- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Smart-1 Cloud
- :
- Re: Creating a Cluster managed by Smart-Cloud
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Creating a Cluster managed by Smart-1 Cloud
Hi All,
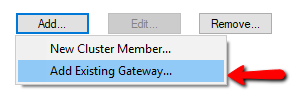
If you are using Smart-Cloud to manage your Security Gateways and are looking to deploy a Cluster - You will need to do this using the ADD EXISTING GATEWAY option.
When you provision/add a new gateway from Smart Cloud, this will create the Gateway Object within Smart Console. Now if these gateways need to be part of a cluster, then you will have to add them using the ADD EXISTING GATEWAY option.
- Login into Smart Console (connecting to your management Instance in Smart Cloud).
- Create a New Cluster
- Give it a Name and IP Address
- Then under Cluster members --> Add --> SELECT Add existing Gateway.
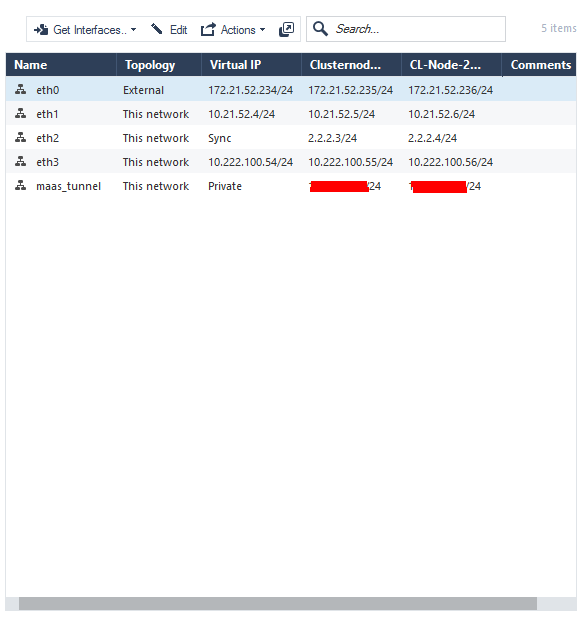
Additionally the topology will now have the maas_tunnel interface also detected as part of the GET INTERFACES with TOPOLOGY.
I had my interface topology configured as below to work successfully.
Hope this is helpful.
15 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for sharing this. This is indeed the way to do it today in Smart-1 Cloud.
Since Cluster is a very common deployment, I also wanted to share that we are working on a simpler way to do this, which will be similar to the way you connect a regular gateway.
This will be rolled out automatically for Smart-1 Cloud users.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
When will this new deployment be ready?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Abbas,
Thanks for sharing this, as I'm trying to setup my first cluster in Smart-1 Cloud.
I successfully connected the gateways and establish communication with Management Server with SIC Trust, and so far I have the maas_tunnel, inside, outside and sync interfaces for each GW. However when I try to setup a cluster following the wizard / or even classic mode as you suggest above, can you please advise what IP do we configure as a Cluster VIP IPv4 address ?
I also read the documentation, but all it says is not to use an IP from 100.64.x.x network. Still I don't figure out what IP I should use as a Cluster VIP.
Our deployment is in R80.40
Thanks for your help in advance,
Konstantinos
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Konstantinos,
The gateways get the automatic IP when establishing the maas tunnel, for the Cluster itself, you should provide your own virtual IP. Similar when connecting a cluster to an on-prem management, nothing special here for Smart-1 Cloud.
If you still have some challenges, please let me (@Anat_Eytan-Davi) or @Amiad_Stern know and we will be happy to assist,
BR,
Anat.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Anat,
Thanks for your explanation. I understood that once you connect the GWs to the smart-1 Cloud, those get their 100.64.x.x/32 IPs ( MaaS tunnel IP). For the cluster VIP, I figured I could use the VIP of the inside interface ( cluster ).
Once the cluster was setup, in the Network Topology, the Inside / Outside / Sync interfaces, would be appear as it should. Nevertheless, there would be 2 entries, each for a different GW, where there would be the maas tunnel /32 IP.
I’m not sure if this is the expected outcome, to have in the Cluster Network Topology, different maas interface / per GW
Unfortunately, I cannot provide you with any screenshots, as finally we deployed the Management Server on premise ( VM-Open Server).
However, if there will be a case where I’ll need to setup a cluster on Smart-1 Cloud, I’ll return back to the same post.
Anyhow, thanks for your contribution and support on this case.
Kind Regards,
Konstantinos
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nice info!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I need to move an on prem cluster to the cloud, I imported the management with success but now it's not clear what to do with the gateways: I added my two gateways and they created their new maas_tunnel interfaces 100.64.x.x/32, but how can I define the vip for them?
Or is it not necessary?
The whole process is not explained anywhere, do I have to add rules for the 100.64.x.x IPs?
Can you helping me in the steps to migrate my on premise cluster to be managed from the SMS Cloud?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
You can create a new Cluster object, or use an existing Cluster object.
The Cluster Virtual IP is not automatically given by the system, and you need to assign one.
Make sure not to give an IP address from this subnet: 100.64.x.x
Next phase is to navigate to Cluster Members > click Add > click Add Existing Gateway > select the Security Gateway object.
You need to allow the communication between the Security Gateway and the service:
-
HTTPS (TCP 443) to your domain at Smart-1 Cloud:
<Service-Identifier>.maas.checkpoint.com -
For Smart-1 Cloud deployments in Europe:
cloudinfra-gw.portal.checkpoint.com -
For Smart-1 Cloud deployments in the United States:
cloudinfra-gw-us.portal.checkpoint.com
I do recommend to check the admin guide, especially the section for advanced configuration: Smart-1 Cloud Advanced Configuration (checkpoint.com)
Please feel free to reach out if the process is still unclear or for any additional question to me (anate@checkpoint.com) or to maas@checkpoint.com
Anat.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm seeing some differences in the information here when setting up a new Azure R81 IaaS cluster connected to MaaS.
The mass_tunnel interfaces are 100.100.0.*/32 while the management service is on 10.64.0.* This is causing traffic to head out the external interface. For the primary member this is not an issue, but the secondary keeps disconnecting when the policy is applied. Looking at the connection it is hiding behind the cluster VIP which we don't want it to do. I have tried sk34180 as a workaround/fix for this, but to no avail, as it keeps reverting to hiding the standby's traffic via the VIP.....
But should the traffic for the management service go via the MaaS tunnel?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
What is the best practice to overcome the Standby cluster member can communicate via the MaaS Tunnel?
Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Garbo,
The standby member should communicate through the maas tunnel.
What is the problem that you see in your setup ?
BR
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Rafi,
The current STANDBY cluster member always lost its connection with the Smart-1 Cloud.
It can be reproduced anytime with a controlled cluster failover.
The maas_tunnel disappears from the STANDBY member interfaces when >show interfaces command is executed and appears on the ACTIVE member.
It can be seen in the /var/log/messages file of the new STANDBY member, when initiating a controlled cluster failover:
ntpd[13416]: Deleting interface #10 maas_tunnel, 100.100.xx.yyy#123, interface stats: received=0, sent=0, dropped=0, active_time=932 secs
Thank you and best regards!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I would recommend to check the internet connectivity on the STANDBY member after the failover. Each member should have connectivity to the cloud in order to establish the tunnel and create the maas_tunnel interface. Even if the tunnel went down during the failover, it should go up again. If you have shell prompt, you can test internet connectivity by running curl_cli and also you can inspect what is printed when you run "maas status" command.
BR
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If mass tunnel interfaces Subnets and IP's are different then what configuration we need to do?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @Rajeshk - Can you share more context or specifics regarding your question?
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 2 | |
| 1 | |
| 1 |
Upcoming Events
Tue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter