IPS inspection requires additional CPU and memory resources to handle the incoming packets. If your CPU utilization is under heavy load IPS inspection will be disabled.
From CheckPoint:
Special IPS Bypass mechanism automatically disables all IPS protections (by placing them under exception), when it detects that the certain CPU utilization and memory utilization thresholds have been reached, and restores the IPS protections when the utilization decreases to a safe level.
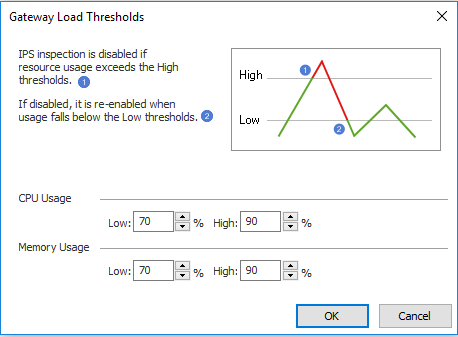
The IPS Bypass mechanism measures spikes on specific CPU core. Meaning, it may be enabled if one of the CPU cores / CoreXL FW Instances that handles IPS, has reached the configured trigger for Bypass. IPS Bypass trigger is measured as a CPU reading above the High threshold and 9 readings above Low threshold. The IPS Bypass feature is enabled if any CPU core is under heavy load (it uses the busiest CPU core - requires continued load for 10 seconds to enter bypass). It is not measured as average of all active CPU cores.
The bypass settings is under gateway properties:
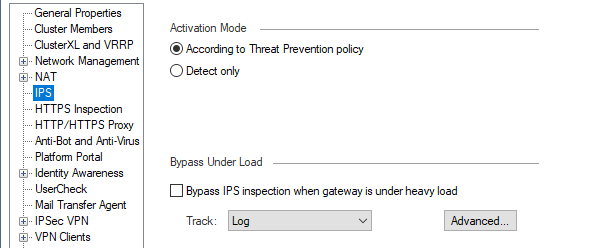
If you have it enabled there will be a checkmark under "Bypass IPS inspection..".
The thresholds can be seen under "Advanced" button.
To check your logs to see if IPS bypass did occur you can open Logs & Monitor and use this filter (choose last 7 days):
blade:IPS NOT(action:(prevent OR block)) OR "IPS Bypass Engaged" OR "IPS Bypass Disengaged"
This is very interesting specially if you have an appliance that have IPS enabled and not powerful enough to handle all the traffic. The above log filter will show when IPS bypass was engaged and then disengaged. By the timestamp you will see the timespan that you were not protected.
From CheckPoint:
Does this mean that when the Security Gateway is stressed absolutely, no IPS code is active?
Almost. Meaning, that all the IPS protections are under a global exception.
What would have happened on an appliance that did not have IPS bypass enabled but were under heavy load?
Is "IPS bypass enabled" a way for attackers to successfully run an attack by first making your firewall sweat and then run an attack knowing that your IPS protections will not be enforced during heavy load?




