- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Threat Prevention
- :
- DNS Reputation Exception
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
DNS Reputation Exception
I am trying to white-list a single domain for DNS Reputation prevents. Currently, it seems like the only option is to make exceptions for all of our DNS servers, effectively turning off DNS Reputation checks for DNS lookups in our company.
The domain is a employee awareness training like for phishing that is publically available, so it technically is a phishing site and should not necessary be re-categorized, but we'd like to whitelist it for our company during our phishing tests.
Has anyone ever had to do this before?
- Tags:
- dns
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
According to TAC case I've seen, it should be supported to use a Custom Application/Sites.
Here are the steps I found from one TAC case where the customer confirmed it works.
For Anti-Virus Configuration (R81.10, R81.20)
1. Verify Anti-Virus Blade: Ensure that the Anti-Virus blade is enabled.
2. Create Custom Application/Site:
* In SmartConsole, navigate to New > More > Custom Application/Site > Application/Site.
* Name the Application/Site and insert the domains into the URL list.
* Ensure the checkbox for "URLs are defined as Regular Expression" is unchecked.
1. Add Exception:
* Go to Security Policies > Threat Prevention > Exceptions.
* Click on Global Exceptions, then Add Exception > Above to create a new rule.
* Change the Action to Inactive.
* In the Protection/Site/File/Blade section, select your custom application.
* Ensure that the values in the following columns are set to Any:
* Protected Scope
* Source
* Destination
* Services
1. Install Policy: Install the Threat Prevention policy.
2. Clear Caches: Make sure to clear the DNS caches on the used DNS servers and the Malware Cache on the gateway. For instructions, refer to sk105179
13 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
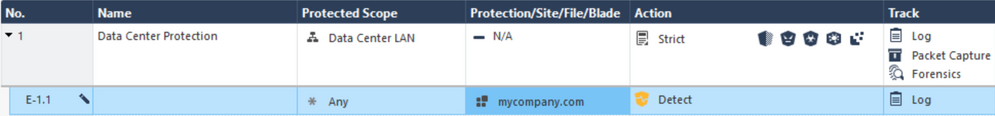
Seems like you could create a custom application definition for said domains and create an exception for it in your Threat Prevention policy.
Something like this:
@Vladimir this might also be a solution to the thread you raised about this as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@PhoneBoy perhaps this would work, if CHeck Point is the one blocking it.
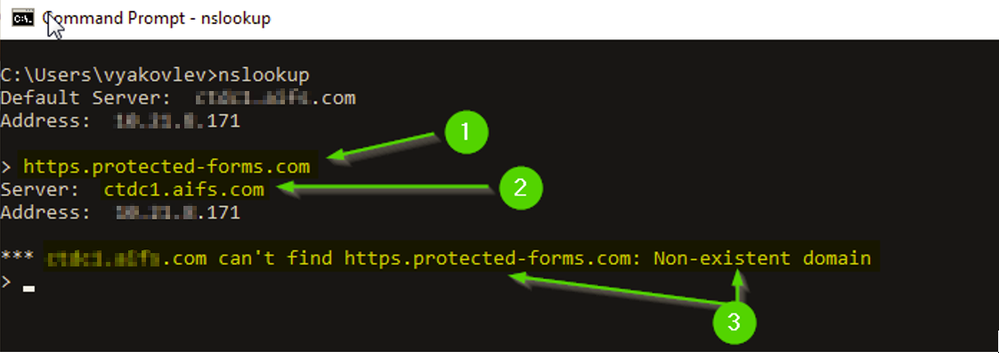
When I've added KnowBe4 domains to the categorization exceptions, the problems persisted, so in my case this was the issue:
When querying the https.protected-forms.com from inside the network, I was getting "can't find" in nslookup:
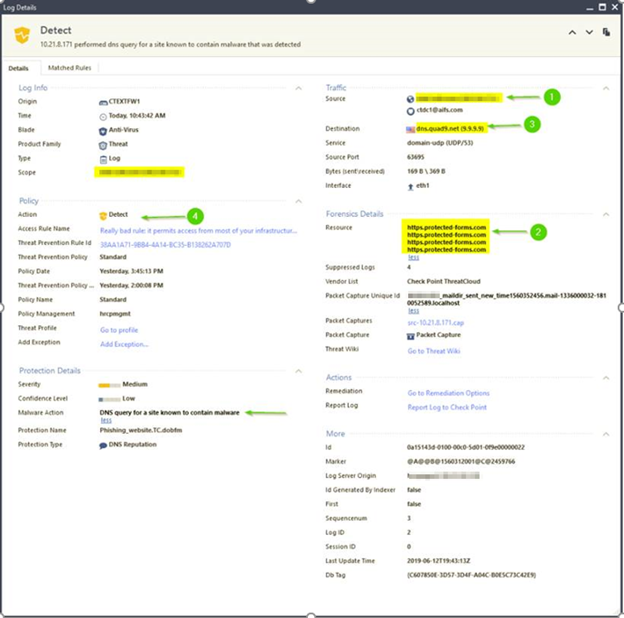
Looking in Check Point for this query, we see that it detects it as the query for malicious domain, but it allows it:
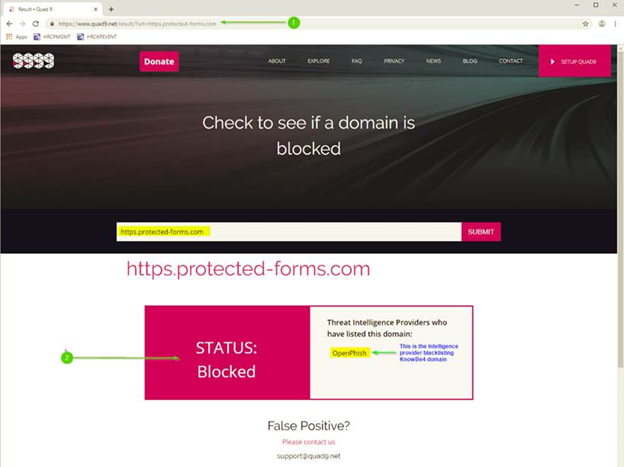
Finally, looking at the public DNS resolver that the Domain Controller forwarding the queries to, (IBM's Secure DNS Service Quad 9):
I have reached out to KnowBe4 and they are working on whitelisting this domain with threat intelligence providers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I know this is an old thread - but I've attempted to do this and haven't had any success.
I believe the issue is that Custom site/Applications only detect on ports 80/443/8080. Not DNS (port 53), which is what is being Prevented in the logs.
There doesn't seem to be a way to add additional Match-By criteria to custom site/applications in Check Point. I could add DNS to an existing App - but not a custom site/application.
Do you know if there's a way to get around this? I'll have to disable the AV protection on my Threat Prevention profile if I can't get exceptions working for these Microsoft Attack Simulation URLs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Custom Application/Site objects use the settings for Web Browsing.
Those can be changed here (though adding DNS might result in a performance impact):
If you know the domains used, you can create FQDN Domain objects and use those in the exception (with service Any).
This assumes your gateway and clients resolve DNS the same.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This doesn't seem to be working here (R81.20).
I have a list of domains that are already exempt from IPS and HTTPS inspection as they're used in phishing campaigns, but cannot find a way to make an exception on the DNS Reputation protection.
Any other tip?
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What specific things have you tried above any beyond the Custom Application/Site object?
In the "answer" for this thread, I had an FQDN Domain object (which I'm not 100% sure works).
If you're on R81.20, you might also try a Network Feed with the relevant domains included.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I did find an interesting tidbit in the R82 Threat Prevention guide that might help: "To add an exception to a DNS protection, you must go to the relevant log and add it from there."
This means right-click the log and select Add Exception.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If memory serves - this creates an exclusion for the detection name, not the domain. I was never able to get exclusions working for domains. The only way I could prevent the detection was by the detection name, which was untenable for Microsoft's attack simulation URLs. There are 130+ domains each with a unique detection name. This is one of those things where I feel it should be simple to exclude detections from the domain name considering it's a domain name resolution threat prevention mechanism. I hope CheckPoint implements a way to do this in the future.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It's also possible this note is specific to R82, since it is in the R82 documentation.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for your quick reply!
It looks like a network feed isn't a supported object in this scope.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
According to TAC case I've seen, it should be supported to use a Custom Application/Sites.
Here are the steps I found from one TAC case where the customer confirmed it works.
For Anti-Virus Configuration (R81.10, R81.20)
1. Verify Anti-Virus Blade: Ensure that the Anti-Virus blade is enabled.
2. Create Custom Application/Site:
* In SmartConsole, navigate to New > More > Custom Application/Site > Application/Site.
* Name the Application/Site and insert the domains into the URL list.
* Ensure the checkbox for "URLs are defined as Regular Expression" is unchecked.
1. Add Exception:
* Go to Security Policies > Threat Prevention > Exceptions.
* Click on Global Exceptions, then Add Exception > Above to create a new rule.
* Change the Action to Inactive.
* In the Protection/Site/File/Blade section, select your custom application.
* Ensure that the values in the following columns are set to Any:
* Protected Scope
* Source
* Destination
* Services
1. Install Policy: Install the Threat Prevention policy.
2. Clear Caches: Make sure to clear the DNS caches on the used DNS servers and the Malware Cache on the gateway. For instructions, refer to sk105179
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That worked!
Doing "the same" through the "custom policy" tab didn't however.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Glad it did and I've updated the "correct" answer accordingly. 🙂
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter