- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
10 December @ 5pm CET / 11am ET
Announcing Quantum R82.10!
Learn MoreOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- SMB Gateways (Spark)
- :
- Anti-Spoofing detection
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Anti-Spoofing detection
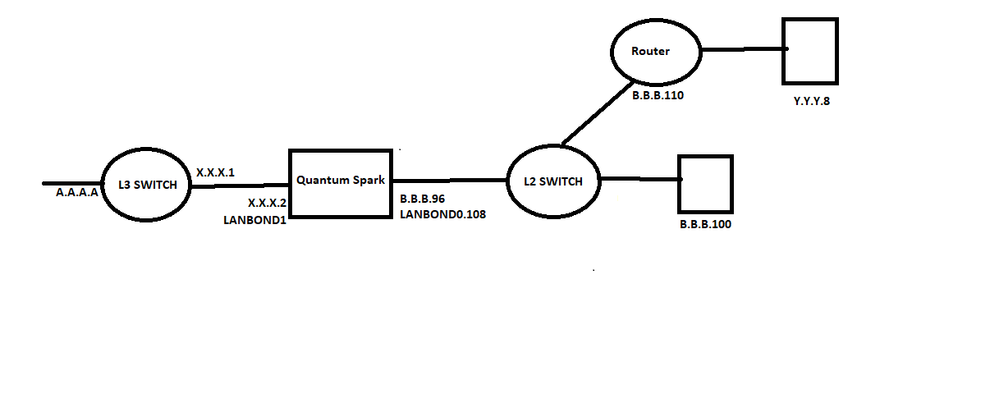
We've systems in the subnet A.A.A.A which is not directly connected with the firewall. While generating traffic from those systems (A.A.A.A) to servers behind the firewall (B.B.B.B), firewall blocks the traffic with the reason "anti spoofing". After disabling anti-spoofing feature, it's allowed.
Hope, Anti-Spoofing detects if a packet with an IP address that is behind a certain interface, arrives from a different interface. In our topology, network A.A.A.A not behind any firewall interface, so why we're getting anti-spoofing detect. Attached our topology.
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
TAC unable to find root cause of the issue. They recommended to upgrade the firewall version. After upgraded firewall to latest version, issue got resolved.
Thanks all.
11 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Anti spoofing verify that each packet arrived with src IP is really configured to be behind the ingress interface.
so if A.A.A.A arriving to the FW from the left interface in diagram, you need to enter this interface in smartconsole (assuming you are centrally managed) , and configure inside the networks behind this interface (the point to point + any subnets behind it).
any other subnets that not explicitly configured would expect to arrive only via the external interfaces.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Amir,
So you mean, all the subnets which is not directly connected with firewall like A.A.A.A will be detected as Spoof?
Also, our quantum spark 1600 security appliances is locally managed, how to permit the external subnets like A.A.A.A in locally managed firewall?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think it uses the routing table also as information for AS. So if you add the networks there the will be allowed.
I cannot find it in documentation so I dont have an example.
-------
Please press "Accept as Solution" if my post solved it 🙂
Please press "Accept as Solution" if my post solved it 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Lesley,
For return traffic, I already have static route to A.A.A.A subnet with the next hop as X.X.X.1. But still the traffic detected as Spoof.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You mention "network A.A.A.A not behind any firewall interface," -- for the purposes of anti-spoofing, A.A.A.A is behind your X.X.X.2 interface.
The anti-spoofing configuration is typically going to be consistent with your routing table as far as what network topology is defined "behind" which interfaces.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think, anti-spoofing is evaluating the traffic based on interface type. By default external interface will allow all the external traffic except internal interface subnet and internal interface permit only directly connected network.
We are locally managing the firewall, Hence we unable to select interface type. It's undefined. So how, Anti spoof evaluate traffic from undefined interface? May be it's considering undefined interface as Internal?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You need to ensure routes are defined for all subnets that are connected to the LAN and/or DMZ interface (directly or via another hop).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Could you please provide the firmware version and routing table details as relevant to your example?
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Chris,
Details given below.
Firmware version :- R81.10.07
FW-1> show route
Codes: C - Connected, S - Static, R - RIP, B - BGP (D - Default),
O - OSPF IntraArea (IA - InterArea, E - External, N - NSSA),
A - Aggregate, K - Kernel Remnant, H - Hidden, P - Suppressed,
NP - NAT Pool, U - Unreachable, i - Inactive
C B.B.B.96/28 is directly connected, LANBOND0.108
LANBOND0.108
C X.X.X.0/29 is directly connected, LANBOND1
LANBOND1
S A.A.A.0/24 via X.X.X.1, LANBOND1, cost 0, age 3953839
S Y.Y.Y.8/32 via B.B.B.110, LANBOND0.108, cost 0, age 3953839
C 127.0.0.0/8 is directly connected, lo
lo
FW-1>
Source :- A.A.A.19
Destination :- B.B.B.100,
Source :- A.A.A.19
Destination :- Y.Y.Y.8
Both traffic flow detected by AS and dropped.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Are all the concerned addresses from RFC1918 space?
When practical I would also recommend upgrading to R81.10.08 or higher.
I feel like we're otherwise missing something here and perhaps it's something that would be more easily navigated via a remote session with TAC.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
TAC unable to find root cause of the issue. They recommended to upgrade the firewall version. After upgraded firewall to latest version, issue got resolved.
Thanks all.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 4 | |
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter