- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
The Great Exposure Reset
24 February 2026 @ 5pm CET / 11am EST
AI Security Masters E4:
Introducing Cyata - Securing the Agenic AI Era
AI Security Masters E3:
AI-Generated Malware
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Hybrid Mesh
- :
- SmartMove
- :
- Re: SmartMove disable layers in policy?
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
SmartMove disable layers in policy?
I am currently migrating Juniper ISG to Checkpoint gateway using SmartMove. This tool is great, but I have one problem: we need to use a flat policy structure, not a layer, which is generated from SmartMove.
Is it possible to somehow disable layers when policy will be under domain or tweak a bash script to create a flat structure?
thanks,
- Tags:
- smartmove
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
SmartMove tool uses layered policy approach, by design, for every vendor.
If you need Juniper SRX policy to be migrated as a flat policy, define it as global in Juniper SRX. There is no other way.
Robert.
14 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
did you followed precisely sk115416 with it?
Jerry
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, I followed sk115416 and migrated policy is layered.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm not 100% what happened but you must have placed your configuration into the:
Get the Juniper configuration file from the gateway. See vendor documentation for "show configuration" commands.
- From Junos: get the configuration file in XML format
- From ScreenOS: get the configuration file in CLI format.
should you've done CLI format there is literally no way it may go onto the Layered Network policy. There must have been something wrong on the way Denis.
is there any chance you can move your layered-network policy to the flat one? on Dashboard you should be able to "migrate" your Layered one onto the "Policies" where you can see only "Access Control" and "Threat Prevention" blocks.
please paste here how your Layered Policy looks like (mark up your specific datails) - there must be a way of making this right even though you've migrated the ScreenOS via SmartMove.
did you managed to import XLM file with "Convert NAT configuration" or without ?
I've done JunOS in the past from my beloved SRX's and it all went perfectly fine, ISG/SSH are quite vintage once hence my question is "what went wrong" ? ![]()
Jerry
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is how the policy looks like.
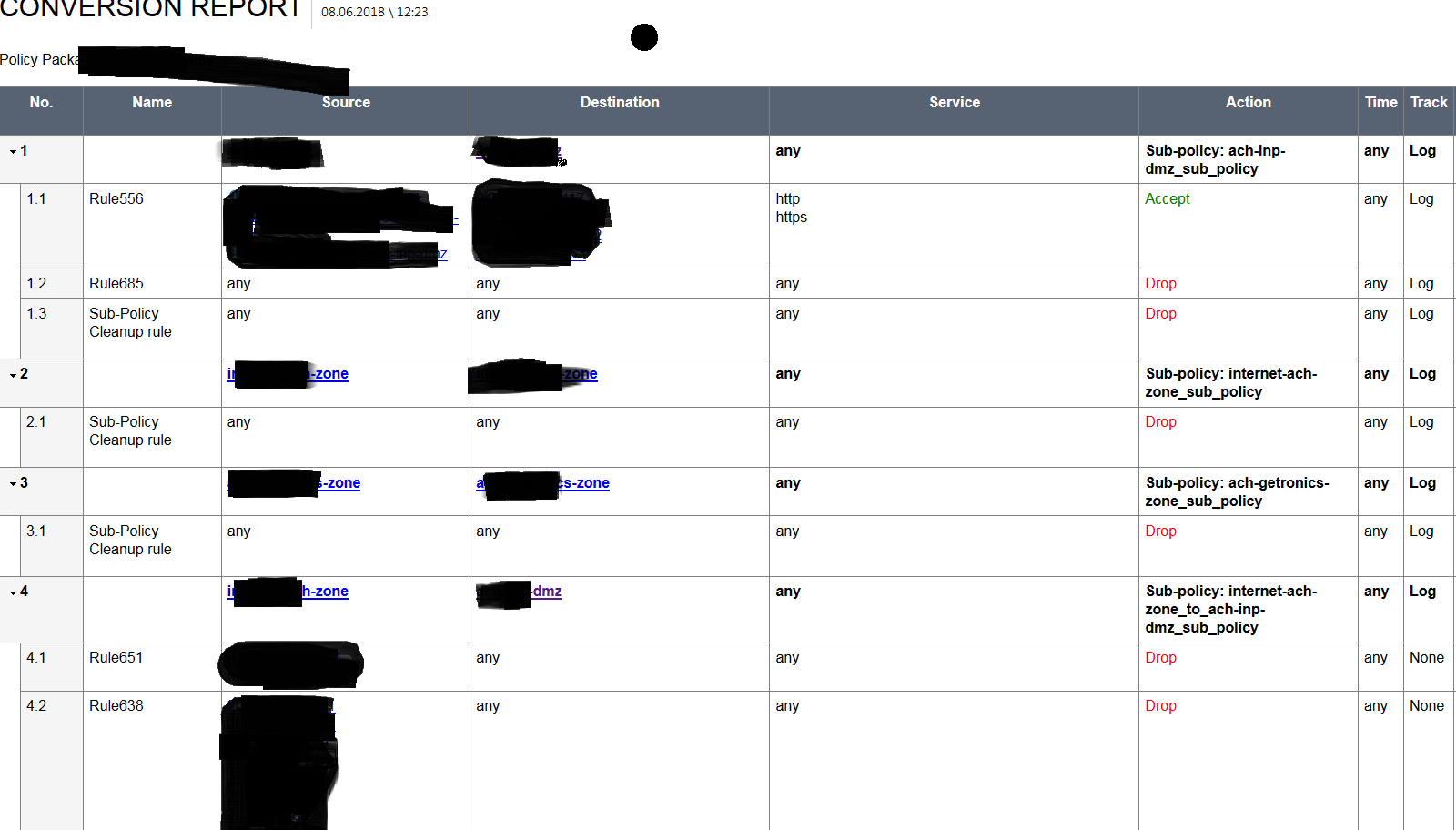
etc, I have about 400 rules divided into layers.
This is part of the bash script:
mgmt_cli SmartMove_Create_Policy -s id.txt > /dev/null 2>&1
echo 'create package [--_policy]'
cmd='mgmt_cli add package name "--_policy" threat-prevention "false" ignore-warnings true -s id.txt --user-agent mgmt_cli_smartmove'
run_command
echo 'Layers: Creating 9 sub-policies'
echo 'create layer [---dmz_sub_policy]'
cmd='mgmt_cli add access-layer name "---dmz_sub_policy" add-default-rule "false" ignore-warnings true -s id.txt --user-agent mgmt_cli_smartmove'
run_command
echo 'Add rules to layer ---dmz_sub_policy'
cmd='mgmt_cli add access-rule layer "---dmz_sub_policy" comments "Intra Zone Blocking Enabled" action "drop" track-settings.type "Log" position "top" name "Sub-Policy Cleanup rule" ignore-warnings true -s id.txt --user-agent mgmt_cli_smartmove'
run_command
echo -n $'\rrule 1/3 '
cmd='mgmt_cli add access-rule layer "---dmz_sub_policy" source "any" destination "any" service "any" action "drop" track-settings.type "Log" position "top" name "Rule685" ignore-warnings true -s id.txt --user-agent mgmt_cli_smartmove'
run_command
echo -n $'\rrule 2/3 '
cmd='mgmt_cli add access-rule layer "---dmz_sub_policy" source.0 "---dmz" source.1 "EDS-RUN-_---dmz" source.2 "---dmz" destination.0 "--" destination.1 "--" service.0 "http" service.1 "https" action "accept" track-settings.type "Log" position "top" name "Rule556" ignore-warnings true -s id.txt --user-agent mgmt_cli_smartmove'
run_command
You can clearly see that it creates layered policy.
I did a get config output from Juniper ISG, so I have a CLI view.
I did use following settings, I have no NAT configuration in ISG config:
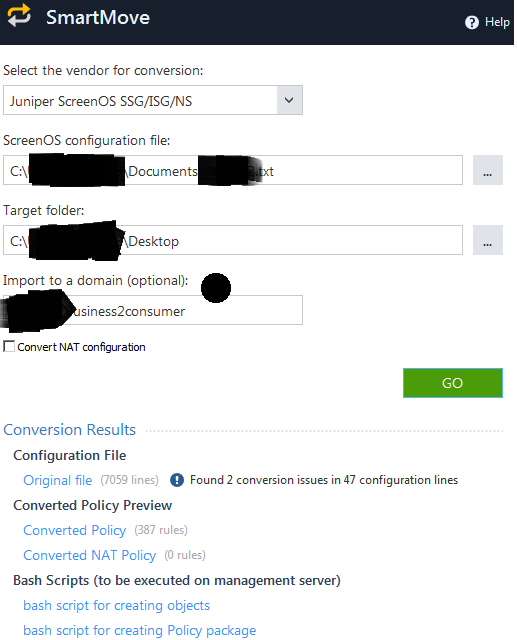
I have a workaround: I can migrate ISG policy to Juniper SRX format, then I can use xml file to migrate to Checkpoint, but please tell me if there is anything I can tweak here.
thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes. Now I can tell you that this is abnormal to create from TXT file (CLI option) multi-layered import.
If I were you I would have ask Tomer Sole or Dameon Welch Abernathy as in my opinion (and I've done only XML version from JunOS myself) there is something wrong with the SmartMove that it imports TXT file onto the GAIA as "Layered" one.
I see now that you're correct. This is something what R&D should be made aware of as I'm not gonna be helpful here I'm afraid. Sorry Denis. Let's see what our GURU's says ![]()
Cheers
Jerry
Jerry
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If the source vendor uses a zone-based policy, we convert it to zone-based inline layers. So that's how a single text file is converted to a tree of policies - because this reduces the need to write "source zone" and "destination zone" in each one of the rules.
Does this make sense?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
totally. that makes perfect sense Tomer, but while every zone-based 3rd party vendors these days produces a config. file like Denis's Juniper ISG/SSH mentioned, would that mean that it is going to be like that every time and creates multi-layered CP set?
does it mean it is an expected behavior from SmartMove or it depends? you know what I mean, would that be for every configuration which is zone-based these days?
I'm asking as when I made my SRX also zone-based migration it was flat-layer via SmartMove and I definitely did not have multi-layered outcome in R80.10. I've done this nearly a year ago in my lab and it went smooth as if it was native upgrade_export/import ![]()
Jerry
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
SmartMove tool uses layered policy approach, by design, for every vendor.
If you need Juniper SRX policy to be migrated as a flat policy, define it as global in Juniper SRX. There is no other way.
Robert.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
that is exactly what I meant Robert ![]() my JunOS config. display-set was flat (global) hence my conversion to GAIA was smooth and none-layered. Seems Denis's isn't that simple plus it isn't JunOS but ScreenOS based - that's what this topic is all about. JunOS - we all know it is simply easier to handle - ScreenOS - not so much.
my JunOS config. display-set was flat (global) hence my conversion to GAIA was smooth and none-layered. Seems Denis's isn't that simple plus it isn't JunOS but ScreenOS based - that's what this topic is all about. JunOS - we all know it is simply easier to handle - ScreenOS - not so much.
Jerry
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks, this is something I looked for.
I will define my ISG policy as global.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is there also a workaround for a Cisco ASA config conversion to be flat policy? I did my Cisco to Checkpoint conversion successfully, but we don't want to keep the Layered Policy. Is there any way i can get a flat Checkpoint Policy?
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The same goes for Cisco ASA - make the access groups global ("global") instead of inbound ("in").
In addition, disable the inter/intra security traffic ("same-security-traffic") to block creation of trafic between zones, in case you do not want to create rules for traffic between them.
Robert.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
btw. what is the verions of your pre-import ScreenOS?
Have you seen the limitations to ScreenOS version 6.3 (R19B/R22) and above ?
Just thoguht it is wise to mention as this seem important prereqs.
Jerry
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It's R21. But I see no difference in the config which I need to migrate between R21 and R22.
Upcoming Events
Mon 23 Feb 2026 @ 11:00 AM (EST)
Latest updates on Quantum Spark including R82 features and Spark Management zero touch - AMERTue 24 Feb 2026 @ 10:00 AM (CET)
Latest updates on Quantum Spark including R82 features and Spark Management zero touch - EMEATue 24 Feb 2026 @ 11:00 AM (EST)
Under The Hood: CloudGuard Network Security for Azure Virtual WANMon 23 Feb 2026 @ 11:00 AM (EST)
Latest updates on Quantum Spark including R82 features and Spark Management zero touch - AMERTue 24 Feb 2026 @ 10:00 AM (CET)
Latest updates on Quantum Spark including R82 features and Spark Management zero touch - EMEATue 24 Feb 2026 @ 11:00 AM (EST)
Under The Hood: CloudGuard Network Security for Azure Virtual WANThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Introducing Cyata, Securing the Agentic AI EraFri 06 Mar 2026 @ 08:00 AM (COT)
Check Point R82 Hands‑On Bootcamp – Comunidad DOJO PanamáAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


