- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Access Control and Threat Prevention Best Practices
5 November @ 5pm CET / 11am ET
Ask Check Point Threat Intelligence Anything!
October 28th, 9am ET / 3pm CET
Check Point Named Leader
2025 Gartner® Magic Quadrant™ for Hybrid Mesh Firewall
HTTPS Inspection
Help us to understand your needs better
CheckMates Go:
Spark Management Portal and More!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Threat Intelligence Reports
- :
- sLoad Delivering Ramnit
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
sLoad Delivering Ramnit
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
2019-01-28
01:23 AM
Early November, we identified a new variant of sLoad downloader delivering Ramnit malware. sLoad is a sophisticated PowerShell downloader, usually in the form of an LNK file. It is known to perform different fingerprinting actions, such as using geofencing, to allowing the attackers to choose targets of interest for the payloads of their choice.
The campaign we analyzed contains a few interesting technical features that were not a part of the sLoad downloader before. The main and most interesting feature is embedding a part of the PowerShell code in the ZIP parent file itself. That feature makes it impossible to run the malware separately from the ZIP parent, as most sandbox tools do today.
Technical Analysis
Stage 1 - ZIP File
The first stage of the attack consists of a ZIP file with 3 files archived inside of it- 2 PNG files and 1 LNK file.The LNK is a sLoad downloader, which executes a PowerShell script:
In the picture below, we can see the ZIP's end-of-file. Right after the end-of-file, we see the PowerShell sthe script is using.
.png)
In this code, we see that the PowerShell is using bitsadmin program to access the URL artisbond[.]org/arti/bond.
Stage 2 - Downloaded Powershell Script Execution
From this URL, another PowerShell code is downloaded, this time checking for the existence of monitoring tools such as windbg, tcpdump etc. and kills those processes.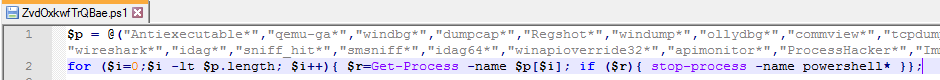 After stopping the monitoring processes, it creates a directory in AppData with the name of the computer's UUID. The PowerShell script then drops the payload files- two ini files, a VBS file, and a PS1, which were hidden obfuscated inside of it. Before finishing its run, the Powershell script disables scheduled tasks related to OneDrive, and creates it's own scheduled task, named "AppRunLog".
After stopping the monitoring processes, it creates a directory in AppData with the name of the computer's UUID. The PowerShell script then drops the payload files- two ini files, a VBS file, and a PS1, which were hidden obfuscated inside of it. Before finishing its run, the Powershell script disables scheduled tasks related to OneDrive, and creates it's own scheduled task, named "AppRunLog".Stage 3 - Scheduled Task Execution
In the third stage, we have a "config.ini" and "web.ini" files, which are obfuscated payloads, in the created folder and the VBS and PS1 files in the folder. The scheduled task previously created, will execute the VBS script, which will execute the PowerShell script, which eventually de-obfuscate the obfuscated payloads and execute them.
The final payload seems to be Ramnit malware, which correlates with other recent distributions of sLoad.
Campaign Analysis
The initial file analyzed in this campaign was a ZIP file containing 2 PNG files and 1 LNK file.
We began analyzing the files, domains, and IPs related to this sample and discovered a wide infrastructure, containing a variety of campaigns with similar attributes to our campaign, for the last several months.
we used VT graph feature to map the connections between the different campaigns
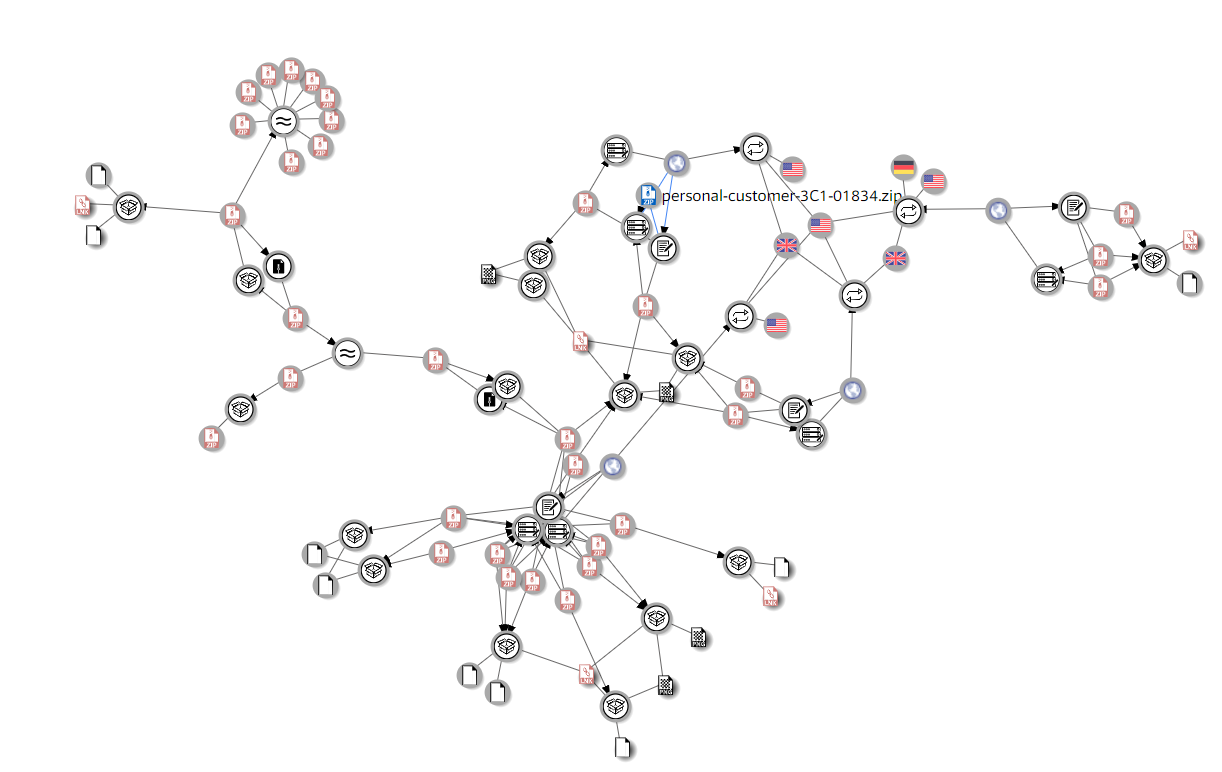
In the graph above, we can identify 2 IP addresses that related to all samples:
143.95.73[.]224
185.17.27[.]108
Looking at the indicators of the attack, it seems to be related to a campaign covered by Proofpoint
The Proofpoint analysis focused on an LNK sample is parsing a PowerShell script that starts from the LNK end-of-file.
In our sample, we saw that the PowerShell script is parsed from the ZIP end-of-file, Which is the main difference between these campaigns.
IOCs
MD5s
ee282ae8feb0e30b3e64efa2ab12aece
1b5fe6f9efe14081f7000f78f3eaffd2
b5d9b28ac2e053a7169a899c485eec4d
60bcdfdb2da81dbd783f383271c4d8ed
212b0c83761fc28d863900ab49d41e0a
b3c0f532cf9d23b02d6057fc7a0a09c8
20e520e4afeac5a56a71e02289c81486
5fb6297d7b017a4fdd3eca1d39a7549d
50b30bd7979a7d5009d4442e48c7f957
c2d546936ad8711101ab937c4a3d2a4c
e5d39b40f2bc845917112104d3e3d9c4
d636cfe8e154d678d8ffc51e34f97708
76e725669c2c24362346e79ae12f01de
e862a654e9370c27e46652778ffb7f86
83d481157b1c25d1d6f67f6eeb2b9d1a
2a2b9d5ed58339253fa220712c9b4083
f4bb659c4543f88f47f83b5175a77a2f
39f7e66e414579eeb6642f48c68f2cd8
6da1aac8fc0a83f3dce952133e3bf532
350a1d6bdcd04d55d6d848d6150d6770
a014e18805338489f82420b7a4bbb96b
eccd6dd8c769eb17e0dc26038624453d
0ad8675f412d8755f7f060b753d492a6
25c992379bcea69473d2491f2917f1cd
8a033c4d4630f5434421e0c2df46158c
08e68f4dd0333f2e56f4a8c120e82dce
c9d87dcec61313fa72d3ea4f7c16ad8c
9278205a57f70a69d09dfef6397ad027
a6c8877c7257264dab3f7c1c5f6f9198
b82d15e9ad0f17c7eb27770d4cb2d547
7513a2e759da21f8063381afbac0e88f
4f1ead14ab1d6872abacc984db9a3da9
c4db2b5d79649686c39bdab040d579fc
66c8e57620cea69d84cd8324245c4ddb
5a15eeef6fdb63a98318c6908d373d1e
89c747063d306c809fc26a078d1d5577
719719069fc140024ae0eb958f1594db
c0bfabac5ddfcea4d8635a376d07cb6f
0bea0db9104757564a5ff2e7bb4cdd00
7c0d442d409f8f91780d20bb351ea001
dd6bec9a37971c20f4b4c8f80f2cd4b2
9286ab0e3ed97476a4e331148abbc5b1
84bcf9ecb666939ee7e93b90028ac10d
eee282d22b8046390e02e019a603bc3b
dbdf6d9c41ab2e80cda9c62ffdd30bd4
Domains
rayhickeyjr[.]com
artisbond[.]org
halfaracoon[.]com
zerotogeek[.]com
IPs
185[.]17[.]27[.]108
143[.]95[.]73[.]224
143[.]95[.]39[.]77
185[.]17[.]27[.]102
143[.]95[.]37[.]78
77[.]6[.]80[.]137
184[.]168[.]221[.]34
About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


