- CheckMates
- :
- Products
- :
- CloudMates Products
- :
- CloudGuard - WAF
- :
- Re: CloudGuard AppSec Workshop: Step-by-Step Guide
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
CloudGuard AppSec Workshop: Step-by-Step Guide
Hi to all CloudGuarders 😀
It was a great pleasure to meet some of you from America and Europe in our CloudGuard AppSec workshops!
I had a great time deploying AppSec with you and answering questions.
Can't wait to meet the rest of you from Europe and APAC this coming week as well!
As promised, I'm posting here a step-by-step guide for the actions we did in the workshop.
Please note that the demo applications are live and you can use them for practice, but the labs are not - so you will need to use your own Azure subscription.
Prerequisites:
- Login to Azure Portal at: portal.azure.com (create a new tenant in case you don't have one)
- Login to Infinity Portal at: portal.checkpoint.com (create a new tenant in case you don't have one)
- Download the files from this Dropbox folder: https://bit.ly/46stZqb (or you can find them attached in the comments)
- Review the architecture documents (located in the Dropbox folder)
- Deploy a demo website to protect using this post: https://community.checkpoint.com/t5/Application-Security/Vulnerable-applications-for-testing-Guide/t...
Deploy AppSec Single Gateway:
Create a New Profile
- Inside Infinity Portal, click on Cloud tab --> Profiles
- Create a New Profile --> AppSec Gateway Profile
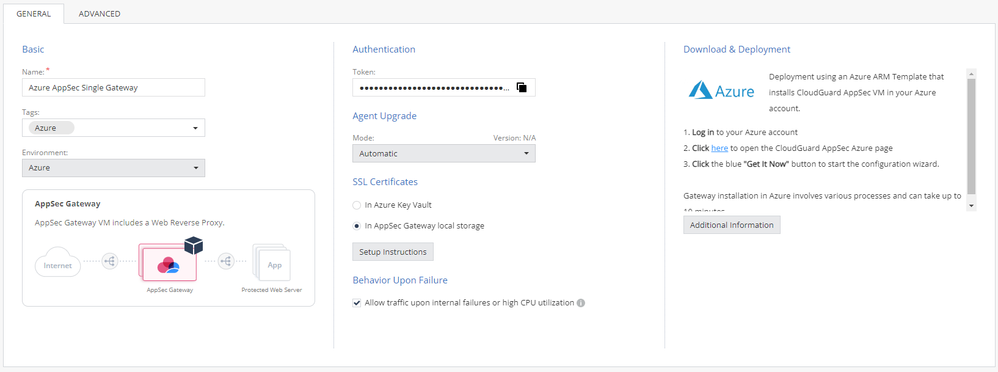
- Type in the Basics: Name, Tags (Optional), and Environment (In our case, choose Azure)
- Adjust the Authentication part: Under SSL Certificates, choose: In AppSec Gateway local storage
- Copy the token and move on the Azure Portal
Deploy CloudGuard AppSec Gateway on Azure
- Inside Azure Portal, use the top search bar and type: Marketplace
- Inside Azure Marketplace, use the inner search bar and look for: CloudGuard AppSec
- Click on Create --> CloudGuard AppSec Single Gateway
- Now, the deployment wizard is opened, and we need to fill in the information:
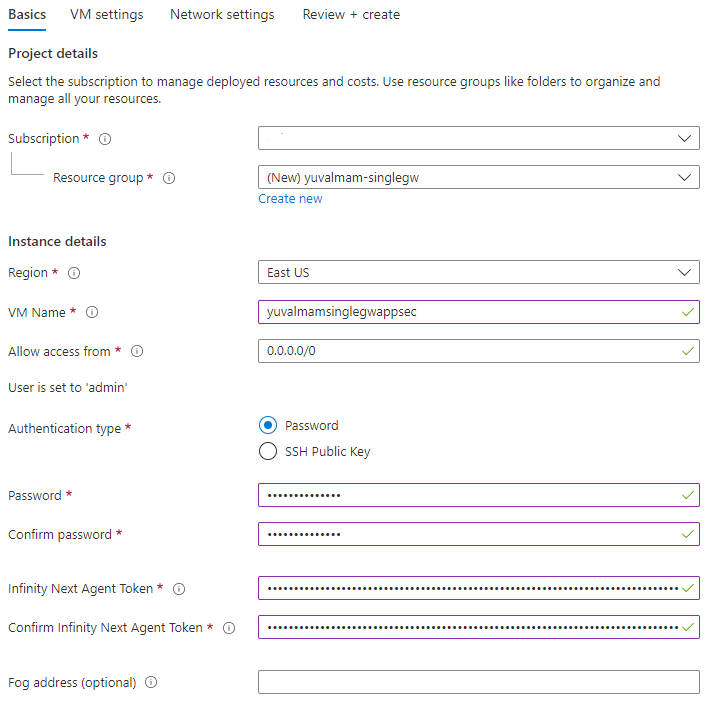
- Basics: Choose the relevant subscription (in the lab it's the default one), resource group (you can use an existing one if it's empty or create a new one), region (you can choose the closest one to you or stay with default - note that the Key Vault should be located within the same region!), choose Scale Set name, leave the allow access from as default, choose a password for the gateway and paste the token you copied from the Profile page. Leave the Fog address empty. Click Next: VM Settings
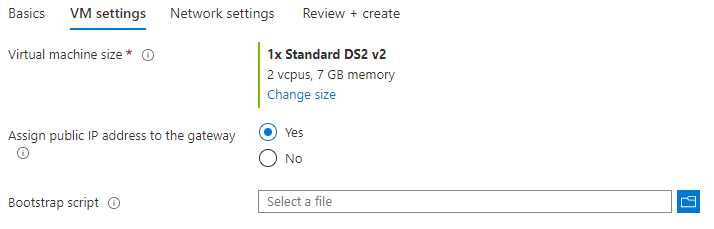
- VM Settings: Basically, we will leave all of this part as default. For those of you who want additional information on this part - At first, you can the virtual machine size. Then, you can choose if you wish to assign public IPs to the gateways (for workshop purposes, leave it on Yes), and you have the load balancer configuration options. Click Next: Network settings.
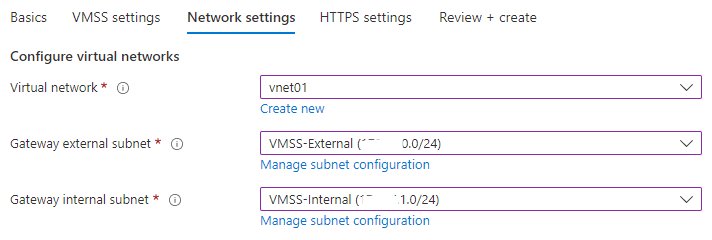
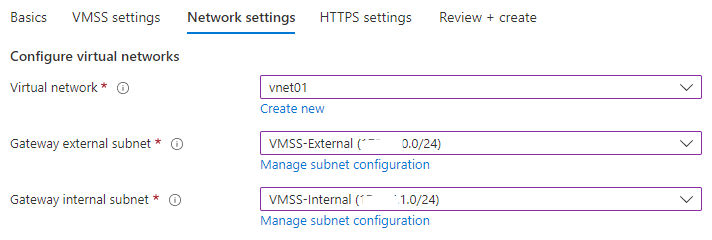
- Network Settings: Here you will need to choose a VNET that AppSec will use. Note that the External Subnet must have a connection to the Internet. Usually, inside the Internal Subnets, we will have our applications.
For this workshop, our applications are from outside of the VNET. Click: Next: Review + Create.
- Once the Validation of the wizard is passed, click on Create
Deploy AppSec VMSS Gateway:
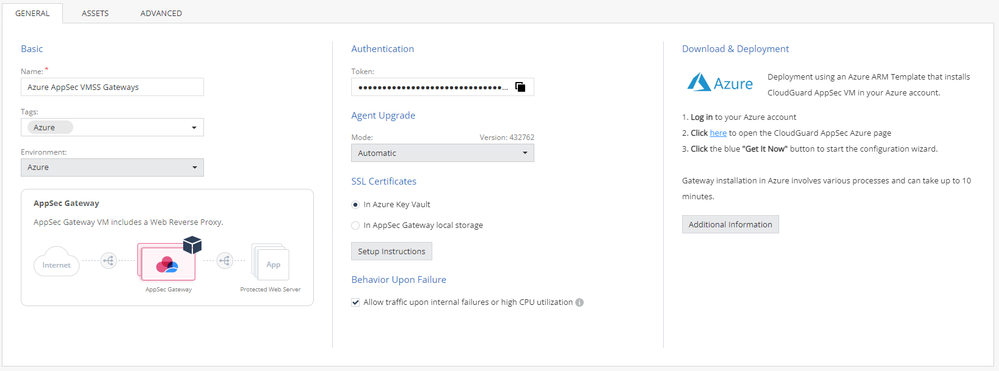
Create a New Profile
- Inside Infinity Portal, click on Cloud tab --> Profiles
- Create a New Profile --> AppSec Gateway Profile
- Type in the Basics: Name, Tags (Optional), and Environment (In our case, choose Azure)
- Adjust the Authentication part: Under SSL Certificates, choose: In Azure Key Vault
- Copy the token and move on the Azure Portal
Deploy CloudGuard AppSec Gateway on Azure
- Inside Azure Portal, use the top search bar and type: Marketplace
- Inside Azure Marketplace, use the inner search bar and look for: CloudGuard AppSec
- Click on Create --> CloudGuard AppSec Gateway: VMSS
- Now, the deployment wizard is opened and we need to fill in the information:
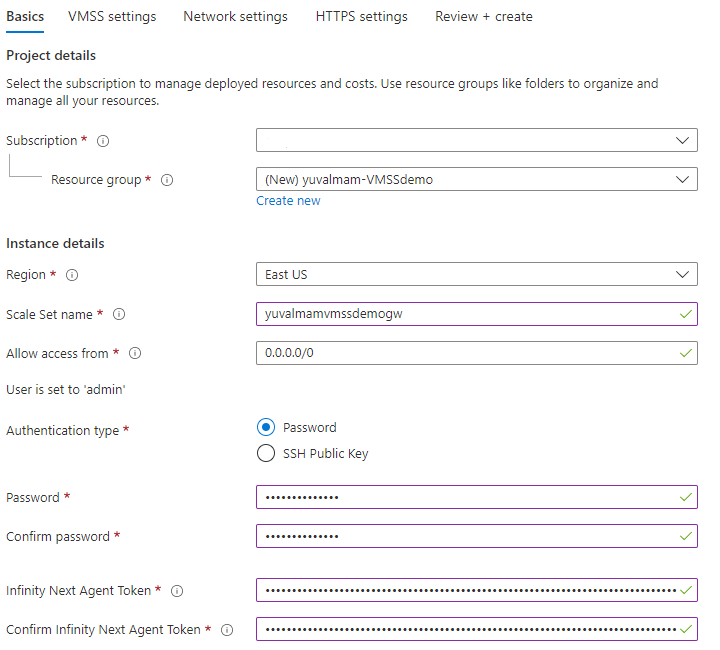
- Basics: Choose the relevant subscription (in the lab it's the default one), resource group (you can use an existing one if it's empty or create a new one), region (you can choose the closest one to you or stay with default - note that the Key Vault should be located within the same region!), choose Scale Set name, leave the allow access from as default, choose a password for the gateway and paste the token you copied from the Profile page. Leave the Fog address and the Administrator email address empty. Click Next: VMSS Settings
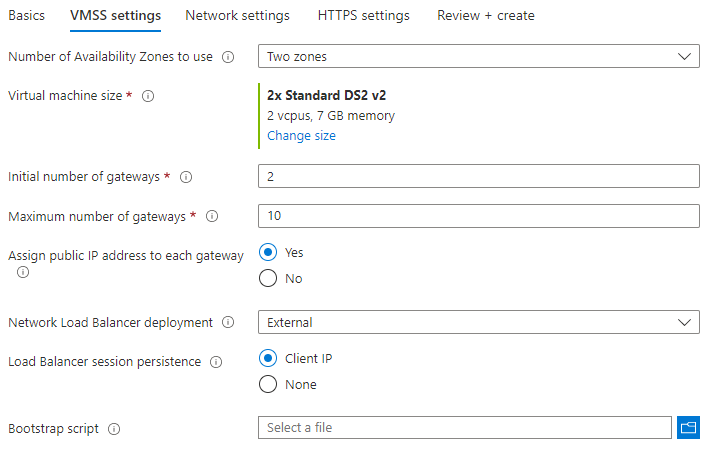
- VMSS Settings: Basically, we will leave all of this part as default. For those of you who want additional information on this part - At first, you can choose the number of availability zone for your VMSS (it depends on the region you chose and on pricing), the number of initial machines, and the maximum number of machines.
Then, you can choose if you wish to assign public IPs to the gateways (for workshop purposes, leave it on Yes), and you have the load balancer configuration options. Click Next: Network settings. - Network Settings: Here you will need to choose a VNET that AppSec will use. Note that the External Subnet must have a connection to the Internet. Usually, inside the Internal Subnets, we will have our applications.
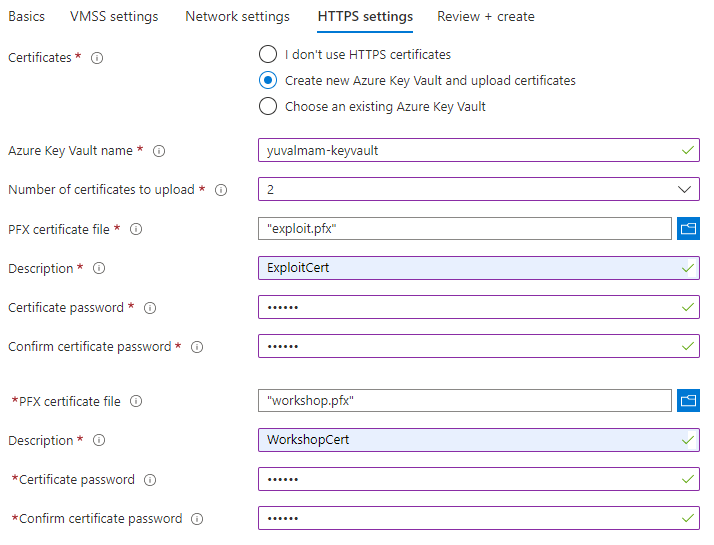
For this workshop, our applications are from outside of the VNET. Click: Next: HTTPS Settings - HTTPS Settings: In this part, we can choose whether we want to use HTTPS traffic in AppSec for our assets, and if we do - we need to use Azure Key Vault. I can choose to use an existing Key Vault or create a new one.
For this workshop, we will choose: Create a new Azure Key Vault and upload certificates.
First, choose a unique name for the Key Vault and choose 2 as the number of certificates to upload.
The first certificate we will upload is "Exploit.pfx" (located in the Dropbox folder), feel in description and type in the certificate password (located in the "pfx password.txt" file. Then, we will repeat this stage with "Workshop.pfx" certificate. Click Next: Review + Create. - Once the Validation of the wizard is passed, click on Create
- Basics: Choose the relevant subscription (in the lab it's the default one), resource group (you can use an existing one if it's empty or create a new one), region (you can choose the closest one to you or stay with default - note that the Key Vault should be located within the same region!), choose Scale Set name, leave the allow access from as default, choose a password for the gateway and paste the token you copied from the Profile page. Leave the Fog address and the Administrator email address empty. Click Next: VMSS Settings
Create the Assets on Infinity Portal
Do this part twice - one for Exploit and one for Workshop.
