|
Critical Vulnerability in Windows OS - Code execution using Remote Desktop Protocol (CVE-2019-0708)
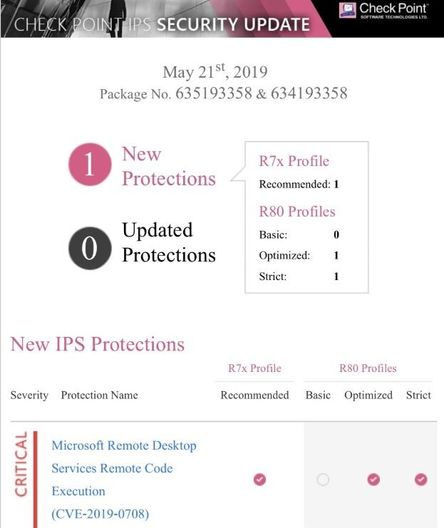
****IPS protection NOW AVAILABLE****
In Brief
In the last few days, Microsoft has released information about a critical vulnerability in the Windows operating system (CVE-2019-0708). This vulnerability allows remote code execution by an attacker directly from the network using the Remote Desktop Protocol (RDP) in remote desktop services that affects older versions of windows used by many users worldwide. This attack may effect many computers in every sector and industry including finance, healthcare, government, retail, industrial and others.
Key Risks:
- An arbitrary attacker from the net can carry out a complete takeover of a private PC within public networks, such as Wi-Fi hotspots.
- Embedded devices such as ATMs or IoT Devices are most vulnerable for takeover.
- PCs within organization’s network are also vulnerable to a takeover using lateral movement within the network.
Why Is This So Important?
As this vulnerability is placed at the pre-authentication stage and does not require any user interaction it would allow any arbitrary attacker on the internet to execute malicious code on a victim’s private system and allow for a total takeover of a PC within any network, such as Wi-Fi hotspots, public networks and private and corporate networks.
According to Microsoft in order to exploit this vulnerability, an attacker would have to send a specially tailored request to the target systems’ Remote Desktop Service via RDP. Given the nature of the vulnerability, once a host is infected there is great risk of lateral movement to infect other connected hosts on the same network.
To clarify the potential exploitation of this vulnerability, it could be used in a very similar manner as that of the 2017 WannaCry attack that caused catastrophic disruption and sabotage to thousands of organizations across all industries worldwide.
Who Is Affected?
Those using certain versions of Microsoft Windows 7 and Windows Server 2008 are at risk from this vulnerability. Customers running Windows 8 and Windows 10 are not affected by this vulnerability due to these later versions incorporating more secure updates.
Those most at risk, among others, are those working with embedded devices such as ATMs in the banking sector and IoT devices in the healthcare industry. This is due to older versions of Windows known to be the systems behind these operations as well as them being prized targets for cyber criminals. As a result, since this vulnerability was announced, security professionals in hospitals and banks have been working diligently to patch their systems.
How to Protect Yourself
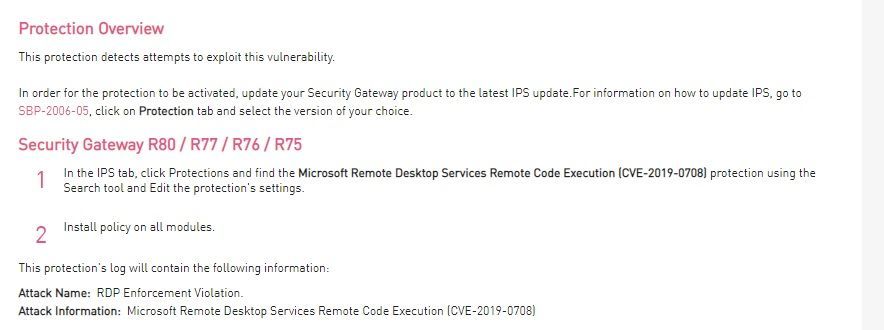
- We have released an IPS protection for CVE-2019-0708 as an immediate response - Click here
- Block the RDP protocol on Check Point gateway product and endpoint SandBlast agent. Instructions for Check Point R77.x and R80.x are detailed in the attached "how to guide" detailed in this post.
- If you are using RDP for mission critical systems – configure the Check Point gateway and endpoint product to accept connections only from trusted devices within your network. Instructions included in the attached "how to guide" detailed in this post..
- Disable RDP on your Windows PC and servers (unless used internally) and deploy the Microsoft patch. Please note that your ability to identify vulnerable systems when used in IoT devices (corporate, finance, industrial and healthcare systems) is limited – therefore it is recommended to follow steps 1 & 2 even if patch is installed.
Currently, while Check Point researchers are investigating this vulnerability and monitoring any relevant activity in the wild, we recommend all IT professionals to deploy Microsoft patches according to the MS Security Update Guide.
See here a quick "how to" guide with detailed step-by-step instructions.
Check Point Security Gateway and Check Point CloudGuard IaaS
We need to decrease the risk by limiting and or blocking the Remote Desktop Protocol service (port 3389).
The following steps are applicable or both Check Point Network Security Gateway and Check Point CloudGuard IaaS products.
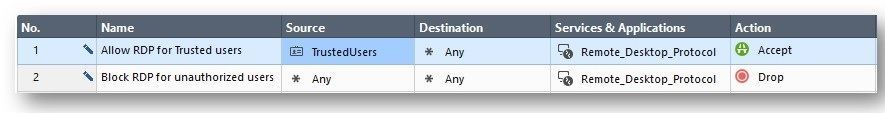
- Open Smart Dashboard
- Define new rule, with Access Role on the source
- Define as specific as possible the source that will use RDP service, such as:
- Users (trusted users)
- Machines: Specific machines within a trusted network
*Note: A combination of both is preferred.
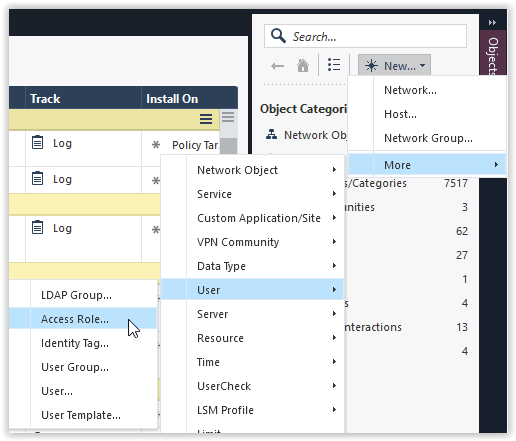
Define trusted Users to use Remote Desktop Protocol service:
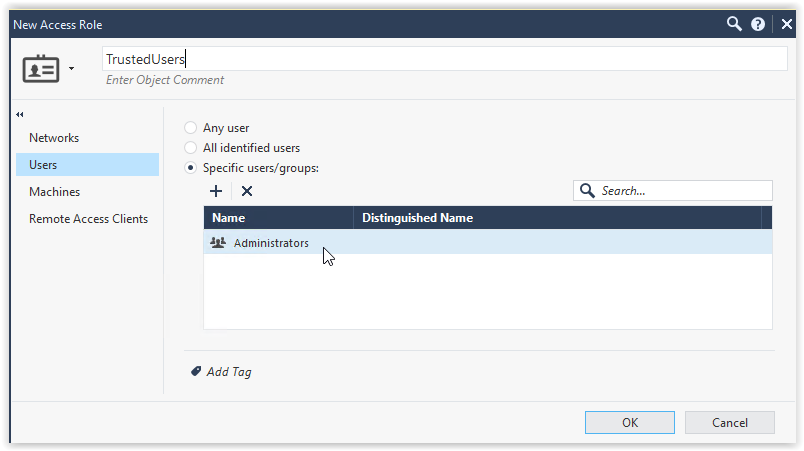
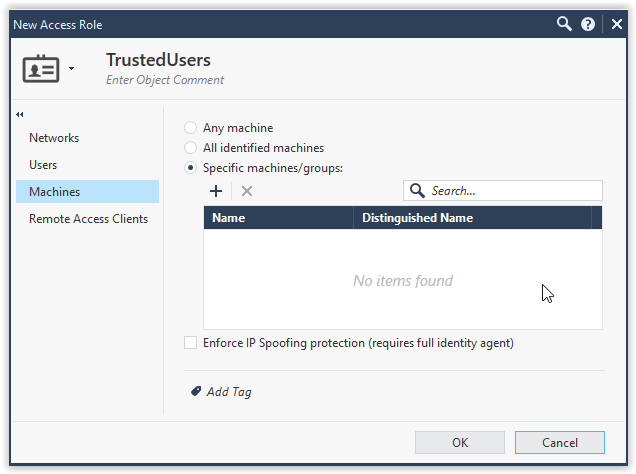
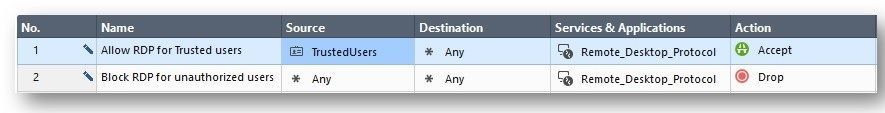
On the Security Policy, in the rule base, make sure 1 rule will allow Remote Desktop Protocol as specific as possible using the Access Rule group as seen in the above screenshots under TrustedUsers-Machines
Check Point Endpoint Security Sandblast Agent
In Endpoint security server, configure the entire organization policy for Firewall to limit remote desktop protocol (3389).
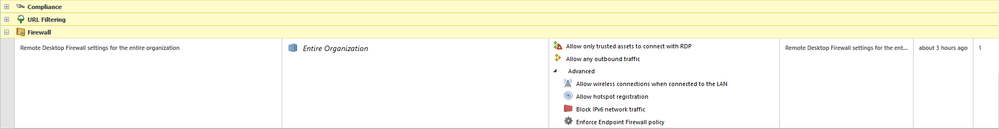
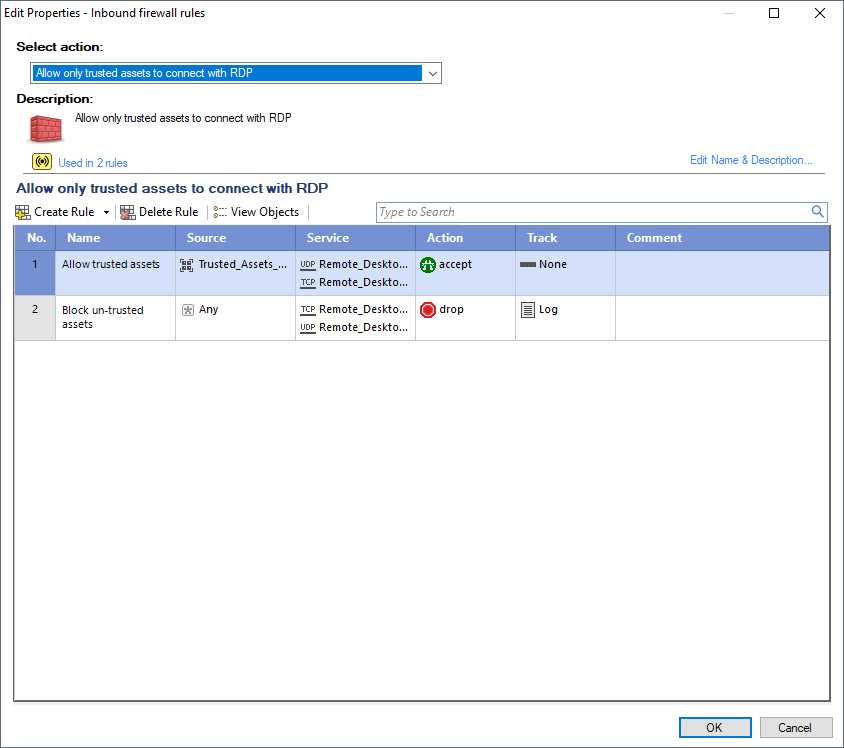
Firewall policy rules to be configured to allow only specific Networks and Machines, and can be applied to specific Users
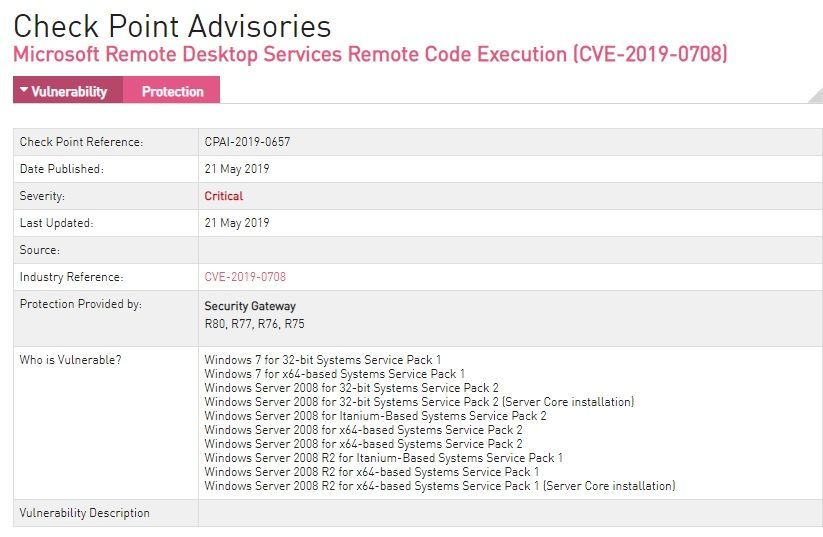
Here are the the OS versions vulnerable according to Microsoft
|
Windows 7 for 32-bit Systems Service Pack 1
|
|
|
Windows 7 for x64-based Systems Service Pack 1
|
|
|
Windows Server 2008 for 32-bit Systems Service Pack 2
|
|
|
Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation)
|
|
|
Windows Server 2008 for Itanium-Based Systems Service Pack 2
|
|
|
Windows Server 2008 for x64-based Systems Service Pack 2
|
|
|
Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation)
|
|
|
Windows Server 2008 R2 for Itanium-Based Systems Service Pack 1
|
|
|
Windows Server 2008 R2 for x64-based Systems Service Pack 1
|
|
|
Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation)
|
|
|