In the age of the internet of “any” things, the market mandates IoT Security and IoT Trust in a regulated manner. The regulatory landscape for IoT is evolving as many governments realize the risk and possible impact of using insecure IoT assets. Governments seek to mitigate those risks. There are many new governmental regulations for IoT on the horizon. How will IoT decision makers, IoT suppliers and IoT manufacturers handle the challenge? Regulations, directives and other legislative acts are here to improve the security of IoT assets and build trust. Regulatory compliance offers several benefits to both IoT consumers and IoT manufactures. Manufacturers should be aware of these regulations to avoid penalties, fines and reputation damage.
Figure 1: My representation of "Internet of Any Things"
There are many new mandatory and voluntary IoT regulations. They all hold similar key elements and requirements. Here is an infographic of such elements.

Figure 2: Overview of regulatory key elements
Today, I would like to discuss the two biggest regulatory challenges for IoT.
- Resilience. It is of the utmost importance to make the IoT asset itself resilient to cyber threats and attacks. Resilience not only offers better protection, but it also detects security issues in a proactive manner, minimizing possible risks and impact. Attacks on IoT devices can massively impact critical, commercial and governmental operations and this is a real risk. The asset should be hardened with on-device runtime security to prevent zero-day attacks and other malicious threats. The asset should be secured from within, ideally with a minimal footprint, based on the Zero Trust and Zero Tolerance principles, thus making the IoT asset tamper-proof.
- Data protection. Attacks on IoT assets threaten not only the device itself (as described above) but also impact the confidentiality and authenticity of the IoT asset’s data. Think of personal and other sensitive data. In Europe, GDPR adopted in 2018 mandates that vendors obtain “user consent” before collecting data. The Data Act, adopted in February 2022, seeks to prevent the unlawful transfer or access to data. Last but not least, data must only be accessible for authorized users.
Let’s take a deeper look at data. We distinguish in three states of data.
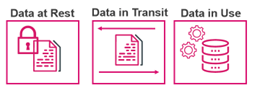
Figure 3: Overview of the 3 state types of data
Data at Rest
- This refers to all data on the device itself and is also known as “inactive data”. Data protection through encryption is a must, along with restrictive security controls with ditto permission to prevent unauthorized usage of data at rest.
Data in Transit
- Data in transit, also known as “data in motion,” is data being transferred to i.e., cloud instances. Data in motion is less secure, as it can be intercepted. This makes it an attractive target for hackers/attackers. Encryption is needed to keep the sensitive data safe.
Data in Use
- This refers to data used by processes/and or users of the IoT asset. It is data being read or processed. This data is regarded to be the most vulnerable, as it is directly accessible. Encryption is also essential here, with additional security controls like authentication, authorization and permissions for data access.
IoT and the Big Data challenge
Why is regulation for data for IoT assets so important? I think we can all understand why. Hackers are real opportunists, as they are always on the lookout to breach assets in very creative ways. As you can see, It is not about the data itself, but also about data communication, how is the data shared, is it encrypted, is it using a secure port, and is it using a secure protocol? I could write another article about M2M, Machine-to-Machine communication. In this scenario, there is no human intervention. In general, monolithic IoT assets are connected to the internet to share data and analytics. With M2M, two or more grouped IoT assets are connected to the internet to share data and analytics. In this environment AI, Artificial Intelligence and ML, Machine Learning is used to facilitate communication and make autonomous decisions. Example: predictive maintenance (to boosting operation efficiency for example) AI is making an informed decisions based on the data.
Dedicated IoT security is a must to maintain a good security posture
In the below infographic that I created, you can see what the attack vector to which asset and threat actor is and finally what the gain would be. It is a high-level infographic which I often use to discuss possible risks and attacks.

Figure 4: Risk and impact infographic
Conclusion
With the adoption of IoT the following elements: encryption, authentication and integrity are a must to keep data safe in all states (in transit, data in use and data in rest). Legislative acts, both mandatory and voluntary will help to build trust for both consumers and organizations. They will build trust that not only applies to the security of the IoT asset itself, but that also pertains to how data is used, handled, protected and so on. This is needed now more than ever, as human reliance on IoT assets is immense and cross vertical. It is not only about assets in healthcare but also smart homes, smart offices and smart cities. Compliance, regulations and security are required to build robust, resilient and secure IoT assets. We are here to help.






