Hi @mschilt,
The SecureXL penalty box is a mechanism that performs an early drop of packets arriving from suspected sources. This mechanism is supported starting in R75.40VS.
Why not sam policy rules?
The SAM policy rules consume some CPU resources on Security Gateway. We recommend to set an expiration that gives you time to investigate, but does not affect performance. The best practice is to keep only the SAM policy rules that you need. If you confirm that an activity is risky, edit the Security Policy, educate users, or otherwise handle the risk. Or better use SecureXL penalty box from a performance point of view.
The purpose of this feature is to allow the Security Gateway to cope better under high load, possibly caused by a DoS/DDoS attack. These commands „fwaccel dos“ and „fwaccel6 dos“ control the Rate Limiting for DoS mitigation techniques in SecureXL on the local security gateway or cluster member.
In version R80.20, the penalty box feature is now supported in VSX mode and each virtual system can be independently configured for penalty box operation.
Attention!
In R80.20, all "sim erdos" commands are no longer supported. They have been replaced with equivalent commands which can be found under "fwaccel dos". Penalty box is configured separately for IPv4 and IPv6. IPv4 configuration is performed using the "fwaccel dos" command. IPv6 configuration is performed using the "fwaccel6 dos" command.
Control the IP blacklist in SecureXL with R80.20 and above. The blacklist blocks all traffic to and from the specified IP addresses. It is an easy way to block certain IP addresses quickly and eficiently on SecureXL level.
The blacklist drops occur in SecureXL, which is more efficient than an Access Control Policy or SAM rule to drop the packets. This can be very helpful e.g. with DoS attacks to block an IP on SecureXL level.
For example, the traffic from and to IP 1.2.3.4 should be blocked at SecureXL level.
On gateway set the IP 1.2.3.4 to Secure XL blacklist:
# fwaccel dos blacklist -a 1.2.3.4
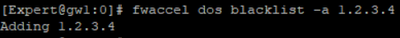
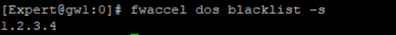
On gateway displays all IP's on the SecureXL blacklist:
# fwaccel dos blacklist -s
On gateway delete the IP 1.2.3.4 from Secure XL blacklist:
# fwaccel dos blacklist -d 1.2.3.4

➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips





