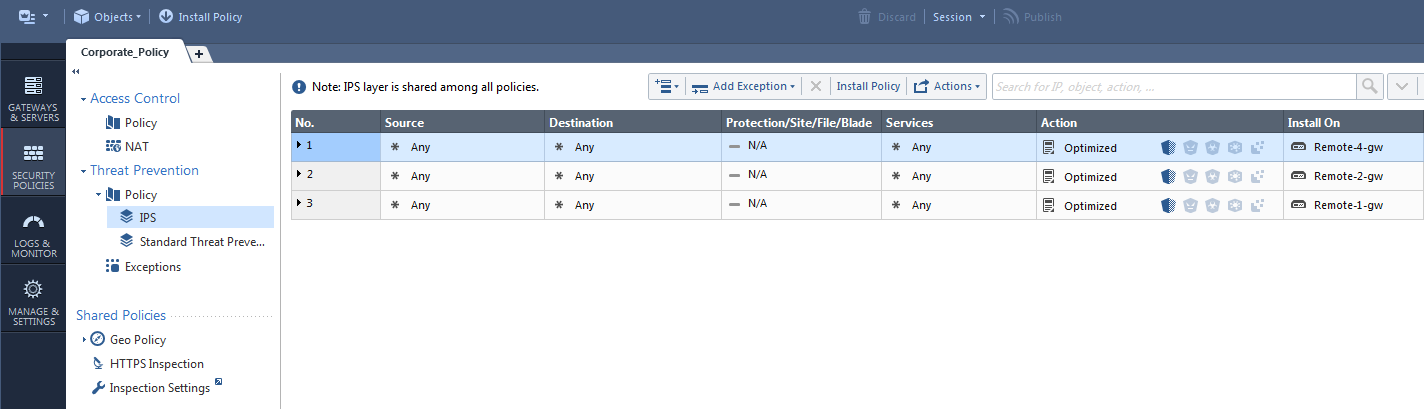
You can configure separate profiles / layers to match however you need to configure your policy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Absolutely:
Clone the Optimized profile twice, rename one clone to ABAV and another to IPSOnly, edit profiles and uncheck not needed blades. Adjust the desired protections.
Create another rule in the Threat prevention policy with edited profiles applied to desired scopes.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey,
i am interested to understand the need for duplicate the profiles....
can you share the reason (even directly by mail)?
two examples for best practices "why you should work with all the blades"
- if you are interested to prevent attacks against your users browsing the web - you will want the URL/DNS reputation + Signature from AV & AB + you will want the exploit kit protections from IPS.
- if you want to protect your servers only in one profile and your users hosts in a different profile - its a little bit problematic.
- SMB signatures (IPS) and much others are relevant for Hosts & servers
- maybe you have a windows server...if you do - its practically a host that can be infected like your 'regular' ones - and then you will want AV for pre-infection protection and AB for post-infection protection.
Thanks,
Oren
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oren, you can use all the blades in each threat prevention profile, but limit the activated protections in each to only those applicable to protected scopes.
I.e. "Windows Servers" scope, for instance, unlikely need to be subjected to the protections for Linux, Cisco, Adobe, etc..
Similarly, Linux hosts do not need protections for IIS, SQL, etc., and only the MTAs and mail servers may need protections particular to smtp, pop3 and imap.
There are also some vendor-specific protections, (i.e. D-Link router vulnerabilities coverage), which you may not have in your environment at all.
By narrowing-down the profiles and the protections enabled in each to only those pertinent to the scope in rule, you are increasing effectiveness and reducing load on the gateways.
Regards,
Vladimir
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Vladimir - this is one of the usages and i totally agree that by working with Scope - it will be much much more effective.
i am looking for those exactly examples from our customers & partners in our community to improve our out of the box Threat Prevention profiles.
the common admin just want to protect his network and doesn't have the time or resources to use all our great features (protections TAGS as an example).
do you have any other examples for dividing the TP profiles for your network?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oren,
For the rough profiles definitions, we can use "Windows" and "Linux" specific profiles.
Under Windows profile category, Servers and Clients (with Servers, omitting the things like Adobe Flash and Reader, IE and other, application specific protections).
Under Linux, same breakdown with Server and Client (with server, omitting browser and application specific protections).
MS SQL as a separate category, since it is now could run on both, Windows and Linux.
Separate overall SQL category covering all relational databases.
Separate Mail category.
Separate Cisco category (too many vulnerabilities and easily defined scope).
Separate category for the overall protection from worms.
Separate category for CPU level exploits.
I would think that the above will cover the needs of most lazy admins:)
Would be nice to have a correlation tool capable of matching protections to the results of the vulnerability scans, such as Nessus, Qualys, Open VAS and Vulners, by comparing their csv output with protections available from CP and generating custom profiles that could be imported.
Having this capability will enable admins to immediately plug the discovered holes.
If this tool could do differential profile updates, that will be totally awesome.
Ability to merge rules with identical scope may also be handy, (i.e. rule added immediately after 0 day discovery as a separate line item that could later be integrated with one or more stable rules).
Just my 2 cents.
Cheers,
Vladimir
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Vladimir,
i think that its a great idea (import a list of relevant vulnerabilities to your network, compare to your profile and present an out-put for "which vulnerabilities should be enabled for better protection)
regard adding a new rule - we are updating the package of our blades all the time and if you will use our recommendation profile you will get it automatically - should we do something different? (basically we do not use rules for new protections - we update the TP profile in IPS case and update the cloud in AV/AB case)
Oren
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Presently, when you are adding new protections to the "Basic", "Recommended" or "Optimized" profiles and those are placed into staging, there are no indicators of whether those will change state to "Protect" or "Detect", so you are forced to select one of the actions manually.
But if you are relying on "Automatic Activation according to profile settings":
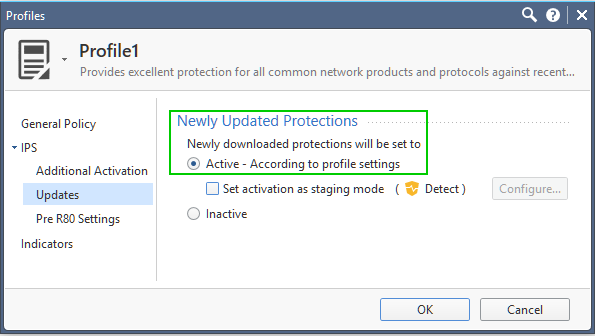
You are not sure which state the new protection will be placed in.
Having explicit notification about new protections and the state they are placed in automatically integrated in Threat Prevention, would be great: else we have to look at external references, find protections individually in IPS and either either enable action or verify it manually.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
if you are using staging mode, the idea is that you will decide what to do with a signature (based on your knowledge/need/limitations).
the interesting thing that you are proposing is to add a comment to the new signature we added regardless the profile status - 'what Check Point will do with it in case of optimize OR strict'.
back to the original question from Libin Thomas original post - if we could have out-of-the-box profiles for Threat Prevention, what they would be? what are the common profiles you are using in your networks and especially what are the changes you are doing in our pre-defined profiles?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Profile suggestions as per my previous post:
For the rough profiles definitions, we can use "Windows" and "Linux" specific profiles.
Under Windows profile category, Servers and Clients (with Servers, omitting the things like Adobe Flash and Reader, IE and other, application specific protections).
Under Linux, same breakdown with Server and Client (with server, omitting browser and application specific protections).
MS SQL as a separate category, since it is now could run on both, Windows and Linux.
Separate overall SQL category covering all relational databases.
Separate Mail category.
Separate Cisco category (too many vulnerabilities and easily defined scope).
Separate category for the overall protection from worms.
Separate category for CPU level exploits.
I typically use clones of the "Optimized" with protections irrelevant to scope disabled and those found by vulnerability scanners in scope, enabled.
Since I am consulting, each case is different.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


