- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Firewall Uptime, Reimagined
How AIOps Simplifies Operations and Prevents Outages
Introduction to Lakera:
Securing the AI Frontier!
Check Point Named Leader
2025 Gartner® Magic Quadrant™ for Hybrid Mesh Firewall
HTTPS Inspection
Help us to understand your needs better
CheckMates Go:
SharePoint CVEs and More!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Threat Prevention
- :
- IPS Core protection - I need help to better unders...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
IPS Core protection - I need help to better understand
Dear team,
I need your help to better understand IPS Core protections.
I found in documentation:
- IPS Core protections - These protections are included in the product and are assigned per gateway. They are part of the Access Control policy.
Why is that ?
If IPS Core protections are assigned globally (per gateway), why in Signature I have option to change/assigned different IPS profile to gateway ?
What will be if I assign here TP profile that is different than Optimized ?
Please see the attached picture.
BR,
Slobodan
SM
15 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Slobodan
Core protections are some general protections that aren't necessarily related to specific software or product vulnerabilities.
They are assigned globally, which means that when you click a signature you will enter the "Core protections" window shown in your screenshot and will change the profile for all core protections. This won't affect the ThreatCloud protections profile, which is assigned in the IPS rules tab.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
IPS Core Protections are the Inspection Settings.
Previously these were configured as part of IPS but they were separated in R80.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Actually, IPS Core Protections and Inspection Settings are 2 different things although both installed with Access Control. I wrote about it at https://community.checkpoint.com/thread/5159-where-did-all-my-ips-protections-go
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It would be less confusing if they were listed as part of Inspection Settings, IMO.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In my opinion this is very confusing. Is there any reason for this Core Protections to be assigned as a different profile in the Gateway?
Any change is being considered on future versions?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
By separating them from IPS protections, it's clear:
- These protections aren't actually IPS protections (they were just lumped with IPS protections in R70-R77.x)
- These protections do not require an IPS license to use (because they are actually enforced in the Firewall, not IPS)
- An Access Policy (Firewall) policy push is required to make changes to the configuration
As far as I know, there are no plans to change this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey Dameon,
I understand Core Protections and Inspection Settings are both enforced in the firewall and applied with Access Policy, but what differentiates them from Threat Cloud protections? From what I can tell, it appears that Inspection Settings deal with network packets that are not exhibiting 'normal' behavior but Core Protections have CVE reference numbers similar to Threat Cloud protections so that's where I'm a bit lost in understanding the difference.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As described in my IPS class, Core Protection/Activations are protections that are in a bit of a "no man's land" between Inspection Settings and IPS ThreatCloud protections. The only clarification I've been able to get about why Core Protections are handled like this is for "technical reasons". I suspect that one of the technical reasons was the ability to use Protected Servers definitions to more precisely control which defined servers would have these Core Activations applied to them. The Protected Servers mechanism is obsolete in R80.10+ due to the ability to apply different IPS profiles to the same gateway with separate Threat Prevention rules. Another reason might be that they are not typically just set to Prevent/Detect/Inactive and have various individual adjustments under a "See Details..." link; and also that exceptions must be added for each Core Protection individually. You can't add a single exception rule for a group of Core Activations or for "Any" of them.
Most of the Core Activations look like they belong under Inspection Settings to me since they are looking for various network protocol weaknesses.
--
"IPS Immersion Training" Self-paced Video Class
Now Available at http://www.maxpowerfirewalls.com
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you Tim, that is helpful
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Note that Geo Protection (now called "Geo Policy" in R80+ management) was also separated from the IPS blade and has its own profile assignments per gateway.
--
Second Edition of my "Max Power" Firewall Book
Now Available at http://www.maxpowerfirewalls.com
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
And in R80.20, you can do Geo rules in the regular Access Policy ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
> And in R80.20, you can do Geo rules in the regular Access Policy
How is this done in R80.20? Can't seem to find it...
Using GEO Location Objects in Firewall Policy (with Dynamic Objects), brilliant as it is, doesn't count. 🙂
--
Second Edition of my "Max Power" Firewall Book
Now Available at http://www.maxpowerfirewalls.com
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Click on the + in the Source/Destination field of a rule.
Select Import > Updatable Objects.
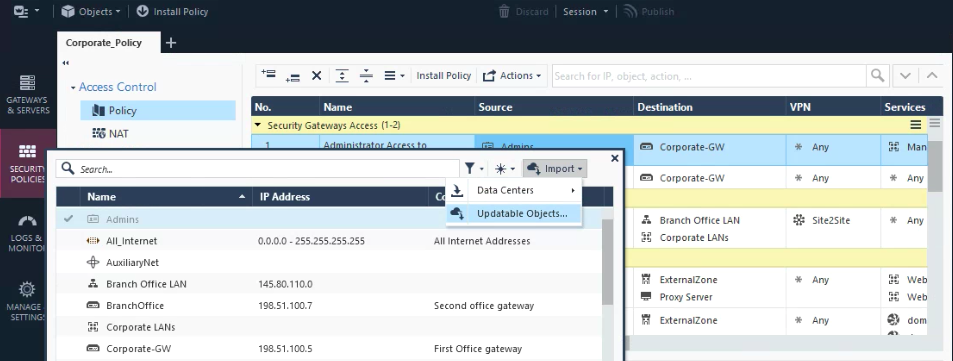
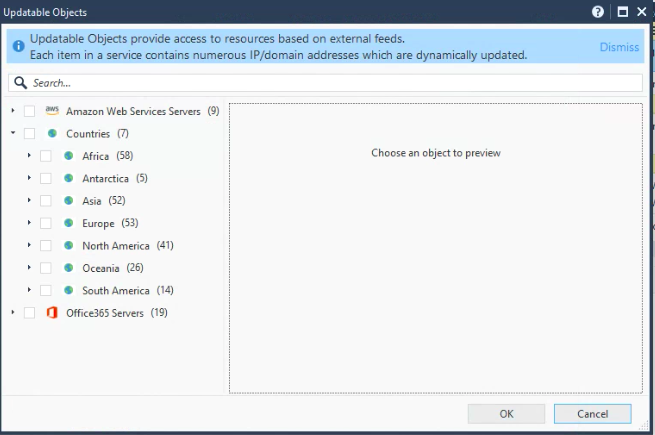
You can find updatable objects for:
- AWS Services
- Office 365
- Country Objects
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Because Geo Policy can now be implemented directly in the Network Policy Layer (among others) using updatable objects in R80.20 management, I assume these can be applied via policy to the Gaia Embedded appliances models 1100-1400 running R77.20.XX? There has been a longstanding limitation that these models do not directly support the separate Access Control Geo Policy/Protection feature (which I assume still applies in R80.20), but using these updatable objects as shown above appears to be a way to achieve the same effect on these models via the main Access Control policy layers. Is my assumption correct Dameon Welch-Abernathy?
--
Second Edition of my "Max Power" Firewall Book
Now Available at http://www.maxpowerfirewalls.com
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This feature requires R80.20 gateway support as the updating of these objects occurs on the gateway.
Which means the SMB appliances do not support this functionality currently.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Wed 22 Oct 2025 @ 11:00 AM (EDT)
Firewall Uptime, Reimagined: How AIOps Simplifies Operations and Prevents OutagesWed 22 Oct 2025 @ 11:00 AM (EDT)
Firewall Uptime, Reimagined: How AIOps Simplifies Operations and Prevents OutagesTue 28 Oct 2025 @ 11:00 AM (EDT)
Under the Hood: CloudGuard Network Security for Google Cloud Network Security Integration - OverviewAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


