- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Firewall Uptime, Reimagined
How AIOps Simplifies Operations and Prevents Outages
Introduction to Lakera:
Securing the AI Frontier!
Check Point Named Leader
2025 Gartner® Magic Quadrant™ for Hybrid Mesh Firewall
HTTPS Inspection
Help us to understand your needs better
CheckMates Go:
SharePoint CVEs and More!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Threat Prevention
- :
- How can I avoid "Host Port" scan?
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How can I avoid "Host Port" scan?
Hi,
We have a lot of "Host Port Scan" events in.
How can I avoid "Host Port Scan"?
In "Core Protecctions" we can only choice between "Accept" & "Inactive".
Could youo help me?
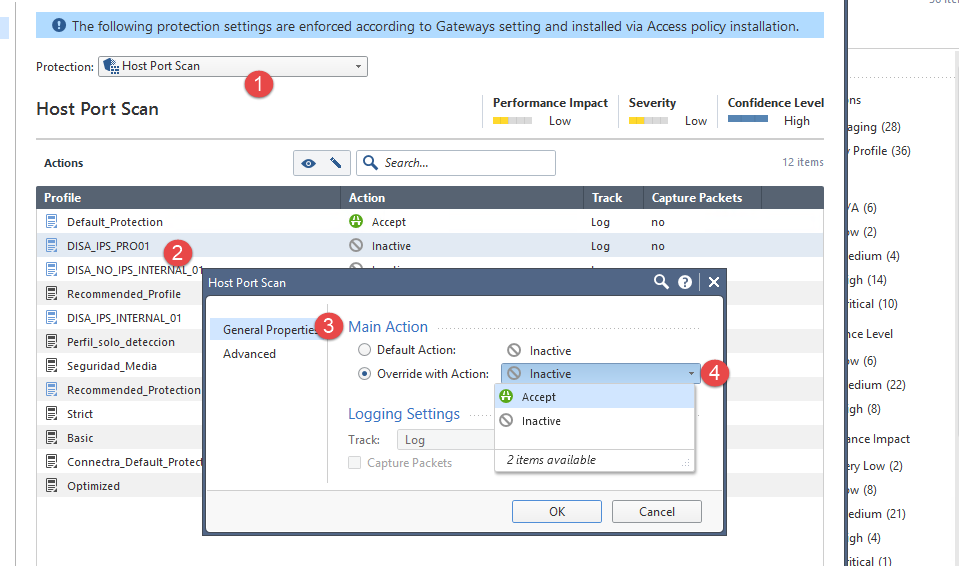
- Tags:
- host port scan
18 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Take a look at this SK How to configure Security Gateway to detect and prevent port scan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What do you mean by avoid? On the internet there's almost no way to avoid it, it happens all the time and everywhere.
Keep in mind that a portscan could be a first phase of an attack, looking at the cyber kill chain (reconnaissance). The amount of info can be annoying if it happens frequently but I would always keep this logged. Unless it's false positive (which I doubt).
I believe that the protection is enabled by default only for the strict profile.
HTH
/Martijn
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Use options 4 or 5, depending on the desired outcome.
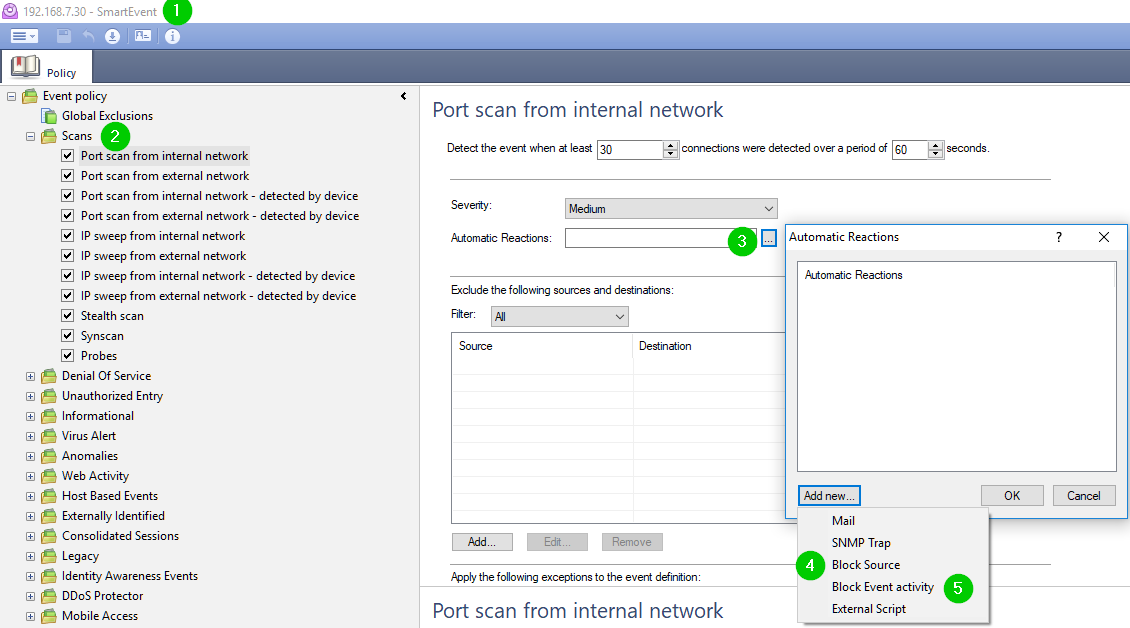
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Vladimir,
What mechanisms use this method? Is this method relevant for VSX infrastructure? For example, we try to use method which Enis Dunic described, but VSX doesn't support SAM mechanism.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
VSX R80.20 does support the "fwaccel dos" commands ![]()
'fwaccel dos' and 'fwaccel6 dos'
'fwaccel dos blacklist' and 'fwaccel6 dos blacklist'
'fwaccel dos rate' and 'fwaccel6 dos rate'
+
'fw sam_policy add' and 'fw6 sam_policy add'
fw sam_policy add' and 'fw6 sam_policy add'
Description
The 'fw sam_policy add' and 'fw6 sam_policy add' commands let you:
- Add one Suspicious Activity Monitoring (SAM) rule at a time.
- Add one Rate Limiting rule at a time.
Notes:
- You can run these commands interchangeably: '
fw sam_policy add' and 'fw samp add'. - Security Gateway stores the SAM Policy rules in the
$FWDIR/database/sam_policy.dbfile. - The SAM Policy management file is
$FWDIR/database/sam_policy.mng. - You can run these commands in Gaia Clish, or Expert mode.
- Configuration you make with these commands, survives reboot.
- VSX Gateway does not support Suspicious Activity Policy configured in SmartView Monitor. See sk79700.
- The SAM Policy rules consume some CPU resources on Security Gateway. We recommend to set an expiration that gives you time to investigate, but does not affect performance. The best practice is to keep only the SAM Policy rules that you need. If you confirm that an activity is risky, edit the Security Policy, educate users, or otherwise handle the risk.
- On VSX Gateway, first go to the context of an applicable Virtual System.
In Gaia Clish, run:
set virtual-system <VSID>In Expert mode, run:
vsenv <VSID> - In Cluster, you must configure the SecureXL in the same way on all of the cluster members.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hmm... I really am not sure what the underlying mechanism is.
Can someone from Check Point answer this question:
When scanning or DOS rules are configured in the SmartEvent with the action set to "Block Source" how is it executed in simple (i.e. single gateway or cluster) and in VSX environments?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- SAM Requests are stored in the kernel table sam_requests on the Security Gateway.
- IP Addresses that are blocked by SAM rules, are stored in the kernel table
sam_blocked_ipson the Security Gateway.
sam_alert:
This tool executes FW-1 SAM actions according to information received through Standard input.
This tool is to be used for executing FW-1 SAM actions with FW-1 User Defined alerts mechanism.
sam_alert -t 120 -I -src :
This will set an automatic SAM rule (for all Security Gateways managed by this Security Management Server / Domain Management Server) with the Source IP address of the host that caused a hit on the IPS protection "Host Port Scan" during 120 seconds.
HTH,
Ofir S
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If the SmartEvent actions are supposed to trigger SAM rules, is there enough intelligence in them to execute on VSX?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi! is it possible to set the automatic SAM rules only on some of the Security Gateways managed by this Security Management Server? I mean, in a situation where IPS is only enabled on the external GWs and detecting only incoming sweeps, and port scans arriving to the external interfaces from the internet, then there is no reason for setting the automatic SAM rules on the internal Gateways...
Best regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have just seen that you can specify on sam_alert command the gateways or group of gateways on which you want to apply the rules, I think it should be someting such us:
sam_alert -t 120 -f <nameGWs> -l src
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Vladimir,
One more question: where can I see IP addresses, which were blocked?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It should be in a SmartEvent view, not the SmartLog.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Vladimir,
Yes, I understand this, but as I understand I will see only some events. Where can I see a list of blocked IPs by "Port Scan" signature?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am actually not certain that you can see it in the list format. If the scan is blocked by creating a SAMP rule, and I do not see any other way it can be done without policy installation, it is added to the gateways kernel table.
You can see them using "fw tab -t sam_blocked_ips" in hex, but will have translate the output to readable yourself.
Alternatively, you can see the rules and the IPs blocked by SAMP here:

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Vladimir,
we are using R80.40 and i can't see that this Smart Event Policy will do anything.
This means that the behavior is the same whether I use the tool or not. Can you tell me if you can be preventing some scans with this ?
Can i troubleshoot this somehow ?
Many Thanks
thomas
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This Host port scan provides many features as I know this is Shows the open TCP ports, services, and version information, Includes operating system information and reverse DNS results, The original Nmap output is also included.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Berry, i know what scans are.
To make it sure... I can identify over IPS the Host Port Scans and the Sweep Scans, but i´m not able to prevent them. Neither with Smart Event or with "sam_alert -t 120 -l src" in Global Properties as Alert. Since I don't have much experience with checkpoint, I'm trying to figure out what I need to do differently to stop these scans. I was hoping that other people here also had this problem and could give me some help or ideas to make that is working. As I said: In smart event i have all scans with automatic replays configured. (Block source and block event activity - Source all Internet to any) AND i have configured what was recommended in the sk110873. But if i look " fw tab -t sam_blocked_ips" the table is still empty and the scan is to see in SMART LOG as Alert and IDS detect. Now i try to understand why checkpoint can identify the scan but what i have to do more to prevent.
If you have a idea , it would be create.
Thanks thomas
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
Has anyone been able to block port scan in VSX?
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Wed 22 Oct 2025 @ 11:00 AM (EDT)
Firewall Uptime, Reimagined: How AIOps Simplifies Operations and Prevents OutagesWed 22 Oct 2025 @ 11:00 AM (EDT)
Firewall Uptime, Reimagined: How AIOps Simplifies Operations and Prevents OutagesTue 28 Oct 2025 @ 11:00 AM (EDT)
Under the Hood: CloudGuard Network Security for Google Cloud Network Security Integration - OverviewAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


