I'm wondering the same thing. I've stumbled onto this issue myself on a Gaia R81.20 installation. Several logs show:
Id: 9f3b54d2-28a9-b2e7-6438-d9230001000b
Marker: @A@@B@1681423200@C@2998816
Log Server Origin: *removed for privacy reasons*
Time: 2023-04-14T04:40:03Z
Interface Direction: outbound
Interface Name: eth5
Id Generated By Indexer: false
First: false
Sequencenum: 39
Threat Prevention Policy: *removed for privacy reasons*
Threat Prevention Policy Date:2023-04-13T17:29:14Z
Service ID: domain-udp
Source: *removed for privacy reasons*
Source Port: 55277
Destination: 2001:500:40::1
Destination Port: 53
IP Protocol: 17
Session Identification Number:0x6438d923,0x1000b,0xd2543b9f,0xe7b2a928
Protection Name: Swift.TC.c754KqbG
Malware Family: Swift
Description: Connection was allowed because background classification mode was set. See sk74120 for more information.
Confidence Level: High
Severity: High
Malware Action: DNS server resolving a site known to contain malware for a client behind it
Protection Type: DNS Reputation
Threat Prevention Rule ID: 170CAD95-2A46-46C7-B72A-C2ABE51782D8
Protection ID: 00283EC74
Vendor List: Check Point ThreatCloud
Action Details: bypass
Log ID: 2
Scope: *removed for privacy reasons*
Suppressed Logs: 1
Last Hit Time: 2023-04-14T04:41:04Z
Action: Detect
Type: Log
Policy Name: *removed for privacy reasons*
Policy Management: *removed for privacy reasons*
Db Tag: {DB09EBF5-3C1A-4046-8ACA-0BA7610D30E3}
Policy Date: 2023-04-13T17:29:09Z
Blade: Anti-Virus
Origin: *removed for privacy reasons*
Service: UDP/53
Product Family: Threat
Sent Bytes: 0
Received Bytes: 390
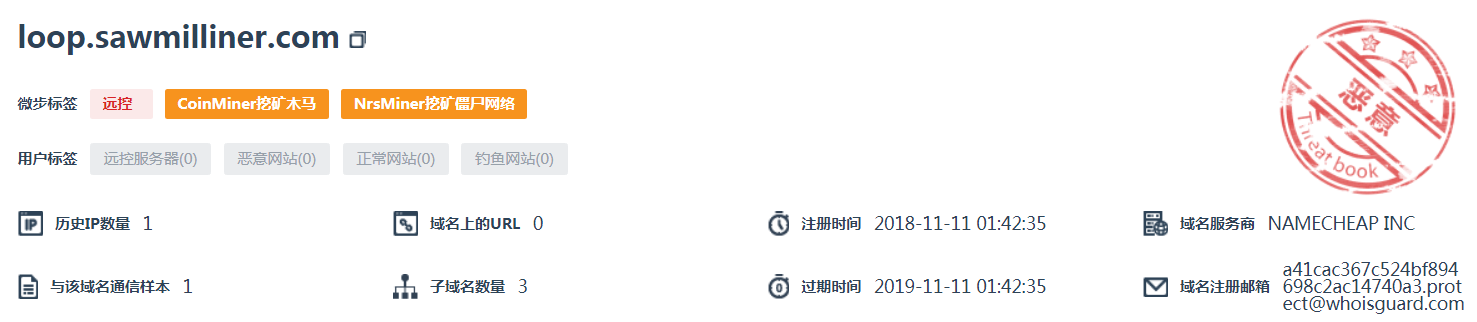
Resource: **bleep**90.duckdns.org
Interface: eth5
Description: *removed for privacy reasons* performed dns server resolving a site known to contain malware for a client behind it that was detected
Threat Profile: *removed for privacy reasons*
Bytes (sent\received): 0 B \ 390 B
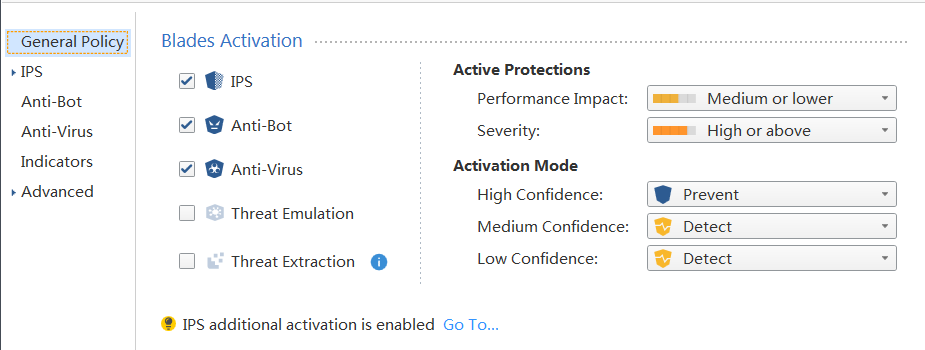
I knew about the Threat Prevention Engine settings, so I tried changing Anti Virus and Anti Bot from Background to Hold. Didn't change anything. I get similar logs from both the Anti Virus and Anti Bot blade:
Id: c1b5f4f7-67b8-28c9-6438-cb0600010014
Marker: @A@@B@1681423200@C@2545885
Log Server Origin: *removed for privacy reasons*
Time: 2023-04-14T03:39:50Z
Interface Direction: outbound
Interface Name: eth5
Id Generated By Indexer: false
First: false
Sequencenum: 11
Threat Prevention Policy: *removed for privacy reasons*
Threat Prevention Policy Date:2023-04-13T17:29:12Z
Service ID: domain-udp
Source: *removed for privacy reasons*
Source Port: 53299
Destination: 194.62.182.53
Destination Port: 53
IP Protocol: 17
Session Identification Number:0x6438cb06,0x10014,0xf7f4b5c1,0xc928b867
Protection Name: nanocore.TC.cai
Malware Family: Nanocore
Description: Connection was allowed because background classification mode was set. See sk74120 for more information.
Confidence Level: High
Severity: High
Malware Action: DNS server resolving a C&C site for a client behind it
Protection Type: DNS Reputation
Threat Prevention Rule ID: 170CAD95-2A46-46C7-B72A-C2ABE51782D8
Protection ID: 0019B95C1
Vendor List: Check Point ThreatCloud
Action Details: bypass
Log ID: 2
Scope: *removed for privacy reasons*
Suppressed Logs: 1
Last Hit Time: 2023-04-14T03:40:51Z
Action: Detect
Type: Log
Policy Name: *removed for privacy reasons*
Policy Management: *removed for privacy reasons*
Db Tag: {DB09EBF5-3C1A-4046-8ACA-0BA7610D30E3}
Policy Date: 2023-04-13T17:29:09Z
Blade: Anti-Bot
Origin: *removed for privacy reasons*
Service: UDP/53
Product Family: Threat
Sent Bytes: 0
Received Bytes: 121
Resource: cnam.myvnc.com
Interface: eth5
Description: *removed for privacy reasons* performed dns server resolving a c&c site for a client behind it that was detected
Threat Profile: *removed for privacy reasons*
Bytes (sent\received): 0 B \ 121 B
Checking https://support.checkpoint.com/results/sk/sk74120, the SK does mention:
Note: Starting from R75.47 and R76, Anti-Bot Resource Classification mode for DNS is performed in the "background" on the Security Gateway. To learn more, see sk92224 - Resource Categorization for Anti-Bot / Anti-Virus DNS Settings optimization.
There is no mention of the possible impact of doing the change mentioned in https://support.checkpoint.com/results/sk/sk92224.
I suspect most of the logs I see are somewhat misleading as our R81.20 gateways use Network Feeds, some including domains for use as a blacklist in the Network Policy. Judging by traffic logs and the timestamp, it seems like the gateway is resolving the domains from the blacklist. As a result of the network feed consisting of well-known bad domains, the gateway is trying to resolve the domains querying our local Windows DNS server. As soon as the Windows DNS server resolves the domain, the Anti Virus and Anti Bot start kicking in (seems a bit random whether it is the Anti Virus or Anti Bot blade) and drops it as "DNS Reputation". And some of these queries end up in detect because "Connection was allowed because background classification mode was set.".
It doesn't look good to have Smart Event telling there are a bunch of attacks not getting prevented, so I'm tempted to make this change to look better. But at the same time, I'm sceptical about the impact this change might have as I feel these logs aren't all that important as it's just the gateways themselves triggering the behaviour when resolving the Network Feed objects containing bad domains.
Reason for me to be sceptical about the change is how changing Anti Virus and Anti Bot in Smart Console does not affect DNS. Surely there is a reason why it behaves this way and you have to start fiddling with manual edits of local files for it to start holding DNS traffic.
Certifications: CCSA, CCSE, CCSM, CCSM ELITE, CCTA, CCTE, CCVS, CCME