Voice over IP (VoIP) environments can be difficult to control when firewalls are introduced. Not only can call behavior be unpredictable resulting in a poor user experience when the configuration is incorrect (e.g. one way voice, no way voice, loss of communications, etc.), but it can also be exhaustive and expensive to get the setup right.
The problem mostly stems from VoIP susceptibility to Network Address Translation (NAT) which is carried out by the firewall. What this can lead to is a mix of communications, where some sessions continue uninterrupted while others do not. A common reason that complicates configuration is the diversity of VoIP deployments, as VoIP can actually be deployed in a number of ways.
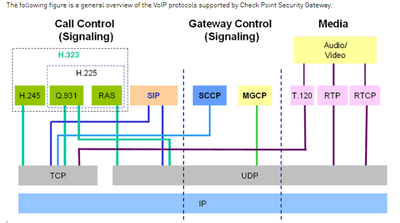
To understand the variety of VoIP deployments, let’s examine its main components. A VoIP network includes three main components the SIP (Session Initiation Protocol) trunk, Private Branch Exchange (PBX), and IP phones. The PBX, among other things, is in charge of routing local calls and allowing short dial numbers between office extensions. The SIP trunk is in charge of providing a range of telephone numbers.
Each VoIP deployment may vary in the following ways:
- The PBX may be placed locally, or externally on the carrier side
- IP Phones may be local or external (remote workers)
- An organization with multiple branches, may use site-2-site VPNs, and place the PBX in one or more of the branches
The type of deployment is often determined by the carrier which provides the VoIP service. For example, here is a deployment where a PBX is positioned inside the company perimeter.
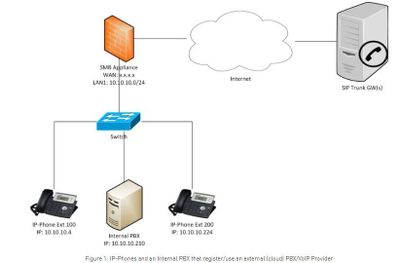
In this example, the deployment requires a few rules that must be configured on the appliance:
- Define network objects of the IP addresses of the carrier’s SIP trunk
- Add access policy rule(s) to allow calls originating from the SIP trunk into the office
- Add NAT rule(s) which tell the firewall how to translate an incoming call destination IP address to the local IP address of the PBX
This may not seem so simple after all, right?
Luckily, Check Point Quantum Spark firewalls have a new VoIP wizard which removes all of the stress and complexity to make configuration effortless. By answering a few simple questions, the VoIP wizard takes care of doing the detailed configuration. These questions include:
- What are the SIP service provider IP addresses?
- Is the PBX on or off-premise?
- And more…
Quantum Spark turns this process, which can often take 1 to 2 hours, into a configuration that is completed in just two minutes.
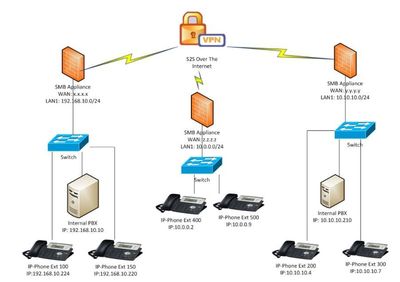
The new VoIP wizard, eases the complexity of building VoIP/SIP environment in the local and external network, and supports diverse topology configurations. The wizard supports 5 different topologies. More information can be found at our support portal.
- IP-Phones (only) behind the firewall that register to an external [cloud] PBX/VoIP Provider.
- IP-Phones and an Internal PBX that register/use an external [cloud] PBX/VoIP Provider.
- IP-Phones and Internal PBX(s) behind multiple sites connected through VPN.
- Soft-Phones and Internal PBX behind multiple sites connected through Client-to-Site VPN.
- External IP-Phones that register to an internal PBX
For more information, check out SK113573
See our blog: https://blog.checkpoint.com/2021/08/10/who-says-voip-configuration-has-to-be-tough/





