- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Workspace
- :
- Endpoint
- :
- Endpoint SFTP Log Collection
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Endpoint SFTP Log Collection
Hi,
I'm trying to perform remote log collection & uploading to a corporate SFTP server.
This works perfectly well when uploading to a username & password protected FTP, but obviously it'd be better to utilize SFTP in this day and age.
Unfortunately it appears that SFTP pushes utilize libssh2 1.8.2 which seemingly struggles on the Key exchange algorithm part when connecting to an OpenSSH 7 server.
Would you happen to know which KexAlgorithm I need to permit on the server side of things to get this working or better yet, are there any plans for updating the libssh2 used?
Given that we manage a number of customers, it would often speed up the troubleshooting process considerably to just collect logs without having to find time with the end user.
Best regards,
Luka
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We had contacted TAC on the matters and it appears the issue is a component of CPInfo in the Endpoint Client.
TAC was able to reproduce the issue and produced a .dll we can use to patch existing installations.
The change is likely to be included with the E86.40 release, but more likely E86.50.
13 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 29 14:43:27 hostname sshd[3813]: debug1: Forked child 558.
Jan 29 14:43:27 hostname sshd[558]: debug1: Set /proc/self/oom_score_adj to 0
Jan 29 14:43:27 hostname sshd[558]: debug1: rexec start in 5 out 5 newsock 5 pipe 7 sock 8
Jan 29 14:43:27 hostname sshd[558]: debug1: inetd sockets after dupping: 3, 3
Jan 29 14:43:27 hostname sshd[558]: Connection from 10.8.32.1 port 10014 on 10.15.5.55 port 22
Jan 29 14:43:27 hostname sshd[558]: debug1: Client protocol version 2.0; client software version libssh2_1.8.2
Jan 29 14:43:27 hostname sshd[558]: debug1: no match: libssh2_1.8.2
Jan 29 14:43:27 hostname sshd[558]: debug1: Local version string SSH-2.0-SSH
Jan 29 14:43:27 hostname sshd[558]: debug1: Enabling compatibility mode for protocol 2.0
Jan 29 14:43:27 hostname sshd[558]: debug1: SELinux support disabled [preauth]
Jan 29 14:43:27 hostname sshd[558]: debug1: permanently_set_uid: 74/74 [preauth]
Jan 29 14:43:27 hostname sshd[558]: debug1: list_hostkey_types: ssh-rsa,rsa-sha2-512,rsa-sha2-256,ecdsa-sha2-nistp256,ssh-ed25519 [preauth]
Jan 29 14:43:27 hostname sshd[558]: debug1: SSH2_MSG_KEXINIT sent [preauth]
Jan 29 14:43:28 hostname sshd[558]: debug1: SSH2_MSG_KEXINIT received [preauth]
Jan 29 14:43:28 hostname sshd[558]: debug1: kex: algorithm: diffie-hellman-group-exchange-sha256 [preauth]
Jan 29 14:43:28 hostname sshd[558]: debug1: kex: host key algorithm: ssh-rsa [preauth]
Jan 29 14:43:28 hostname sshd[558]: debug1: kex: client->server cipher: aes128-ctr MAC: hmac-sha2-256 compression: none [preauth]
Jan 29 14:43:28 hostname sshd[558]: debug1: kex: server->client cipher: aes128-ctr MAC: hmac-sha2-256 compression: none [preauth]
Jan 29 14:43:28 hostname sshd[558]: debug1: kex: diffie-hellman-group-exchange-sha256 need=32 dh_need=32 [preauth]
Jan 29 14:43:28 hostname sshd[558]: debug1: kex: diffie-hellman-group-exchange-sha256 need=32 dh_need=32 [preauth]
Jan 29 14:43:28 hostname sshd[558]: debug1: expecting SSH2_MSG_KEX_DH_GEX_REQUEST [preauth]
Jan 29 14:43:28 hostname sshd[558]: error: kex protocol error: type 30 seq 1 [preauth]I went ahead and switched LogLevel to "DEBUG" in sshd_config & this is what I get in /var/log/secure when attempting to push the CPInfo
I've added KexAlgorithms, Ciphers & MACs to the end of sshd_config & still experience the same issue. Any clue where I'm actually getting stuck?
KexAlgorithms diffie-hellman-group-exchange-sha256
Ciphers aes128-ctr
MACs hmac-sha2-256
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A kind user on Reddit linked https://serverfault.com/questions/592059/debug1-expecting-ssh2-msg-kex-dh-gex-group#697350 & https://superuser.com/questions/568891/ssh-works-in-putty-but-not-terminal
These both point towards an MTU mismatch being the root cause of such an issue. As we're currently working from home I was performing the tests over VPN which has an interface at 1350 MTU.
To cut out any strangeness, I went ahead and deployed a little SFTP server at home & ran the test with both interacting interfaces at 1500 MTU.
Got practically an identical log. Soo, that's probably not it either.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Seems no CP product is part of your question - why not ask this in a more appropriate place for SFTP issues ?
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I support SmartEndpoint and it's associated client don't fall under CP products? I'm merely presenting the fileserver side of the affair as that's the end where I'm able to capture a debug log. (Unless of course there's a log available within the context of the Endpoint Security client)
Let me re-word the question then, how can I make the "Collect logs" push operation work with SFTP?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can not make the "Collect logs" push operation work with SFTP. It only collects the logs into a CAB file and shows it to you. For SFTP transfer you have to use other tools. SmartEndpoint and it's associated client can not help here...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why does it work with FTP then?
The log files on the endpoint are collected then pushed to an FTP server of my choosing.
Here's my "workflow" for FTP pushes.
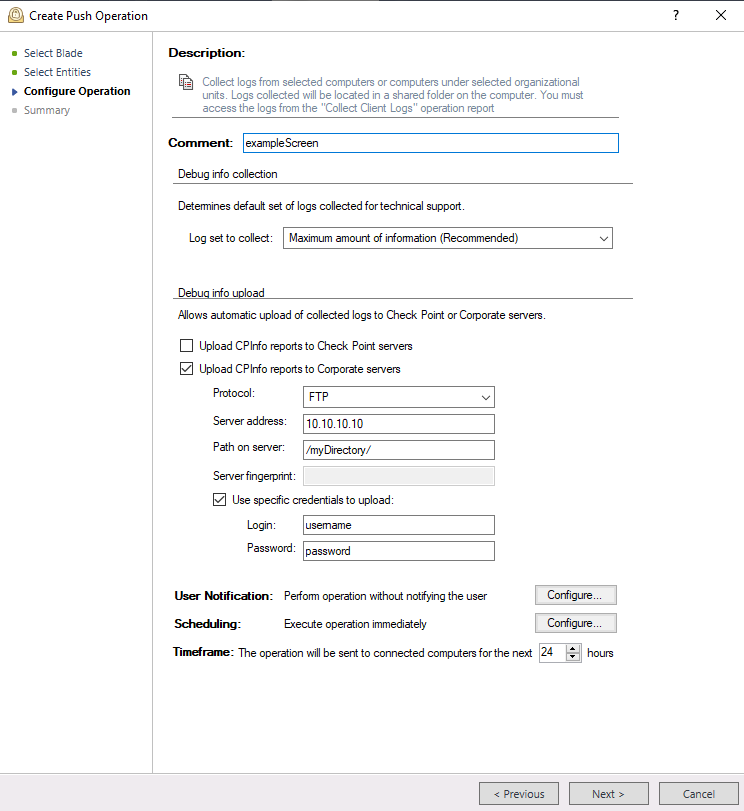
1) Log into SmartEndpoint
2) Open the "Reporting" tab -> "Push Operations" -> "Create New"
3) Select "Client Settings, Collect Client Logs" -> Next & under "Select Entities" select the target machines hostname
4)
With "Protocol" selected as FTP this will work as expected.
CPInfo will be collected and ZIPPED on the Endpoint. The Endpoint will upload the collected logs to the specified FTP server.
If I select "Protocol" to "SFTP" the CPInfo will be collected and ZIPPED on the Endpoint. The Endpoint will ATTEMPT to upload the collected logs to the specified SFTP server, however it will fail at doing so with the log in my initial posts showing up on the SFTP server.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry, now i understand what you are trying to do ! I thought you were collecting on client side. I would suggest to contact TAC !
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I suppose I shall.
Would you happen to know what the "best practice" for Question Type tickets is with TAC?
I have several questions to ask, but should I split them into individual tickets or is it okay to only open one "megaticket".
Though the questions I have currently all apply to Push Operations in one way or another.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This depends on the issue / topic - basically, CP expects one ticket for one issue to be able to involve the most specialized team. If your bundle of questions are all about EPS push operations, i would open a TAC ticket severity medium for e.g. this issue. During a RAS, you will be able to talk to the engineer and, after resolving the issue, ask your other questions 8)
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We had contacted TAC on the matters and it appears the issue is a component of CPInfo in the Endpoint Client.
TAC was able to reproduce the issue and produced a .dll we can use to patch existing installations.
The change is likely to be included with the E86.40 release, but more likely E86.50.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What precise version of the management server is in use?
If not at least R80.40, upgrade as a newer Linux kernel is used, allowing for a newer version of OpenSSH.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We're on R81. But I've also attempted this with an Infinity Portal managed deployment of Endpoint Security since we're lucky enough to manage a bit of both.
I'm not uploading to the Management server though, the role of the SFTP server is taken by a generic Debian 10 server.
Rather, I don't think the EPMS is even involved in the process aside from pushing the initial Push Operation to the client, right?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Hope this is relevant to your issue.
I resolved my issue in SFTP into Checkpoint appliance.
On Checkpoint, go to Expert mode, enter “chsh -s /bin/bash”.
Best Regards
David
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 4 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter