- CheckMates
- :
- Products
- :
- CloudMates Products
- :
- CloudGuard - WAF
- :
- CloudGuard AppSec is the only product known to pre...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
CloudGuard AppSec is the only product known to pre-emptively block Claroty WAF bypass
This article originally posted by Oded Gonda, on open-appsec website here.
--
Claroty Team82 has developed a generic bypass for industry-leading web application firewalls (WAF). The bypass technique involves appending JSON syntax to SQL injection payloads that a WAF is unable to parse. It is explained in a detailed blog that was published on December 8th, 2022.
As part of a responsible disclosure process for vulnerabilities, Claroty approached our team with findings of the new bypass technique. Looking at the attack payloads we thought that open-appsec/CloudGuard AppSec ML-engine would block the attack based on the vast training data we use. To validate, we tested it on the same day and indeed it blocked the attack pre-emptively! We sent the product logs to the Claroty team and they confirmed “Thanks for the update. Kudos to the AppSec Team”.
You can read more about the WAF bypass technique in Claroty’s detailed blog. It explains the details of this new bypass vector and how they found that AWS WAF as well as other major WAFs were vulnerable to it:
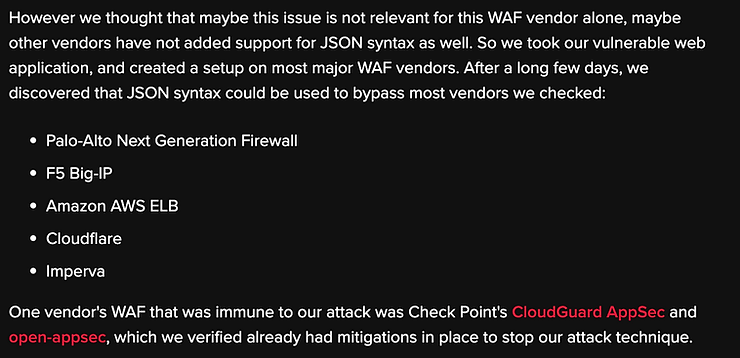
Source: Claroty Team82 Blog
Attack Details
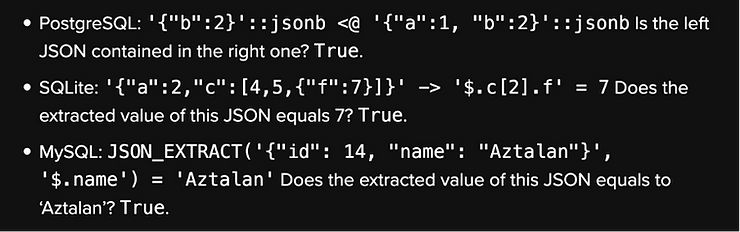
Source: Claroty Team82 Blog
Summary
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks @yuvalmamka that's a wonderful explanation. I am the one who has implemented Appsec when it was pretty new and running in production with around 18 portals.
Blason R
CCSA,CCSE,CCCS


