- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Access Control and Threat Prevention Best Practices
5 November @ 5pm CET / 11am ET
Firewall Uptime, Reimagined
How AIOps Simplifies Operations and Prevents Outages
Overlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Spark Management Portal and More!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Workspace
- :
- Endpoint
- :
- Re: Need to allow all my machine to access local u...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Need to allow all my machine to access local user in FDE machines
Dear Team,
Recently we implemented Endpoint FDE client(E80.85/R80.10) with AD integration. The challenge what I face is, I am unable to login with my local user on all my machines where I installed FDE.
In Smart Endpoint Console I can add AD users, soon after I added the new users to respective machine I am able to login as many users as I want except local user account.
In our organization we created a local user to all client machines, To get the access of all machine when ever we need to do any changes on it.
Local account username: itsecsuport.
If i want access of any machine I can enter this credential for RDP(mstsc).
After installed FDE I am not able to access any machine with local user.
Note: I tested with one client machine, If I installed and logged in for the first time with local user, then after I am able to access with local user and the AD users both. If I installed and logged in for a first time with AD user then I dont.
Do I can enable any feature to identify my local-user on my Endpoint Server to acquire the local user access to all client machines where I installed FDE.
- Arun.R
19 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What is the error you are getting when trying to RDP into the computer that has FDE? Also, what is the algorithm being used for FDE.
I just tested your scenario and I was able to RDP into a fresh built computer with FDE using a local admin account (have not logged into the computer yet with the local account, but is preconfigured) and it worked. I am using FDE XTS-AES 256 Bit/UEFI BIOS/Win10 Enterprise.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dear Steve,
The same algorithm has been used on our premises. But I am getting an error "Account is disabled".
Here I did few testing for my reference:
Test Machine - 1: Logged in with local user and installed the EPM package with admin privilege(AD is integrated). I complete the encryption and logging in with the local user.
Observation: Once the process has been done, I added the AD user to access the machine, post this changes all my AD users are able to access the machine include my local user because my endpoint server learned the local username and as well AD users.
Test Machine - 2: Logged in with AD user and installed the EPM package with admin privilege(AD is integrated). I complete the encryption and logging in with AD user.
Observation: I am unable to log in with local user and I am not able to find this machine local user on Endpoint console, because it is not learned before on my endpoint server.
In the test machine - 2 scenarios I am facing an issue with local user access.
- Arun.R
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
you need to provide the dlog.txt from these machines to see what is causing this issue.
without the dlog, it would be difficult to tell, also the username you used to login would help also.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
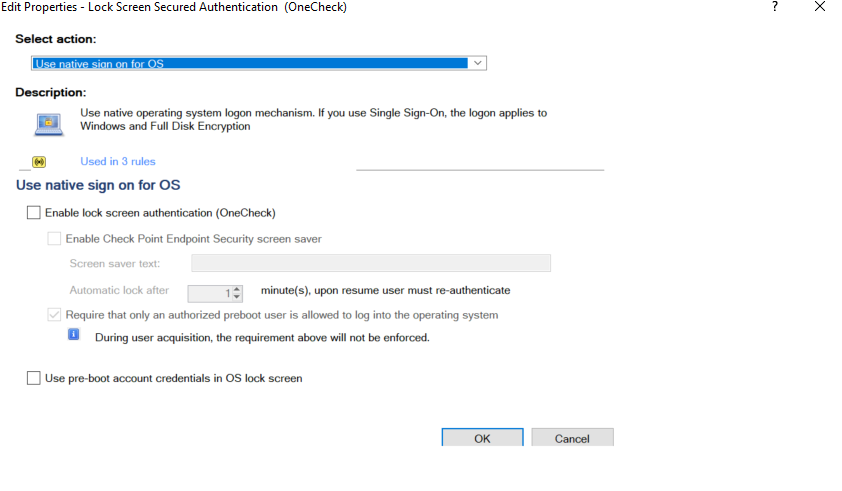
the other thing that can be causing this is the Endpoint policy look for the "Enable Lock Screen Authentication(One Check)" but in the Full Disk Encryption settings
edit this policy and change the settings "required that only an authorized preboot user is allowed to log into the operating system" what this will do is allow any user on domain to login and could be what is causing your issue maybe.
basically un-tick this setting save and install policy, now you need to update the client side and for that to work it needs contact with server to receive this update, once done you should be able to reboot login in with the preboot user and then an AD account should work for you.
let me know if that helps.
Regards
Frank
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Since we use Preboot Authentication, I have this not checked as well, see my screenshot below. As Franco mentioned above, if you enabled this that may be why you are having issues logging in locally since I have no issues.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dear Steve,
Thanks for the assist.
I will check with any one of my client machine if I got any and I will let you know.
- Arun.R
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dear Steve,
This changes starts working, I am able to login with local user.
One more thing I observed is, all my AD users are also starts able to logging in every machines. But we do not want to give a privileged to my users can login every machines once one AD user and local user.
Is it possible.?
Regards,
ArunHari.R
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Arun,
I don't think that is possible to do what you are asking.
local users don't show up in the EP console, so can't be authorized preboot users, and as per the settings "Require that only an authorized preboot user is allowed to login to the operating system" is the fix for you, but as you say it will allow any one in AD to login now.
I don't get why you would need to allow local accounts, there AD account should be enough and it you create your ITSECSUPPORT in AD and add the to the Entire Organization that should allow you to get into any machine for IT people who need it,
worse case you get a user who can't login and you need to use remote help for them.
Frank
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dear Frank,
Thanks for the update.
The reason why I need local user is, The local user have Administrator privileged which it helps me to install the software. When my client machine is not communicate to AD server.
There was a huge conversation with my AD & Windows team and they finalize( AD user will require AD administrator privileged when its connected to AD server if I want to install any software otherwise it will prompt enter local Administrator to install the software).
Due to this I always wanted make sure all the machines to have "itsecsuport" local user access.
- Arun.R
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dear Franco,
As I never facing any issue with AD domain users. If I want to authenticate more than once users, I can add it under preboot authenticate users, therefore all my AD users are able to authenticate easily without any issue.
Endpoint server learn about those user from AD server even though those users are never been log in before in client machine.
However, this suggestion sound good, I will check with my client machine once I got access of any.
- Arun.R
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Arun,
I am pretty sure this will fix it and allow the local user in, I understand they are not found in the EP console but this settings is restrictive in only allowing preboot user into the OS so test it on a machine you know you had an issue with.
clone this policy and change that settings after cloning the settings also not to affect your other clients, and point this rule at your test host only and make sure it receive the update then reboot and login in with the local account.
I expect it will solve this issue.
Frank
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
the other thing you can do is at the top of the domain structure in Endpoint console, authorize itsecsuport as a preboot user to the domain, this will add this user to all machine that get FDE and can be a recovery account for decryption process also and in case the user can not get past preboot you have a IT account there for these issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dear Franco,
If you don't mind, can you share some screenshot where do I need to change for my local user.
And one concern, How do my endpoint will recognize localuser if we never been used to login before.?
But thank you very much for your effort on this, I will check another option which you given.
- Arun.R
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Arun,
itsecsuport will need to be a domain account I did think you could use a local account, but that wont work for you
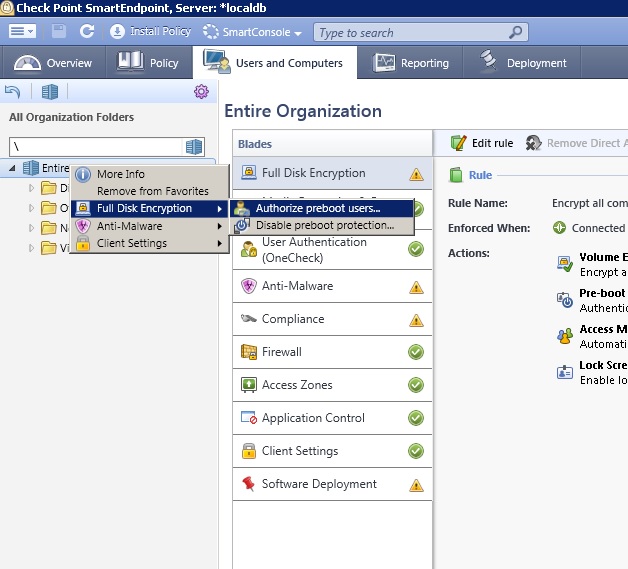
but this will be looking at your domain to add the ITSECSUPPORT acount not the local account on machine, that other setting I mentioned should fix the local account and allow you to login to Windows OS not preboot tho.
Frank
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dear Franco,
Thanks for sharing.
I will check it out once got any client machine to test.
- Arun.R
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Arun,
The reason why I need local user is, The local user have Administrator privileged which it helps me to install the software. When my client machine is not communicate to AD server. -
ok understood but nothing stops you doing a runas when in the machine that will not be blocked so I think use the right click and hold shift down will offer you to run as administrator.
There was a huge conversation with my AD & Windows team and they finalize( AD user will require AD administrator privileged when its connected to AD server if I want to install any software otherwise it will prompt enter local Administrator to install the software).
AD administrator to install software ? or local admin ? Runas is your fix here.
Due to this I always wanted make sure all the machines to have "itsecsuport" local user access.
best way for itsecsupport to be on all machines is add it to Entire organization as an authorized preboot user to the whole domain will give you this.
Frank
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dear Frank,
I always wanted make sure all the machines to have "itsecsupport" local user access.
best way for itsecsupport to be on all machines is add it to Entire organization as an authorized preboot user to the whole domain will give you this.
I tried this way and I am able to see that local User in Endpoint Server, But the challenge is, Machine-1 shows "ITSeecsupprt" but I am unable to use in Machine-2 as its integrated only AD user, Even after its same if I am adding current existing "ITSeecsupprt".
Because this "ITSeecsupprt" is not belongs to Machine-2 its belongs to machine-1.
When I checked under Other users and computer folder I am able to see many "ITSeecsupprt" users as each represent each machine local user, as its not same for all.
There was a huge conversation with my AD & Windows team and they finalize( AD user will require AD administrator privileged when its connected to AD server if I want to install any software otherwise it will prompt enter local Administrator to install the software).
AD administrator to install software ? or local admin ? Runas is your fix here.
If i am installing some software when the machine is connected to AD Server , it expect me to enter AD administrator privilege, whereas its quite opposite when the machine is not connected to AD Server ((ex: When the machine is roaming out of office) it expected me to enter local user Admin privilege).
Due to this issue, I have to make sure of both accesses (Local Admin i.e ITSeecsupprt and AD admin privilege).
-Arun.R
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Arun,
Because this "ITSeecsupprt" is not belongs to Machine-2 its belongs to machine-1. remove this users from the endpoint server can you delete them ? also I would create this user in AD "ITSeecsupprt" so it will be available to all machines.
Due to this issue, I have to make sure of both accesses (Local Admin i.e ITSeecsupprt and AD admin privilege).
this users needs to be created in AD to be able to be shared across the entire organization, also then I would undo the tick I mentioned "required that only an authorized preboot user is allowed to log into the operating system"
this will give you what you want, ITSeeCsupprt will have to be a local admin to all machines, and in AD to be available across all EP machines.
then you can un tick that option above, this will give you an admin account ITSeeCsupprt, and also stop the issue of any AD users being able to login.
this sounds like the best you can do to me.
Frank
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dear Frank,
Thank you so much you effort on this.
I will check with my test machine and will get back to you.
- Arun.R
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Wed 05 Nov 2025 @ 11:00 AM (EST)
TechTalk: Access Control and Threat Prevention Best PracticesThu 06 Nov 2025 @ 10:00 AM (CET)
CheckMates Live BeLux: Get to Know Veriti – What It Is, What It Does, and Why It MattersTue 11 Nov 2025 @ 05:00 PM (CET)
Hacking LLM Applications: latest research and insights from our LLM pen testing projects - AMERTue 11 Nov 2025 @ 10:00 AM (CST)
Hacking LLM Applications: latest research and insights from our LLM pen testing projects - EMEAAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