- Click on Cloud tab --> Assets
- Create New asset --> Web Application
- Follow the wizard and complete the information:
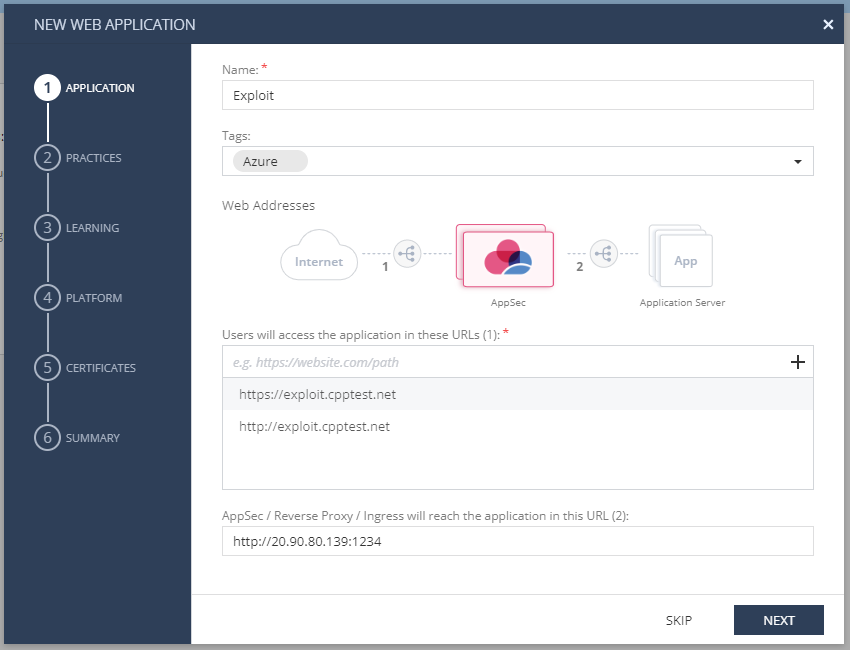
- Application: Type in the asset name, add tags (optional), add the web application URLs (for Exploit: http://exploit.cpptest.net, https://exploit.cpptest.net ; for Workshop: http://workshop.cpptest.net, https://workshop.cpptest.net), and then, add the reverse proxy IP address (The public IP of the webserver hosting the demo sites). Click Next.
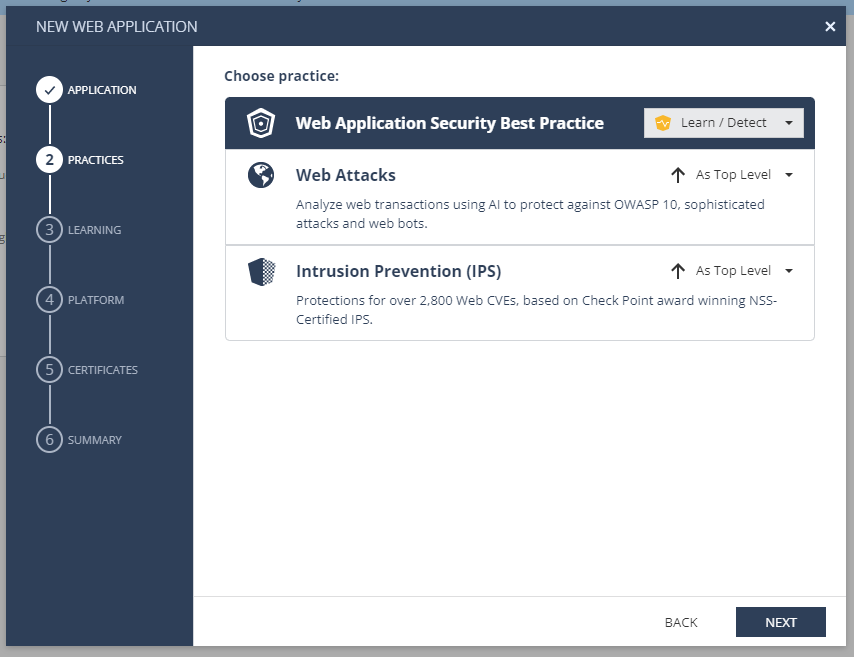
- Practices: In this window, we are able to choose what is the mode that AppSec will be on - Learn / Detect or Prevent.
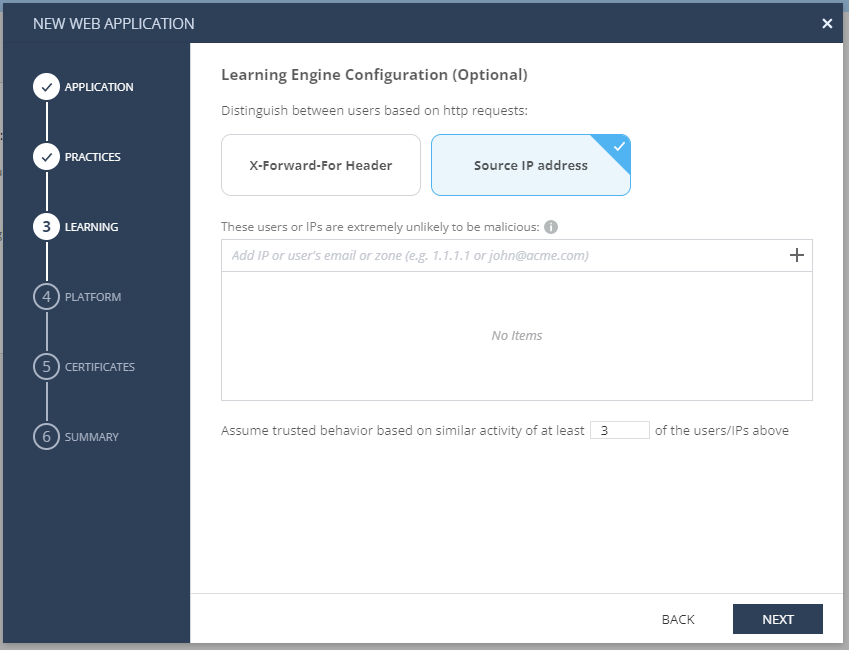
The best practice is to deploy AppSec on Learn / Detect mode for about 2 weeks, in order for the ML to be able to learn properly your assets and avoid false positives. Click Next. - Learning: Here we can choose how we will distinguish between users based on http requests. For the workshop purposes, we will choose: Source IP address. Click Next.
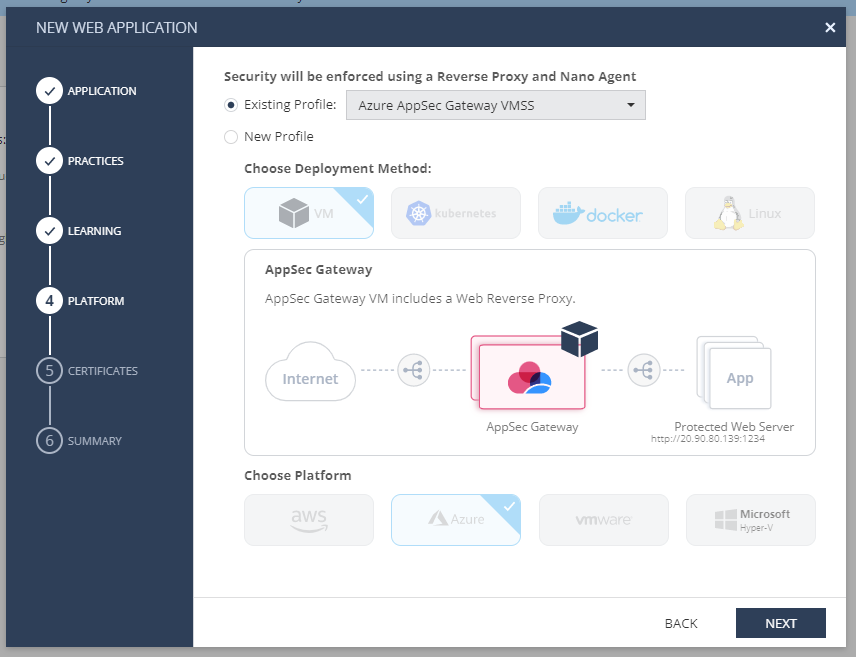
- Platform: Choose Existing Profile --> the Profile that you created in the previous steps. Click Next.
- Certificates: We have already taken care of them. Click Next.
- Summary: Click Done.
- Application: Type in the asset name, add tags (optional), add the web application URLs (for Exploit: http://exploit.cpptest.net, https://exploit.cpptest.net ; for Workshop: http://workshop.cpptest.net, https://workshop.cpptest.net), and then, add the reverse proxy IP address (The public IP of the webserver hosting the demo sites). Click Next.
Surf to your assets via AppSec Single Gateway
- Inside Infinity Portal, click on Cloud tab --> Assets, and choose one of the assets.
- Click on Advanced… --> Check V on: Redirect incoming HTTP requests to the same URL using HTTPS.
- Click Enforce.
- Change your HOST file in your machine (location: \windows\system32\drivers\etc\hosts) to point exploit.cpptest.net and workshop.cpptest.net to your AppSec VM public IP on Azure (you can find it by searching “Virtual Machines” on Azure Portal).
- Use Cert-Verify tool to create .pkg files from the certificates (guide here). Connect using SSH to the AppSec machine (username: admin, password: as you chose on the deployment wizard) and place both of the files under /etc/certs. In case certs folder is not exists, create it under /etc.
- Surf the websites via browser and play with Exploit and Workshop.
Surf to your assets via AppSec VMSS Gateways
- Inside Infinity Portal, click on Cloud tab --> Assets, and choose one of the assets.
- Replace the Profiles to the VMSS profile.
- Click Enforce.
- Change your HOST file in your machine (location: \windows\system32\drivers\etc\hosts) to point exploit.cpptest.net and workshop.cpptest.net to your Load balancer’s public IP on Azure (you can find it by searching “Load Balancers” on Azure Portal and then click on “Front End Public IP”).
- Surf the websites via browser and play with Exploit and Workshop.
That’s it!
You have implemented both CloudGuard AppSec as a Single Gateway and as a VMSS gateway.
You created and protected 2 websites and surf them through AppSec inspections.
Now, you can explore the Monitor tab and see the traffic and the security events founded.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great Work!!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Yuvalmamka,
Any chance that the files from this Dropbox folder could be made available again?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @yuvalmamka
Thanks for sharing this. Can you also share the same for an onprem deployment in an KVM Virtualization environement?
Thanks for your support.
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is exactly what I was hoping for.
May I ask if you've already implemented it? and if so, could you please share any key considerations or lessons learned when deploying on a KVM platform?
Additionally, is there any feature in KVM that functions similarly to Azure VMSS (Virtual Machine Scale Set) in terms of scalability and Load Balancer?
Your insights would be extremely helpful to us.
Thanks & Best Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
We don't have a dedicated image for a KVM platform. Still, you can use our single-container deployment, which brings the functionality of the CloudGuard WAG agent and a managed NGINX environment, just like the AWS/Azure/VMWare deployments, as a "gateway".
Find more information here: Single Docker | CloudGuard WAF