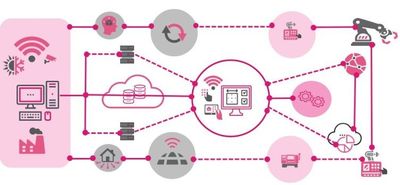
Figure 1: Example overview of OT assets
Reassessing OT Cyber attacks
OT (Operational Technology), Industrial networks or ICS (Industrial Control System) networks are completely different to IT networks. OT environments have other requirements and needs compared to IT environments. Below and overview of the differences between those 2 worlds.

Figure 2: Overview IT vs OT requirements
The challenges differ too, in below infographic I have grouped some of those challenges.

Figure 3: Example overview of OT challenges
Assessing risks in these complex environments is difficult. OT networks are very static and the life cycle of assets is very long in this realm. Think of assets such as RTUs (Remote Terminal Units), PLCs (Programmable Logic Controllers), HMIs (Human Machine Interfaces) and IEDs (Intelligent Electronic Devices). Hackers know about these challenges. Hackers or attackers are looking for ways to exploit outdated software and vulnerable ICS assets. To attack, infiltrate and compromise OT networks. In 2022 manufacturing was one of the most targeted Operational Technology verticals.
The OT Threat Landscape
GhostSec | GhostSec is claiming to be the first to encrypt an RTU, Remote Terminal Unit using ransomware. An RTU is a critical asset in the OT/SCADA environment. An RTU is situated at level 1 of the Purdue model.
- A Hacktivist group with political attribution used a simple breach technique to compromise the RTU, as the device came with a weak preconfigured root password.
- Target | Internet-exposed devices in Russia, Kazakhstan and Belarus
- Risk | Hacktivist group demonstrated the ability to disrupt business and operation. Impacting productivity and safety within industrial automation settings.
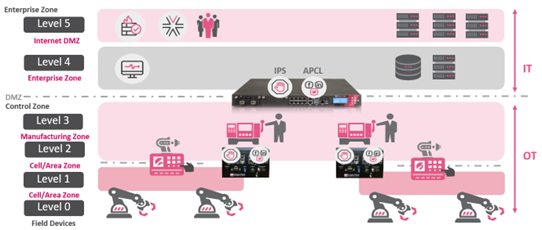
Figure 4: Purdue Model
INDUSTROYER.V2 | This specific “OT malware” crafts configurable IEC-104 Application Service Data Unit (ASDU) messages (AKA telegrams) to change the state of a remote station’s Information Object Addresses (IOAs) to ON or OFF. IOAs identify a specific data element on a device and may correspond to power line switches or circuit breakers in an RTU or relay configuration. In other words, it could communicate and manipulate the RTU over TCP. IEC-104 is used for power system monitoring and control over TCP. IEC-104 is mainly implemented in Europe and the Middle East.
- Target | Energy facilities
- Risk | Infiltrate and compromise critical infrastructures, with the option to analyze the targeted environment and offering tools for manipulation of assets in the critical infrastructure.

Figure 5: Example OT setup using IEC-104
INCONTROLLER (aka PIPEDREAM) | ICS attack toolset which allows communication, access and manipulate Schneider Electric, Omron PLCs and OPC assets. It can manipulate PLCs and industrial software. It is very likely state sponsored. Offering capabilities related to disruption, sabotage and potentially physical destruction. The toolset consists of:
1. TAGRUN - Is a tool that scans for OPC servers, enumerates OPC structure & tags, brute forces credentials and read/write OPC tag values
2. CODECALL – Is a framework that communicates via Modbus, the most common industrial protocol and Codesys. CODECALL contains modules to attack at least three Schneider Electric PLCs.
3. OMSHELL – Is also a framework with capabilities to communicate and scan some types of Omron PLCs via HTTP (port 80), Telnet (port 23), and Omron FINS protocol (port 9600).
- Target | Energy facilities
- Risk | Disrupt and shutdown operations, reprogram PLCs to sabotage industrial processes and disable safety controllers to cause physical destruction

Figure 6: Incontroller/pipedream infographic ploted on Purdue model
OT:ICEFALL | Forescout researchers released a report about 56 vulnerabilities caused by insecure-by-design practices in the OT realm. The vulnerabilities are divided into four main categories:
1. insecure engineering protocols
2. weak cryptography or broken authentication schemes
3. insecure firmware updates
4. RCE (Remote Code Execution) via native functionality
- Target | oil and gas, chemical, nuclear, power generation and distribution, manufacturing, water treatment and distribution, mining and building automation.
- Risk: exploitation of security flaws, which can lead to:
- RCE, Remote Code Execution
- Compromised assets (bots or zombies can participate in DDoS attacks)
- Corrupt and exploit vulnerable firmware
- Credential theft
- Poor authentication or bypass authentication
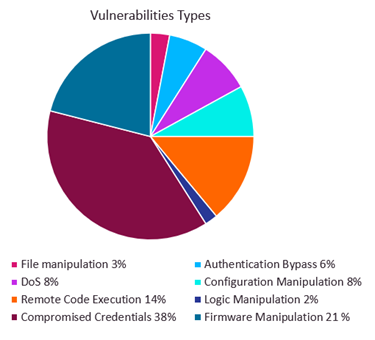
Figure 7: Overview of Icefall vulnerabilities
RSOCKS Proxy Botnet | This Russian botnet is dismantled by the FBI. The compromised assets (350.000 devices), bot or zombie were sold as high quality proxies. The threat actor mechanism is similar to Mirai, exploiting known vulnerabilities and weak credentials. Under compromised assets there were OT assets and consumer assets.
- Target | Industrial control systems, IoT devices and much more from PCs to Android devices
- Risk | Compromised assets may participate in malicious activities such as DDoS

Figure 8: Overview of RSOCKS Proxy Botnet
Other attacks mentioned our Threat Intelligence Report by Check Point Research are |
- Semikron, a German manufacturer of power modules and systems, has been targeted by the LV ransomware group. In a statement, Semikron confirmed that an attack caused partial encryption of files, and that the hacker group claim to have exfiltrated data.
- LV ransomware gang has launched an attack against Finland-based company Wartsila, one of the largest manufacturers of machinery and electrical equipment for the marine and energy markets worldwide. More than 2000 GB of data were leaked.
- The Largest copper manufacturer in Europe Aurubis - has been the victim of a cyberattack that targeted its IT systems and forced the company to shut down many of its sites systems.
- RansomEXX Ransomware group claims to have stolen over 7GB of data belonging to the Italian luxury sports car manufacturer Ferrari. The stolen data allegedly include contracts, invoices, internal company information, repair manuals and more. A Ferrari spokesperson confirms the data leak, but denies being a victim of a ransomware attack.
Gartner predicts that attacks resulting in fatal casualties will reach over $50 billion by 2023. Even without taking the value of human life into account, the costs for organizations in terms of compensation, litigation, insurance, regulatory fines and reputation loss will be significant. Gartner also predicts that most CEOs will be personally liable for such incidents.
Conclusion
To secure critical infrastructures and OT environments, topics like the IT/OT convergence, policies, remote access (RA), compliance and processes should be addressed. I always talk about the four “Ps”, processes, protocols, procedures and people! Addressing the challenges that come with the four “P’s” ensure safety and availability. Worldwide governments mandate regulations for OT and Industrial IoT assets, which will be a step in the right direction in these very complex environments.










