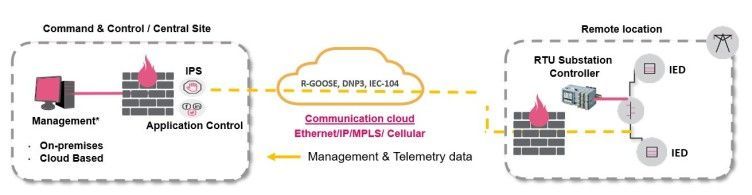
Figure 1: Topology setup for power grids, energy and utilities
Hi experts, happy to share my IoT Insider newsletter on Check Mates. Today, let's talk about the challenges in the Operational Technology, OT realm.
One major challenge is the lack of IP capabilities in many SCADA devices. As technology advances, the need for these devices to be connected to the internet becomes crucial. Without IP capabilities, it can be difficult to integrate them into modern networks and take advantage of the benefits of connectivity. As discussed in an earlier article, the life cycle of RTUs (Remote Terminal Unit) and PLCs (Programmable Logic Controller) are very long and it impossible to detect anomalies as they often run serial protocols over RS-485, RS-232 or RS-422 interfaces. So it would be impossible to check if the shop floor is still compliant with regulations and legislative acts.
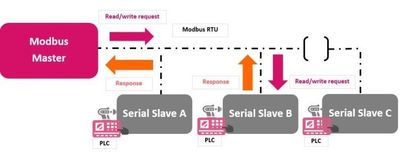
Figure 2: Serial protocol example Modbus
This is a real danger. SCADA systems and ICS environments often operate in critical infrastructure sectors, such as energy, water, manufacturing and transportation. Meeting strict compliance standards and regulations can be a complex task, as these systems handle sensitive data and must ensure the highest level of security. Example: IEC 60870-5-101, a standard for power system monitoring, control & associated communications for tele control, tele protection and associated telecommunications for electric power systems.
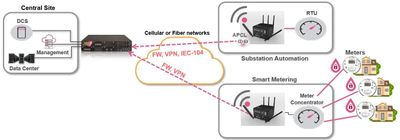
Figure 3: IEC104 protocol for communication between control station (Central Site) to substation
Furthermore, SCADA devices face the challenge of interoperability. Different vendors may have their own proprietary protocols and communication standards, making it challenging for devices from different manufacturers to seamlessly work together. This can hinder the efficiency and effectiveness of the overall environment.
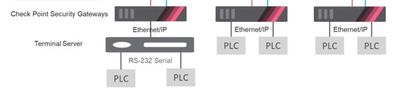
Figure 4: Secured PLCs via Security Gateways
Additionally, as SCADA devices age, they might may lack the necessary updates and patches to address security vulnerabilities. Legacy devices in air-gapped OT environments refer to older or outdated equipment. Those legacy devices often lack built-in security protocols, making them vulnerable to cyber threats and may pose significant cybersecurity risks. Some legacy devices may have hardcoded or default credentials that cannot be changed. This makes them an easy target for attackers who can gain unauthorized access using these credentials.
Despite these challenges, the industry is actively working towards solutions. IP-enabling legacy SCADA devices, implementing robust security measures, and adopting standardized protocols are steps being taken to improve the overall security and efficiency of SCADA systems. And we see a lot of OT environments joining the cloud journey. Which opens up a complete new world!
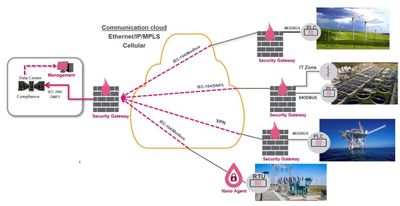
Figure 5: Distributed topology setup of energy and utilities
Let's continue to raise awareness about these challenges and work together to overcome them, ensuring the safety and reliability of our critical infrastructures and OT realms. Stay vigilant in detecting and addressing traffic anomalies, safeguarding the integrity and resilience of our industrial systems.







