- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast Weekly Reports - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
CheckMates Fest 2025!
Join the Biggest Event of the Year!
Simplifying Zero Trust Security
with Infinity Identity!
Operational Health Monitoring
Help us with the Short-Term Roadmap
CheckMates Go:
Recently on CheckMates
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- SMB Gateways (Spark)
- :
- VPN S2S from CP 1550 to FG 30E not PING
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
VPN S2S from CP 1550 to FG 30E not PING
Hello,
I have a configured and active VPN tunnel between CP 1550 and FG 30E (VPN Site to Site)
The tunnel is active with FG I can ping and access the network on the Checkpoint side. However, I cannot ping from Chackpoint to Fortigate.
I attach entries in the firewall in the post.
13 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why the second Outgoing Rule - Source behind FG target CP ??? And i see no rules defined in incoming & VPN traffic, so i wonder how this should work ?
I would just follow Quantum Spark 1500, 1600 and 1800 Appliance Series R80.20.25 Locally Managed Administration Guide pp.26ff !
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just follow the admin guide - i think your manual rules are wrong... Usually, no manual routing is needed as we have a VPN community.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
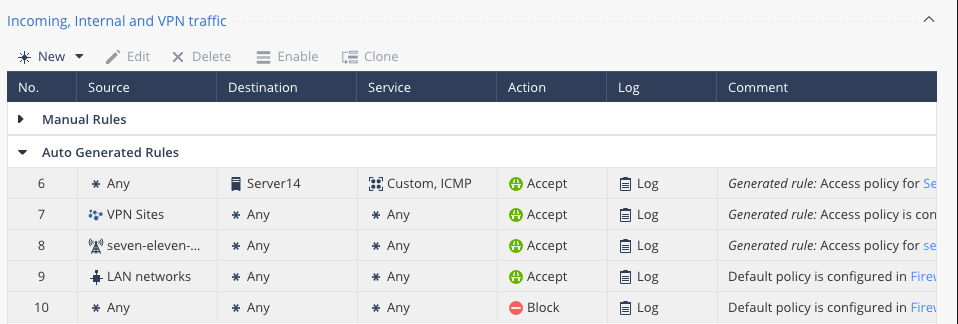
This is part of my rulebase from 1550, Policy normal, VPN working:
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
As you saw on the screen sent by me, I have the same rules.
With time, I added manually the ones that you can see.
Since I can ping from the FG 30E side, the Checkpoint network (I have access to LAN) insists that IKE Phase 1 and Phase 2 are ok on both sides.
It looks like the CP 1550 is not letting traffic into the VPN tunnel from its LAN, although the LOGs show that traffic is entering the tunnel but no response.
I also don't understand that I am getting an error on my VPN test.
If I had an error in IKE Phase 1 or Phase 2 configuration, the connection would not be active and I certainly wouldn't be able to get from the FG 30E LAN to the CP 1550 network.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
When the Check Point attempts to initiate the tunnel to Fortigate the proposed subnets/Proxy-IDs in IKEv1 Phase 2 must PRECISELY match how the Fortigate is configured, whereas if the Fortigate initiates the tunnel the Check Point will accept a subset of the Phase 2 subnets in lieu of a precise match and still allow the VPN tunnel to start. There have been numerous prior CheckMates threads about this, see scenario #1 of sk108600: VPN Site-to-Site with 3rd party
Attend my 60-minute "Be your Own TAC: Part Deux" Presentation
Exclusively at CPX 2025 Las Vegas Tuesday Feb 25th @ 1:00pm
Exclusively at CPX 2025 Las Vegas Tuesday Feb 25th @ 1:00pm
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
So I have to execute the command in the console: disabling the R80.20 "disable supernetting per community
---
This new feature will still work once ike_enable_supernet is set to "true".
Access the relevant gateway.
Run fw ctl set int enable_supernet_per_community 0
Note: It can take some time until user.def tables start to take effect, as current connections can still invoke tunnels using the old ranges.
In order to save this change after reboot of the gateway, set this configuration variable: "enable_supernet_per_community = 0" in the $ FWDIR / boot / modules / fwkern.conf file of the gateway.
---
This also applies to my firmware
R80.20.20 (992001869)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
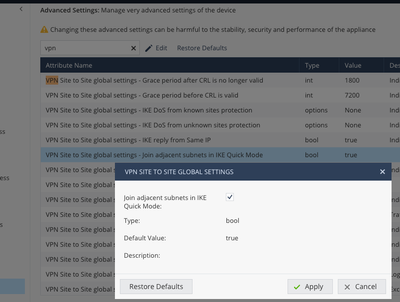
There is also an Advanced Setting that may help:
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
The setting you suggest is already running. It didn't change anything.
I still have FG to CP traffic but no CP to FG traffic.
Could I only have the option to edit the crypt.def file and change the ike_enable_supernet is set parameter to "true".
Will I do it via the console? However, am I forced to set up a GAIA server?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No, you have to uncheck the option ! This is the default and makes trouble with some 3rd party GWs...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Read my last post again. The IKE Phase 2 subnet proposals from the CP must exactly match those on the Fortigate or it will silently discard your Phase 2 proposal and appear to not be responding. You need to set subnet_for_range_and_peer.
Attend my 60-minute "Be your Own TAC: Part Deux" Presentation
Exclusively at CPX 2025 Las Vegas Tuesday Feb 25th @ 1:00pm
Exclusively at CPX 2025 Las Vegas Tuesday Feb 25th @ 1:00pm
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The only way forward is to contact TAC to resolve this issue - locally managed SMBs can not set subnet_for_range_and_peer in user.def. You can try crypt.def, but it does not contain these lines:
#ifndef __user_def__ #define __user_def__ // // User defined INSPECT code // #endif /* __user_def__ */
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 3 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Tue 18 Feb 2025 @ 03:00 PM (CET)
Why Adding SASE to Your Network Infrastructure is a Win-Win - EMEATue 18 Feb 2025 @ 02:00 PM (EST)
Why Adding SASE to Your Network Infrastructure is a Win-Win - AMERICASWed 19 Feb 2025 @ 10:30 AM (BRT)
Explore o Futuro da Segurança Cibernética com o Quantum Firewall R82 - BrasilThu 20 Feb 2025 @ 11:00 AM (EST)
Tips and Tricks 2025 #2 - Controlling Access to SaaS Apps with Harmony SASETue 11 Mar 2025 @ 11:00 AM (IST)
Penetration Testing as a Service – Continuous Security for Evolving Threats - EMEATue 11 Mar 2025 @ 06:00 PM (IST)
TechTalk: The Future of Browser Security: AI, Data Leaks & How to Stay ProtectedTue 18 Feb 2025 @ 03:00 PM (CET)
Why Adding SASE to Your Network Infrastructure is a Win-Win - EMEATue 18 Feb 2025 @ 02:00 PM (EST)
Why Adding SASE to Your Network Infrastructure is a Win-Win - AMERICASWed 19 Feb 2025 @ 10:30 AM (BRT)
Explore o Futuro da Segurança Cibernética com o Quantum Firewall R82 - BrasilThu 20 Feb 2025 @ 11:00 AM (EST)
Tips and Tricks 2025 #2 - Controlling Access to SaaS Apps with Harmony SASETue 11 Mar 2025 @ 11:00 AM (IST)
Penetration Testing as a Service – Continuous Security for Evolving Threats - EMEATue 11 Mar 2025 @ 06:00 PM (IST)
Penetration Testing as a Service – Continuous Security for Evolving Threats - AmericasAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter